Setup Intune Policies
Overview
This guide explains how to configure and testConditional Access Policies in Microsoft Intune.
These policies define how access is granted or denied for users based on the compliance state of their devices.
For more information, read the official Microsoft Conditional Access documentation.
Misconfigured Conditional Access policies can unintentionally block users from signing in. Relution is not liable for any damages resulting from improper configuration. Targeting
all cloud appsin thetarget resourceswith strict policies will also block users from registering their devices.
Recommendations from Relution
To ensure a smooth rollout, Relutionrecommends the following:
- to start with, either
- use the “report-only” mode to simulate policy effects before enforcement
- OR apply the policy to a limited group of test users
- never select
All cloud appsin thetarget resources. SelectingAll cloud appswith strict policies will block users from being able to register their device. As of today, theMicrosoft Broker appcan’t be selected in theexcludefilter, which always needs to be enabled.- A good starting point is to target Office 365.
Example Policy Setup
Policies can be configured in Intune > Endpoint security > Conditional Access > Policies.
See the following screenshot as example:
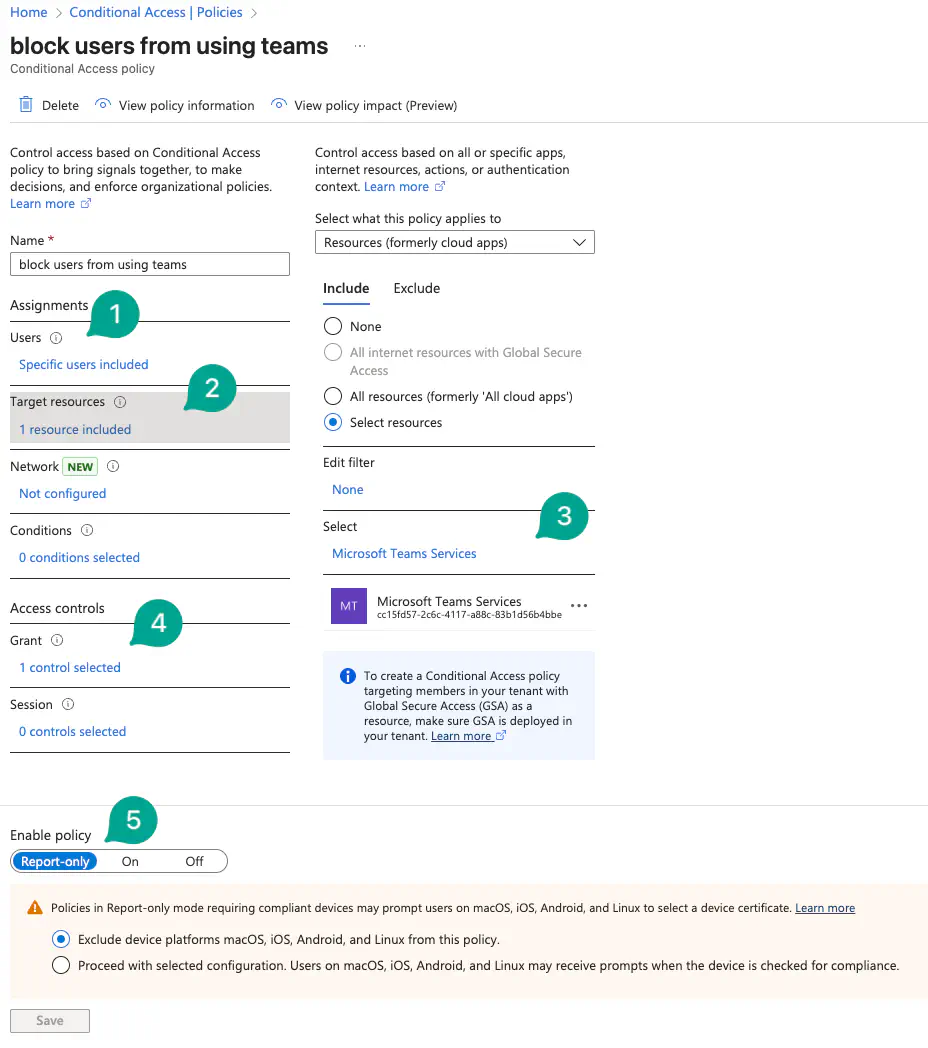
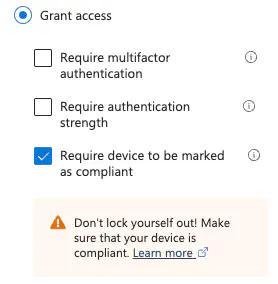
Example configuration:
- Select the users the policy should apply to.
- Select the target ressources.
- In this example, we selected Microsoft Teams
- As a grant, we decided that devices have to be compliant
- Set the policy mode to
Report-Onlyfor initial testing.
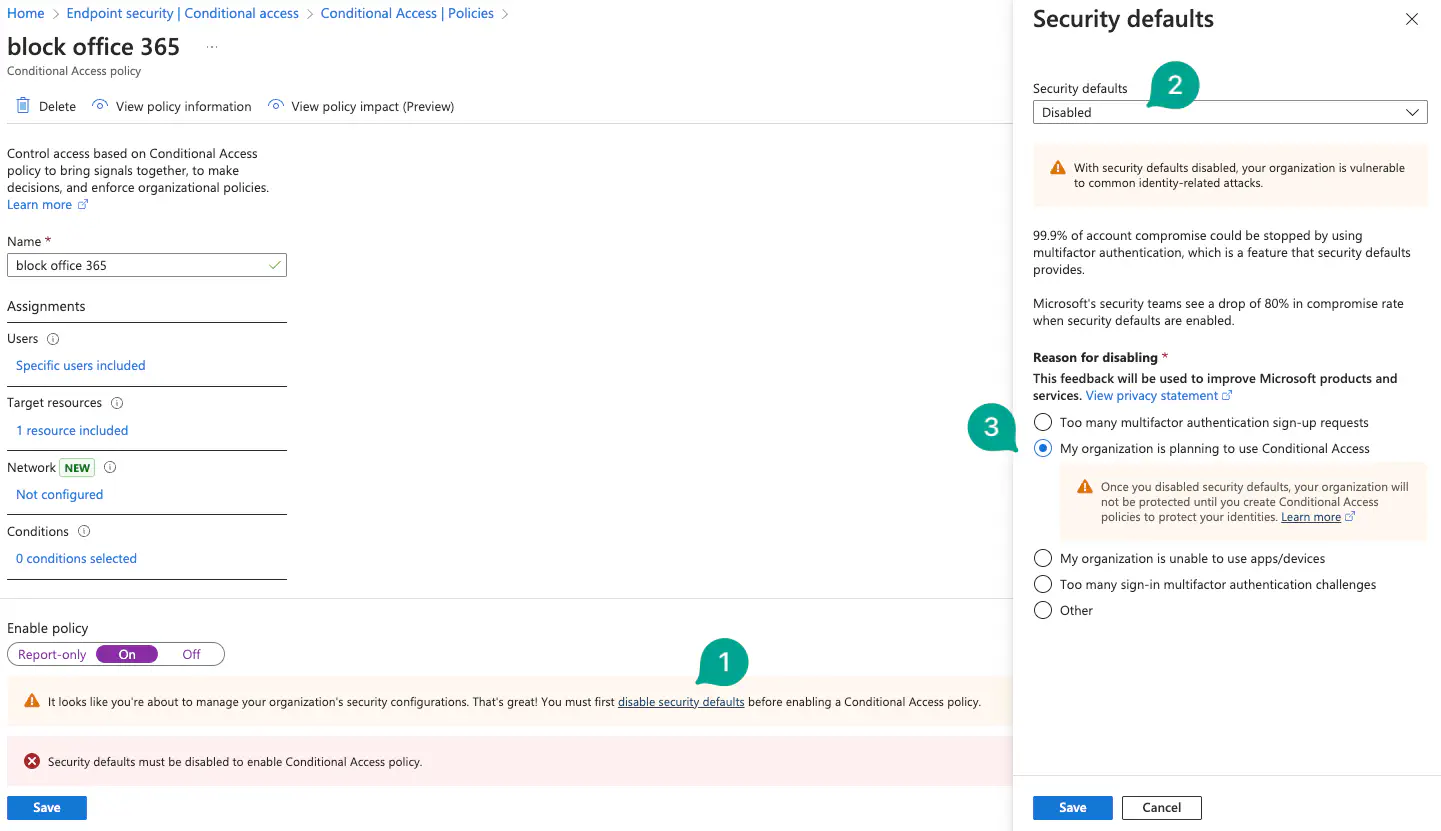
Disable Security Defaults
If you receive an error about security defaults, you must disable them before Conditional Access policies can be used. More information can be found in the Microsoft documentation on security defaults.
If you’re sure to disable them, you can click on disable security defaults, select disabled and My organization is planning to use conditional access.
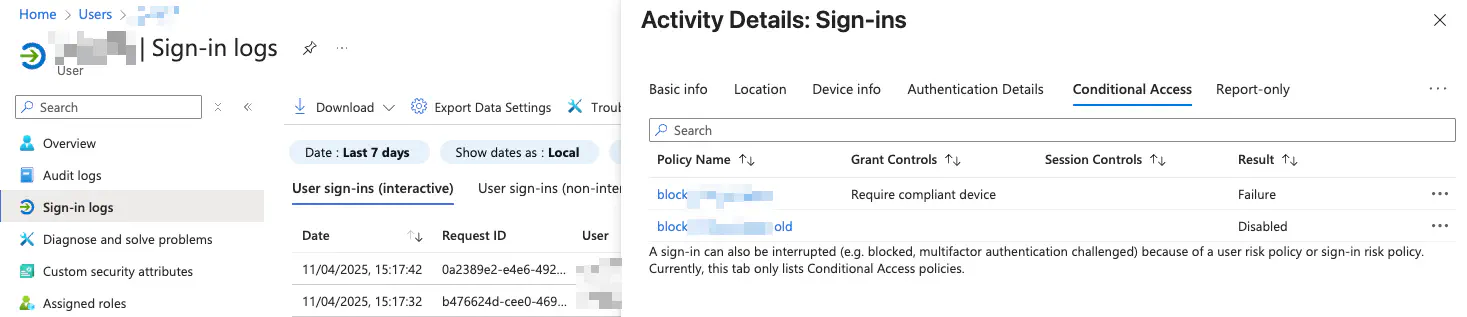
Debugging and Policy Evaluation
To verify whether a policy has been applied successfully:
- Go to the
Sign-in logsview inEntra IDorIntune. TheConditional Accesstab shows applied or evaluated policies.
Additionally, Microsoft offers a What If tool.