Multi-factor authentication
Introduction
Multi-factor authentication, or MFA for short, is a security mechanism that requires users to provide at least two independent verification factors to uniquely identify themselves when accessing an application.
Unauthorized access is not possible due to the additional authentication method; the security level is thus significantly increased.
MFA and Relution
Relution enables LDAP and local users to activate the additional authentication methods Email Token and Authenticator App in the Relution Portal in addition to specifying user name and password.
With the release 5.16, the requirement of the German Federal Office for Security (BSI) for MDM providers to implement the provision of an additional security level is taken into account.
How is the MFA configured in Relution?
The new MFA feature must be enabled by an organization or systemadmin under Settings → Password Policies before it can be used.
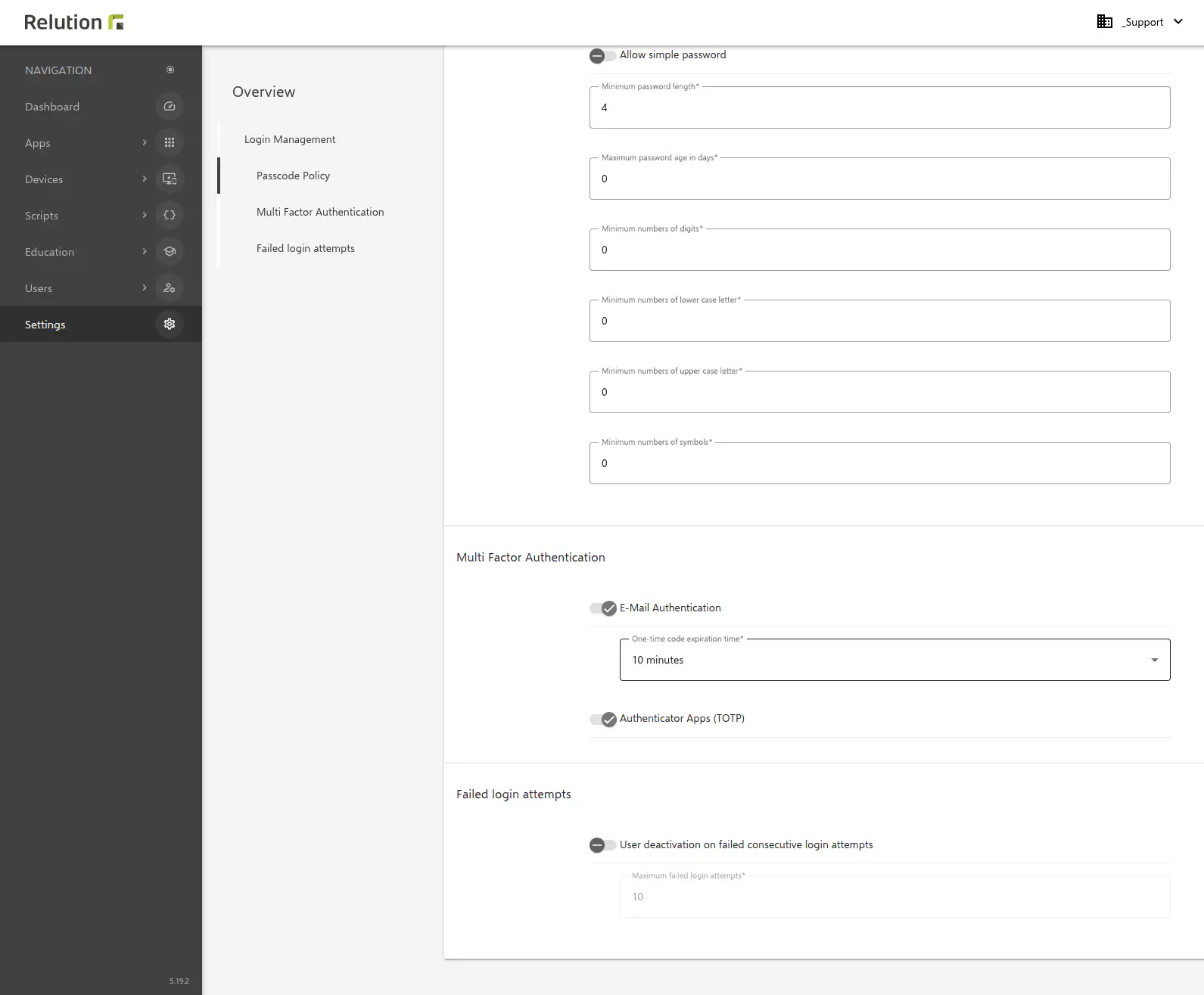
In the submenu item Multi-Factor Authentication either Email Authentication can be selected and the validity period of the one-time code to be sent can be determined or the option Authenticator Apps can be selected. Alternatively, both variants can be activated in parallel.
Force MFA log in
The Relution Permission system has been extended with the possibility of multi-factor authentication. It is possible to define for a role whether MFA log in is required or not.
If the permission/role with activated MFA login is assigned to a user or a group, an MFA login is mandatory when logging in.
If no MFA method has been set up yet, then the user must do this at the first log in.
Multi-factor authentication methods
E-mail token
Each user, independent of an administrator, has the possibility to activate MFA individually in the Relution Portal. In the menu bar Profile selected, new tokens for two-factor authentication can be added under MFA Tokens. If the first option E-mail is selected, a new tab opens afterwards to add the e-mail address.
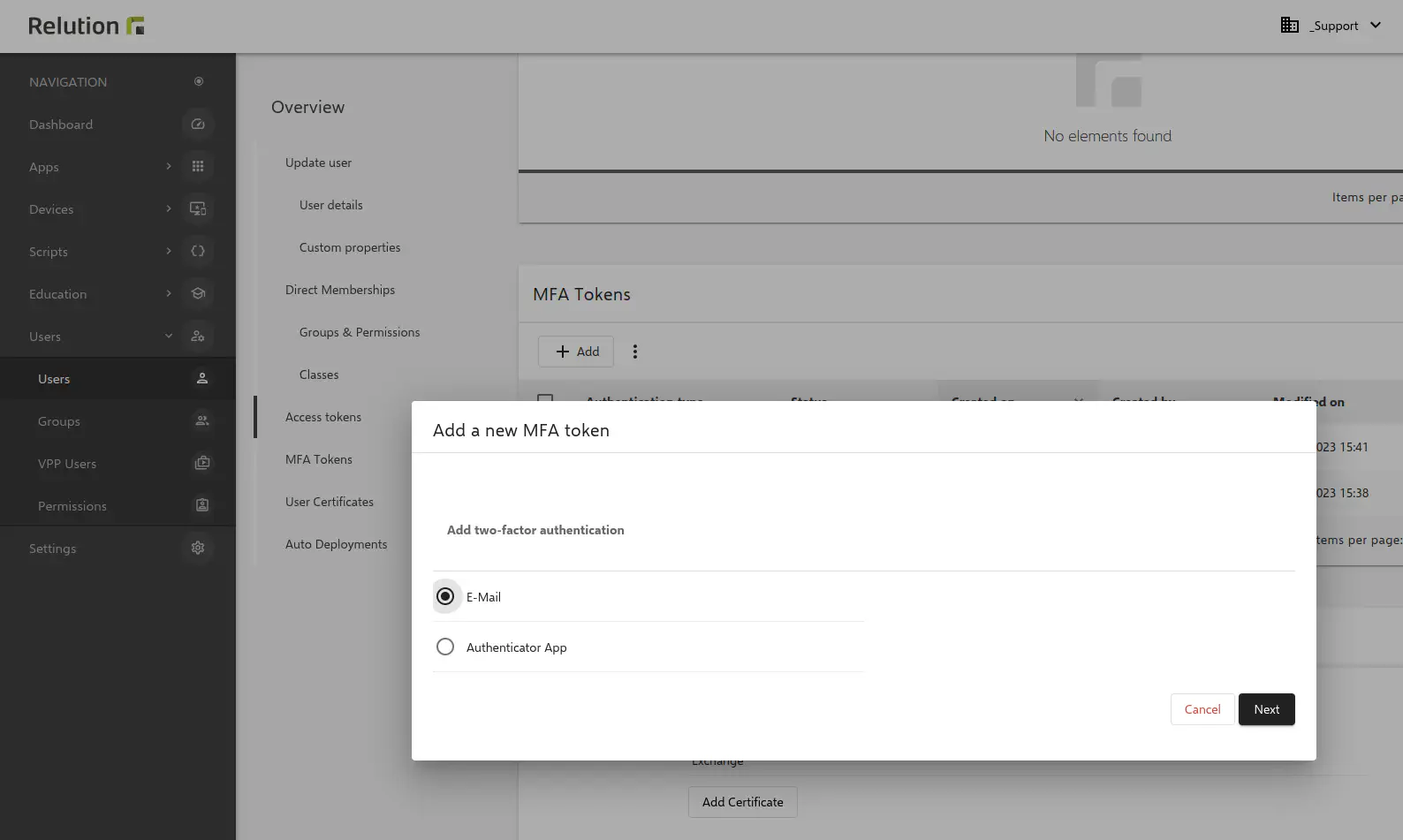
Private as well as user different e-mail addresses can be stored in the system - useful in the school context.
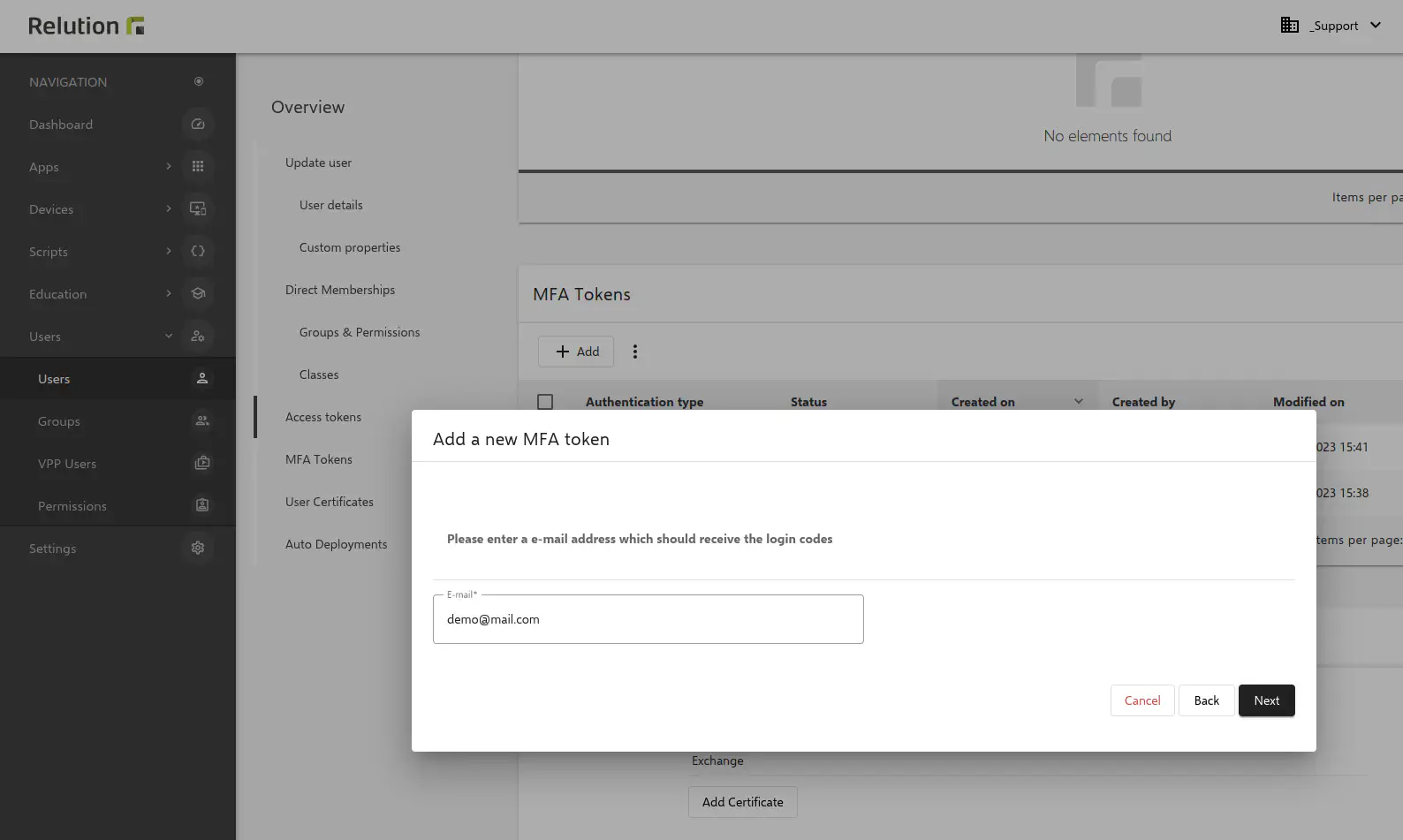
After entering a one-time code for verification will be sent to the stored email address. This code is valid for the time period defined by the administrator. As soon as the correct pin, consisting of any numeric number combination, is entered, the multi-factor authentication is configured.
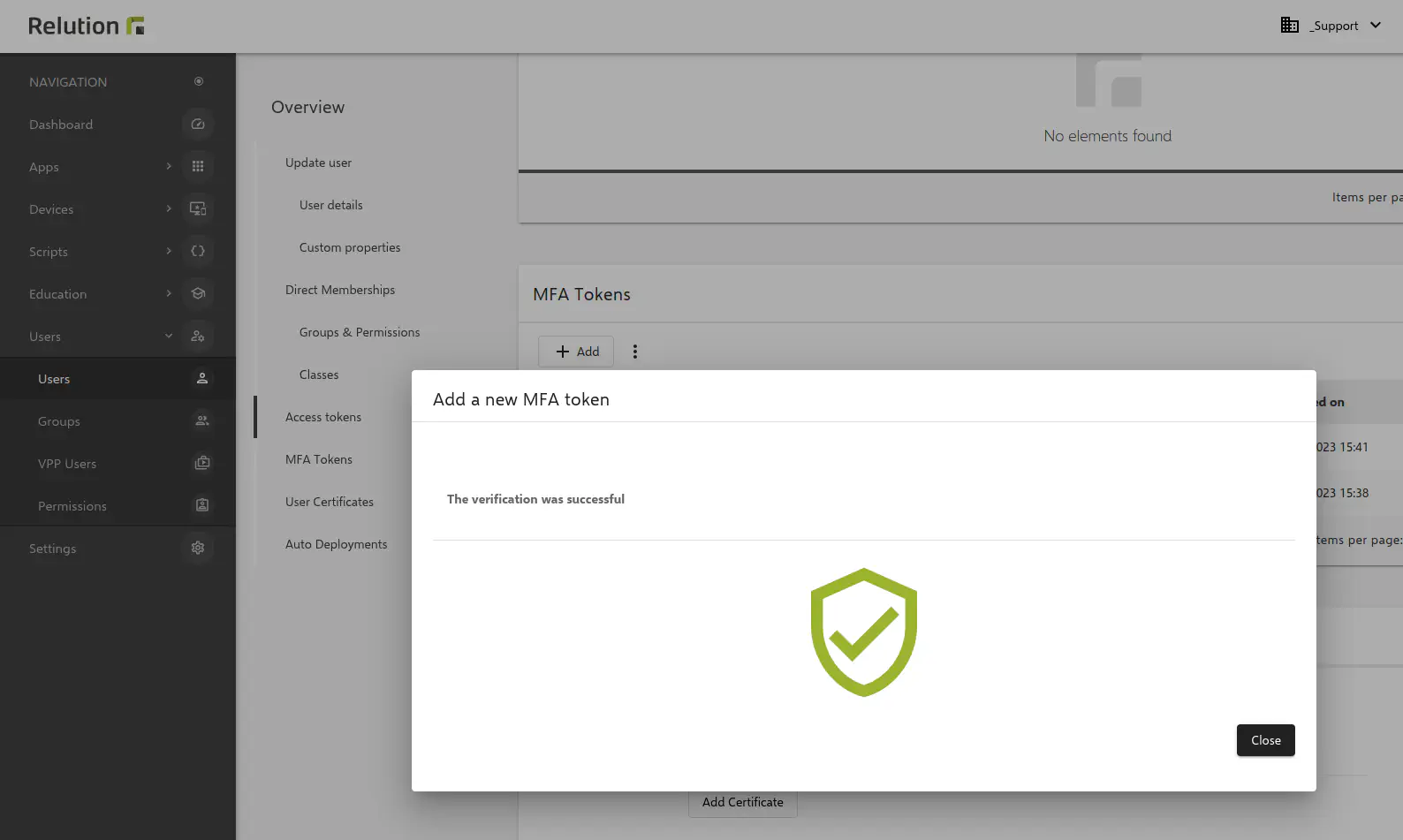
Any number of MFA factors can be stored in the Relution Portal. In addition to the e-mail variant, the use of various Authenticator Apps is supported.
If the second variant Authenticator App is selected in the menu bar Profile as a new MFA token, a new window opens with a QR code that has to be scanned with the authentication app previously installed on the end device.
It is also possible to use a setup key for verification.
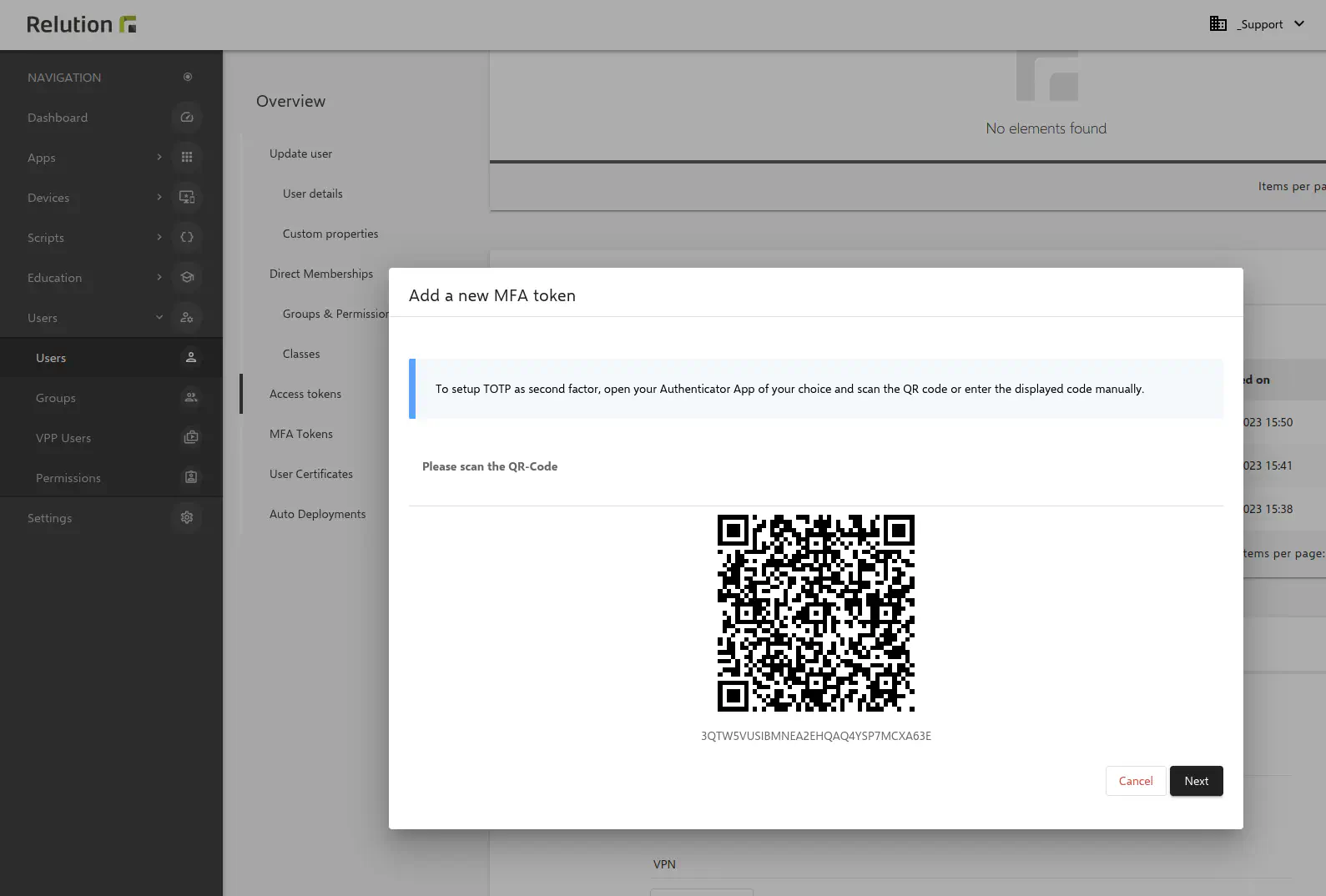
If various Authenticator apps are in use on multiple devices at the same time, the validity of at least one app is checked for a correct login. When using both multi-factor authentication methods, the Authenticator app is primarily queried; the stored email variant serves as a backup.
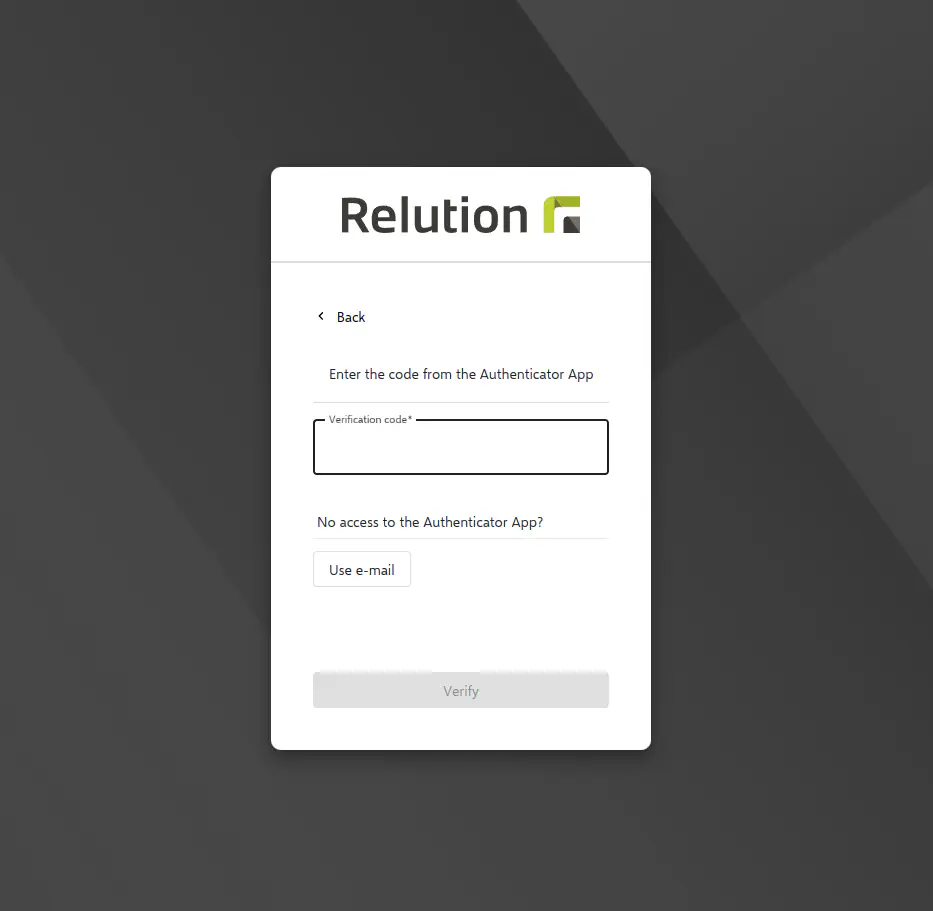
If only the Authenticator app is in use, there is no email fallback.
Delete MFA tokens manually
MFA tokens can be deleted manually by the user in the Profile menu bar under the MFA tokens menu item.
If all MFA variants have been removed manually, but the application has been forced by the administrator, multi-factor authentication must be stored again the next time the user logs in to the Relution Portal.
What happens if the MFA is lost?
If the user does not have access to email and/or Authenticator app while the MFA is activated, logging into the Relution Portal is no longer possible - going to the Administrator is mandatory.
Under Users → Users, the Administrator has the option to manually remove the blocked MFA token.