Local Exchange without SMG
Introduction
Configuring a local Exchange server without SMG (Secure Mail Gateway) can easily fail. For this reason, we have identified common causes and recorded appropriate solutions. To check basic connectivity, there are four steps to perform.
Logfile analysis
Here you need the log from the reverse proxy (e.g. nginx) for further analysis
on Linux the log is located in the following directory
/var/log/nginx/relution_access.logfor Windows e.g. in your nGinx installation path
/nGinx/logs/relution_access.log
If the mails are retrieved on the end device, the log should contain a reference to the following URL
/Microsoft-Server-ActiveSync
If the entry /Microsoft-Server-ActiveSync is left behind the connection works.
Troubleshooting
If nothing is entered in the log, the URL must be entered in the browser whether it is generally accessible.
https://myexchange.com/Microsoft-Server-ActiveSync
If the URL is called, an entry must be left in the nginx log.
- If no entry is generated, the infrastructure must be checked.
- If the entry can be found, probably the settings of the Exchange configuration in the Relution policy are not set correctly or are invalid.
Checking the connection
A curl command can be used to check the connection from Relution to the Exchange server:
curl https://outlook.XXX.de/Microsoft-Server-ActiveSync --user Our-Exchange-host\\Exchangeuser@Domain.de:ExchangePWvomUser --verbose --http1.1 -i
You might get an output with a certificate error as shown:
Trying 172.16.105.109:443....
Connected to outlook.XXX.de (172.000.000.000) port 443 (#0)
schannel: disabled automatic use of client certificate
ALPN: offers http/1.1
schannel: SEC_E_UNTRUSTED_ROOT (0x80090325) - *The certificate chain was issued by an untrusted certificate authority.
Closing connection 0
curl: (60) schannel: SEC_E_UNTRUSTED_ROOT (0x80090325) - *The certificate chain was issued by an untrusted certificate authority.
More details here: https://curl.se/docs/sslcerts.html
If the error message is displayed as above, the CA’s certificate is not stored in the server’s operating system, so depending on the operating system, the certificate must be installed accordingly.
Example for Relution in Docker →
Read out HTTPS communication
In Springboot Admin you can check the HTTPS communication between Relution and the Exchange and read it in the logfile.
org.apache.http.wire : DEBUG
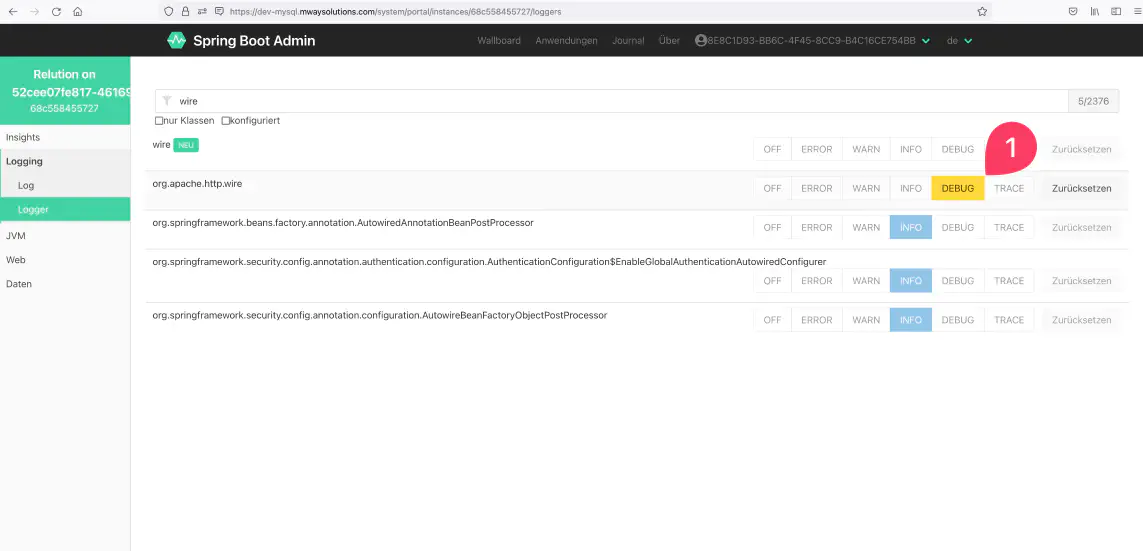 A communication must be triggered by the device to fill the log with hints about the cause.
The log level must be set back to
A communication must be triggered by the device to fill the log with hints about the cause.
The log level must be set back to INFO after the analysis.
Evaluate log
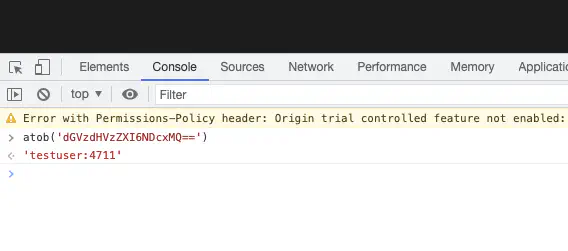
Subsequently, the increased log level can be searched for conspicuous clues. For example, if the user and user credentials are not correct, the login fails and a 401 Unauthorized message is entered, which may look like this in basic Auth: dGVzdHVzZXI6NDcxMQ==
This can be decoded in the browser console to compare the transmitted password and the user
atob('dGVzdHVzZXI6NDcxMQ==')
SMG is not functional with Outlook365, Microsoft has deactivated Basic Auth for this and is using OAuth2 Deprication of Basic Auth →