OIDC with Workspace
Introduction
OpenID Connect OIDC is an identity protocol built on top of OAuth 2.0 that enables secure authentication and authorization for web and mobile applications. It allows users to log in securely to various services while service providers can simultaneously access verified identity information.
This guide explains the step-by-step configuration of OIDC in Relution using Google Workspace as an example.
Project and Client Setup (Google Cloud Console)
First, an application must be registered in the Google Cloud Console to obtain the necessary credentials.
Log in at console.cloud.google.com.
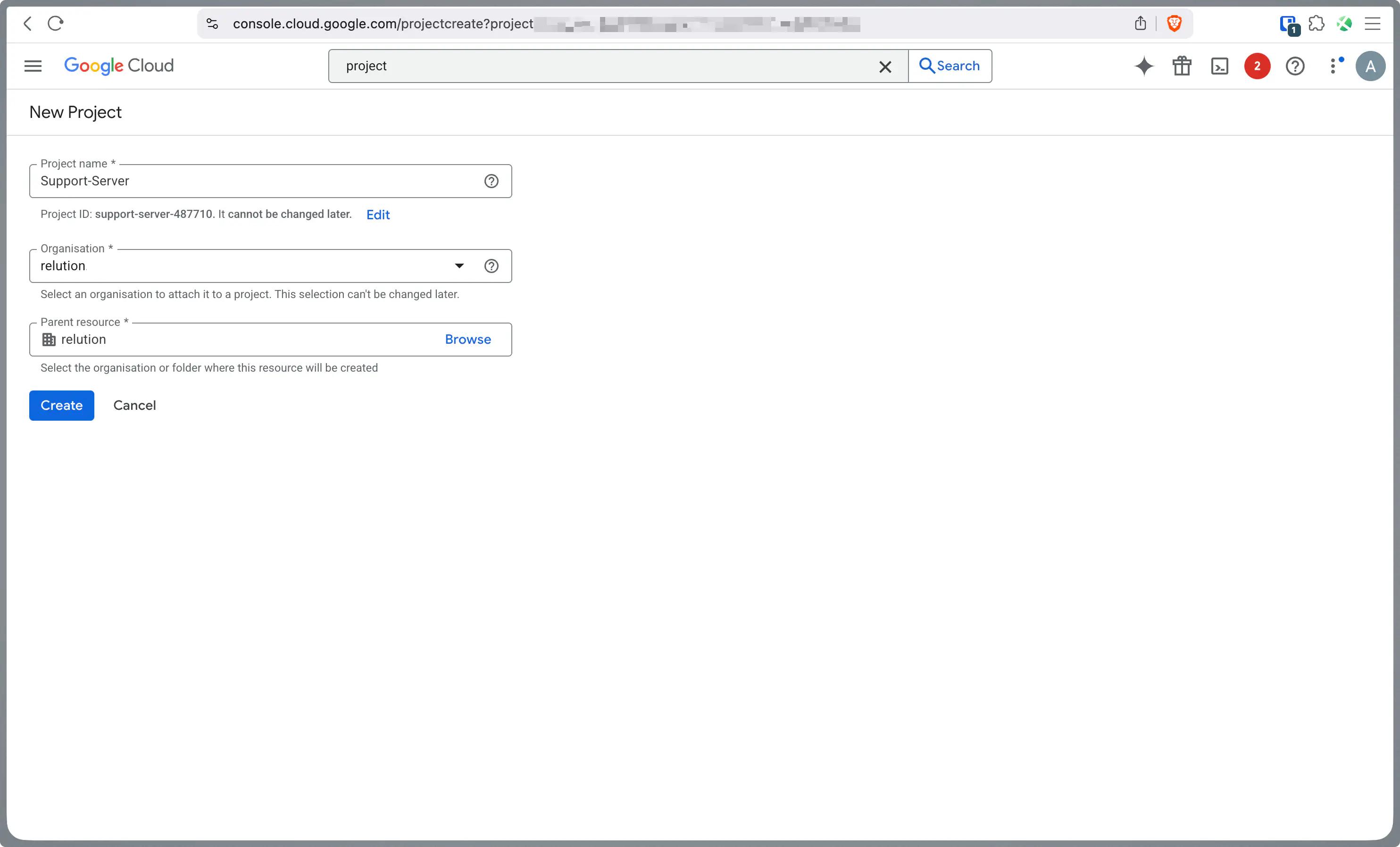
Create a new project or select an existing one.
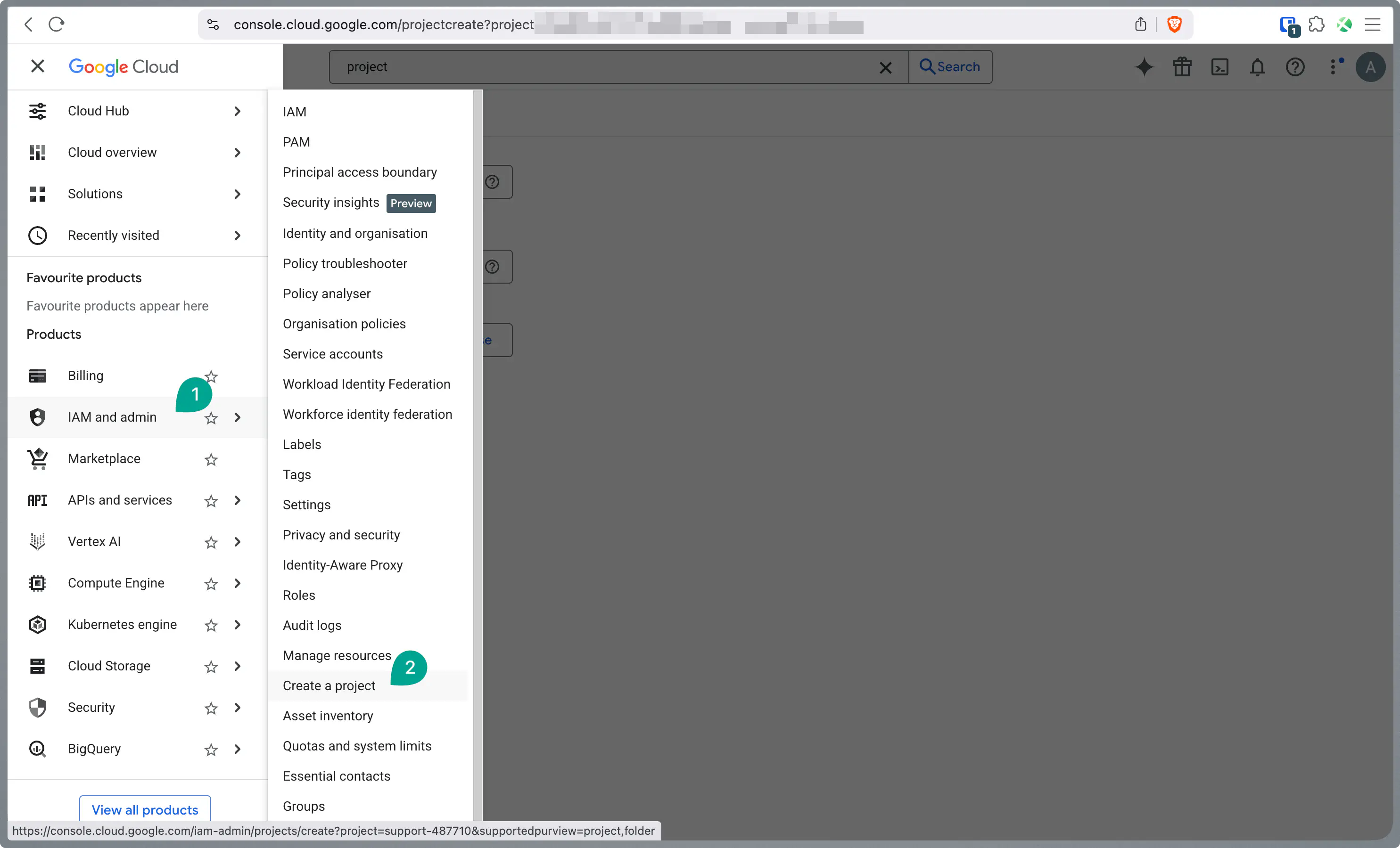
In the navigation menu, go to APIs & Services > OAuth consent screen and configure it if necessary.
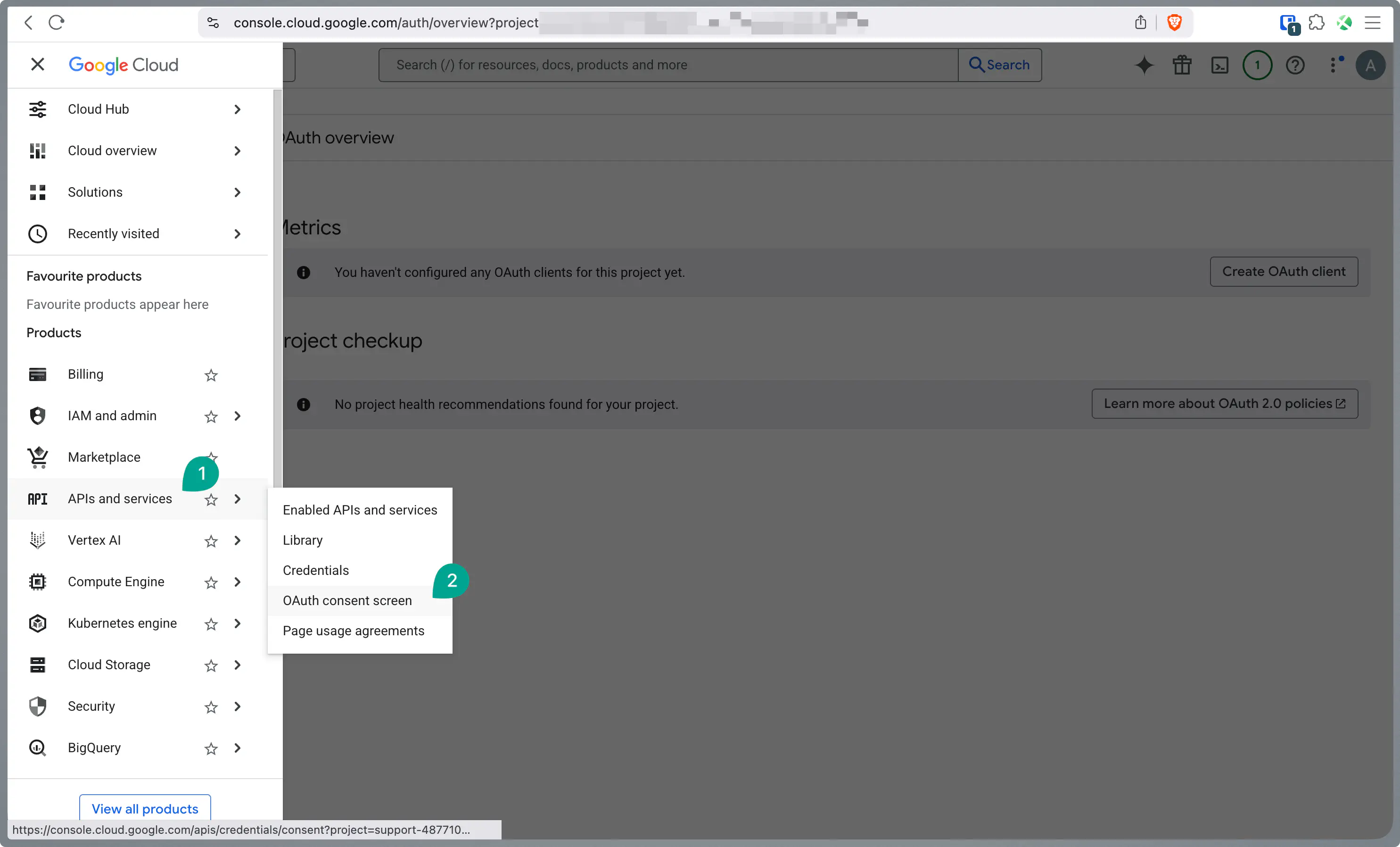
Navigate to Credentials, click the Create Credentials button, and select OAuth client ID.
For Application type, select
Web application.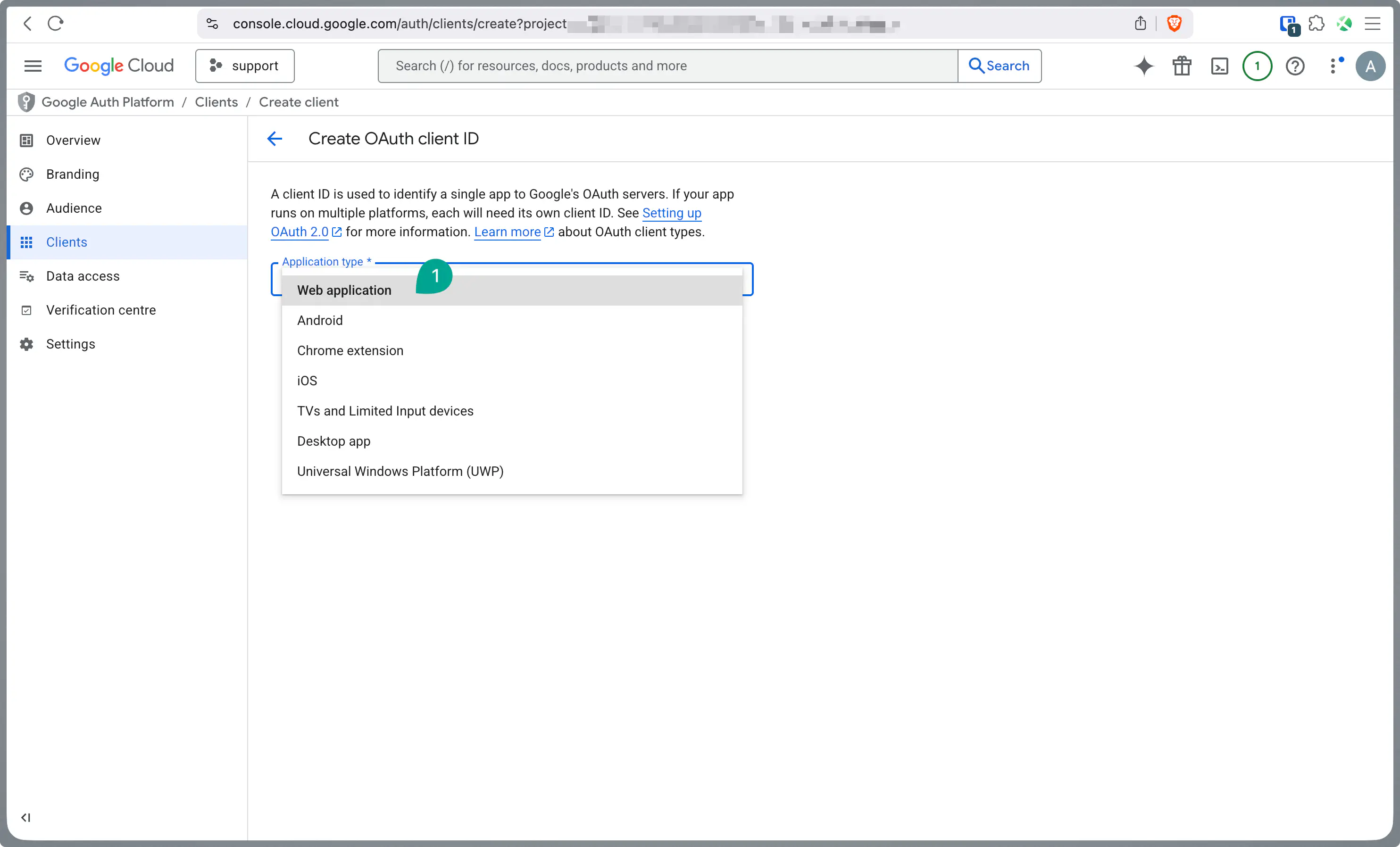
Under Authorized JavaScript origins, enter your server URL (e.g.,
https://support.relution.io). Note: Leave the Authorized redirect URIs field open for now; it will be updated later with specific data from Relution.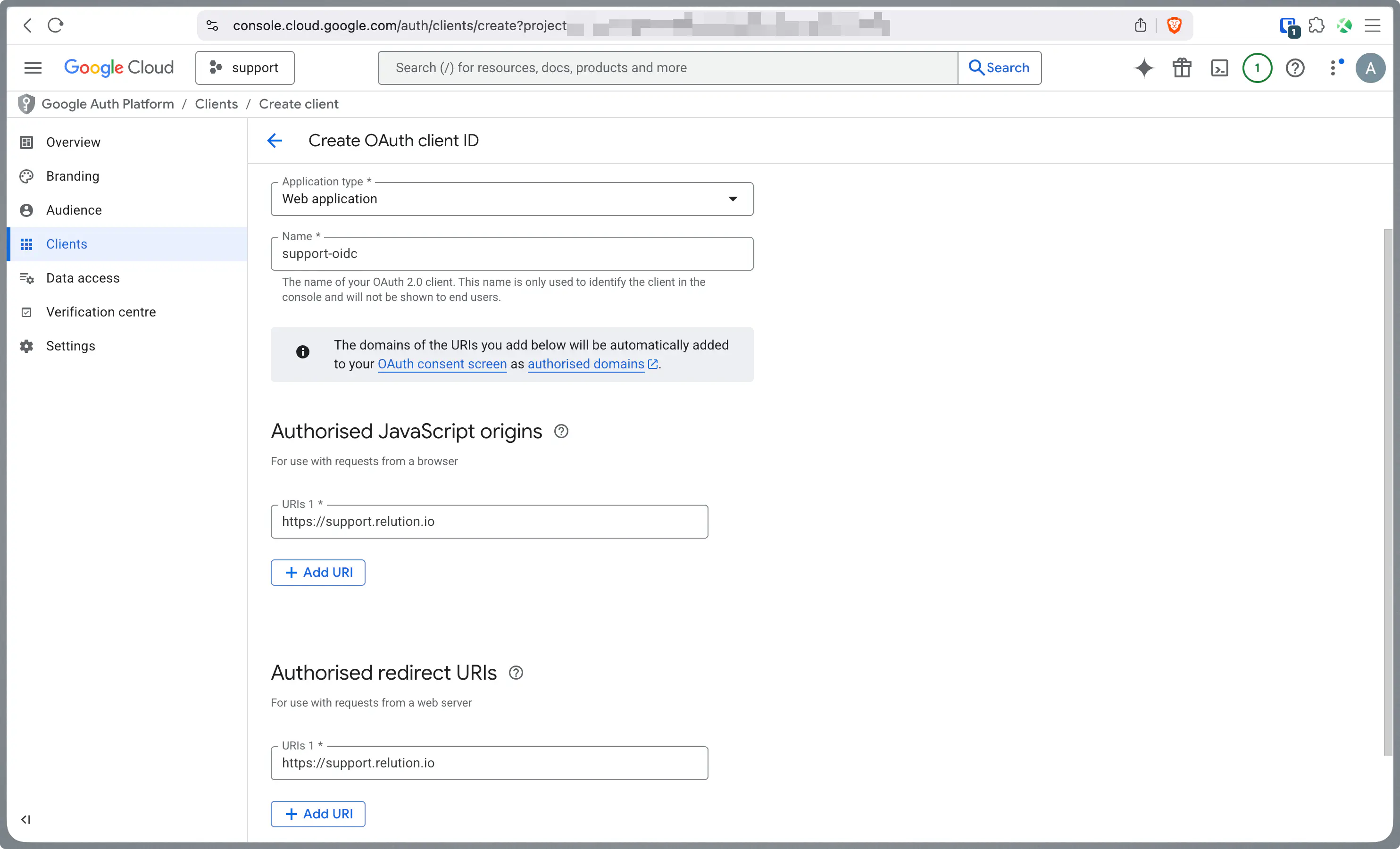
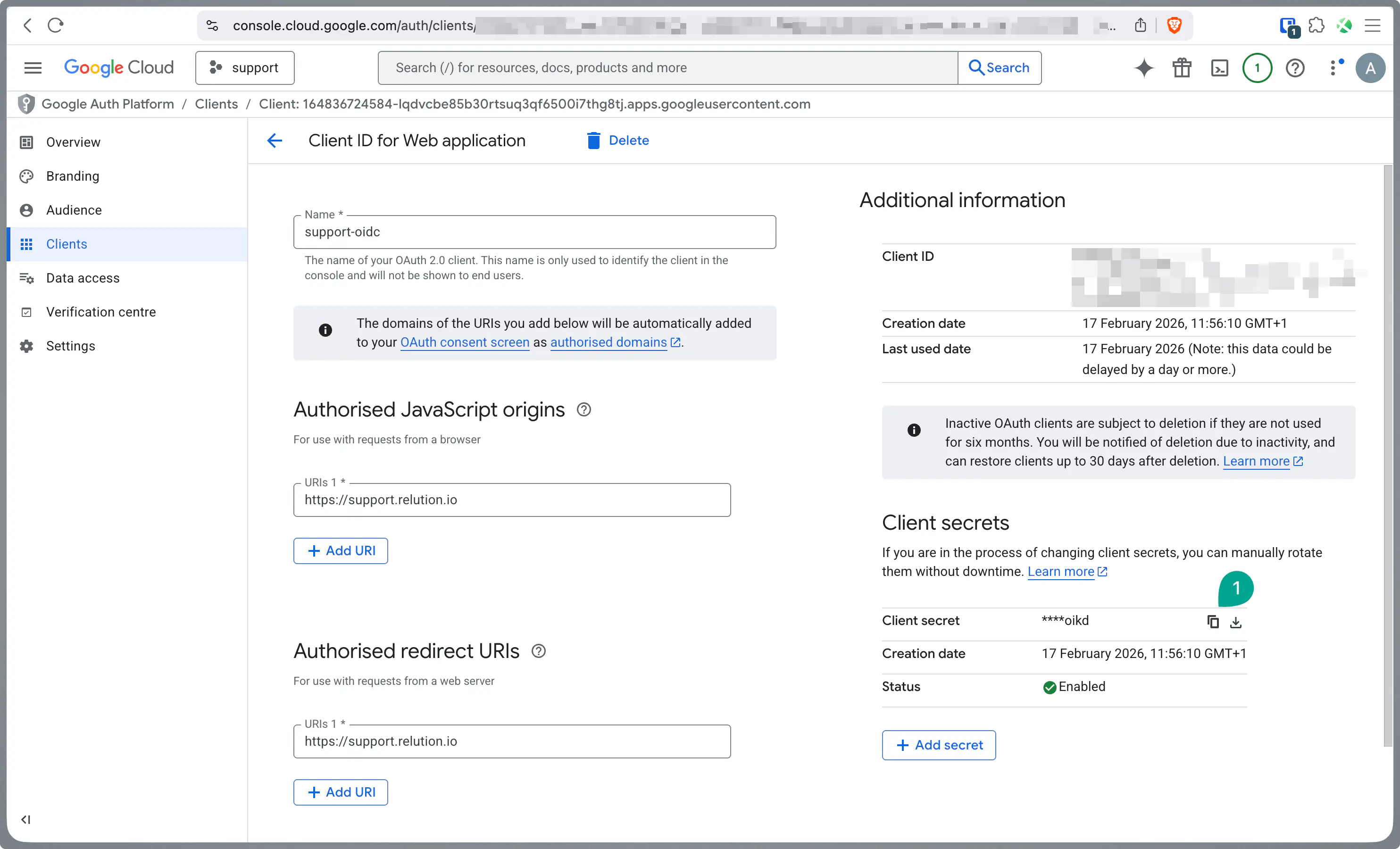
Copy the Client ID displayed after saving.
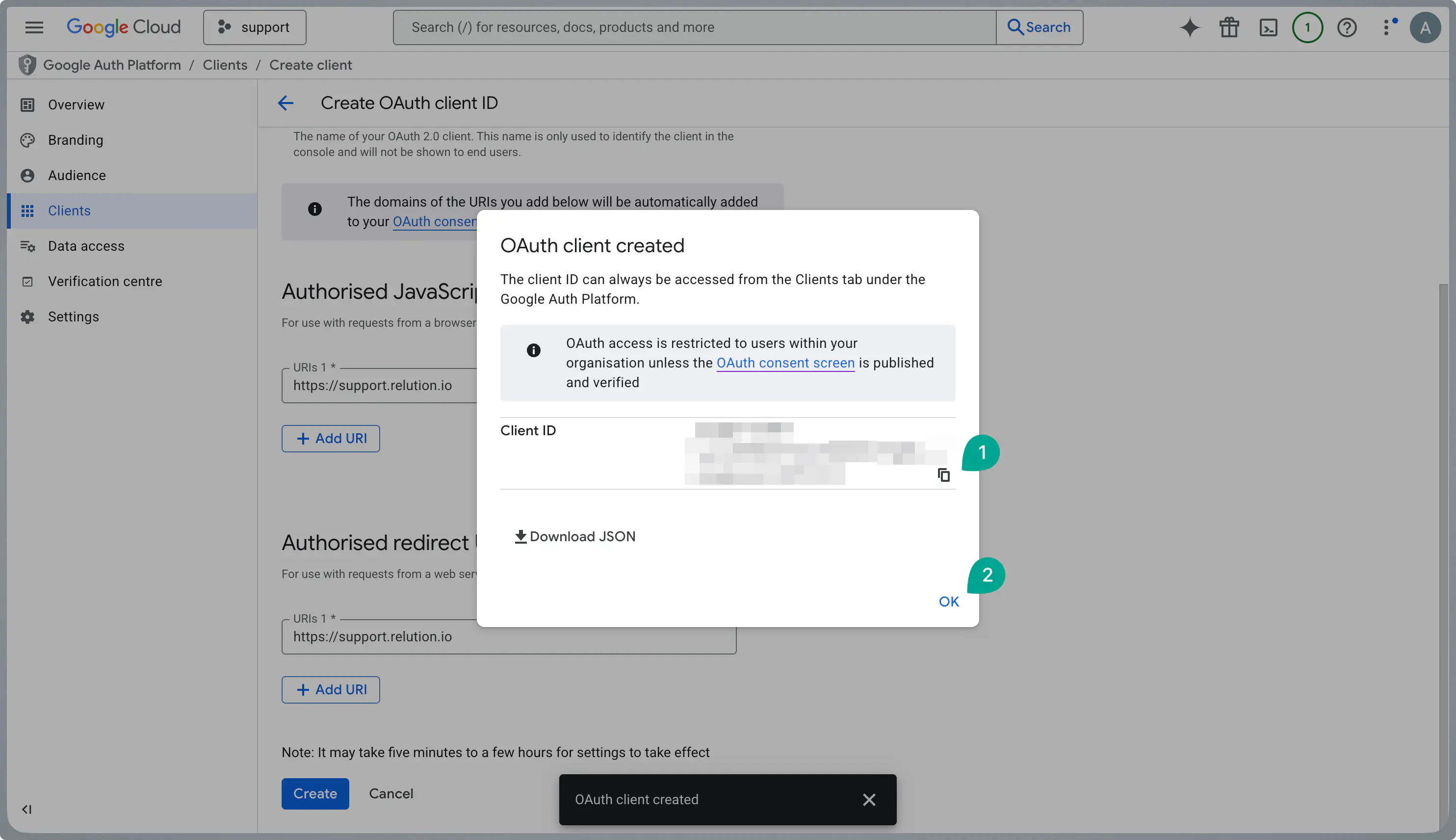
Edit your newly created client to view the details.
Copy the Client Secret. Keep both the ID and Secret secure for later use in Relution.
SSO Setup (Google Admin Console)
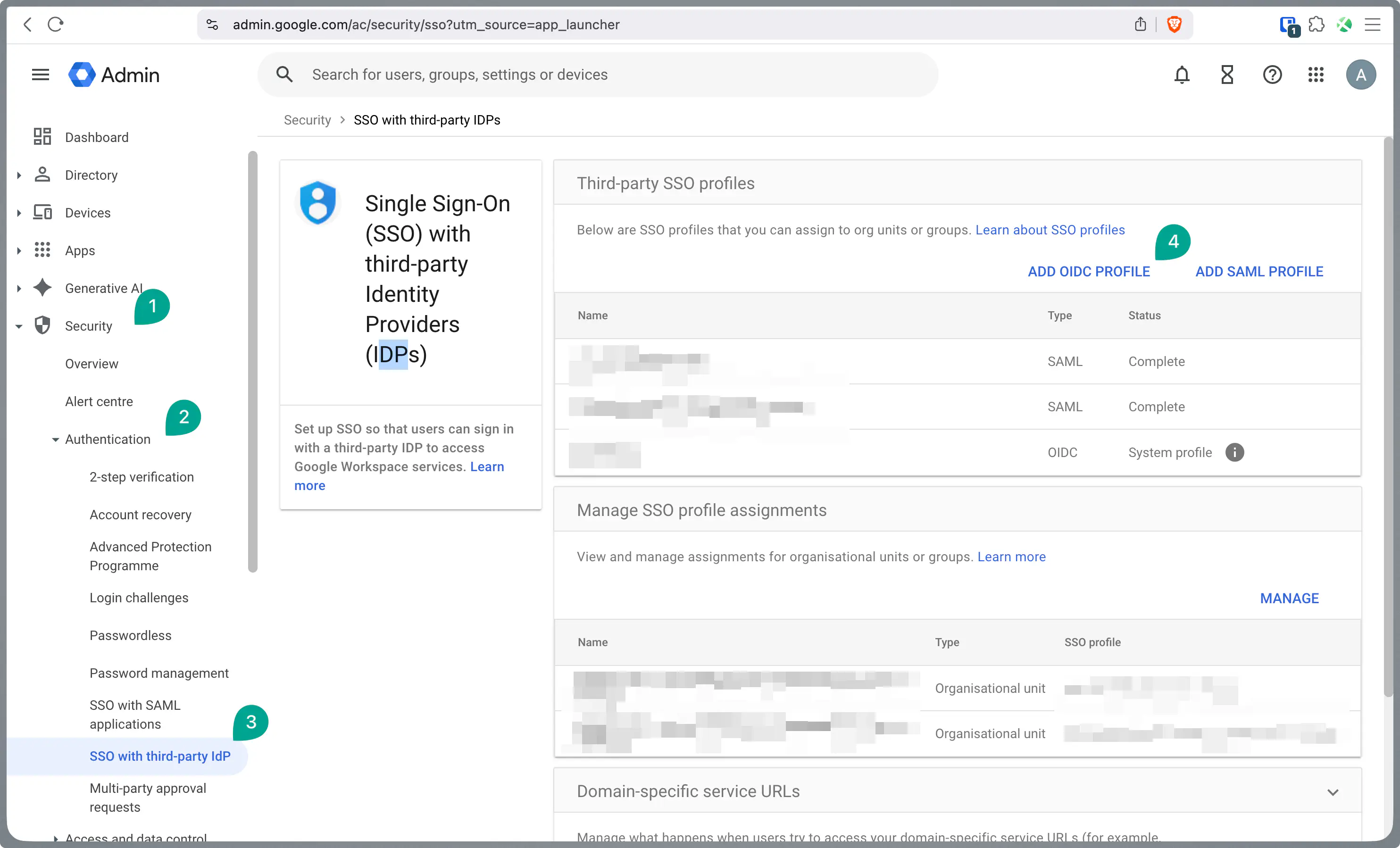
In parallel, the Single Sign-On (SSO) profile must be stored in the Google Admin Console.
Navigate to admin.google.com.
Create a new OIDC profile under Security > Authentication > SSO with third-party IdP.
Enter the Client ID and Client Secret obtained in the previous steps.
- For the Issuer URL and Change password URL, use your Relution server URL (e.g.,
https://support.relution.io).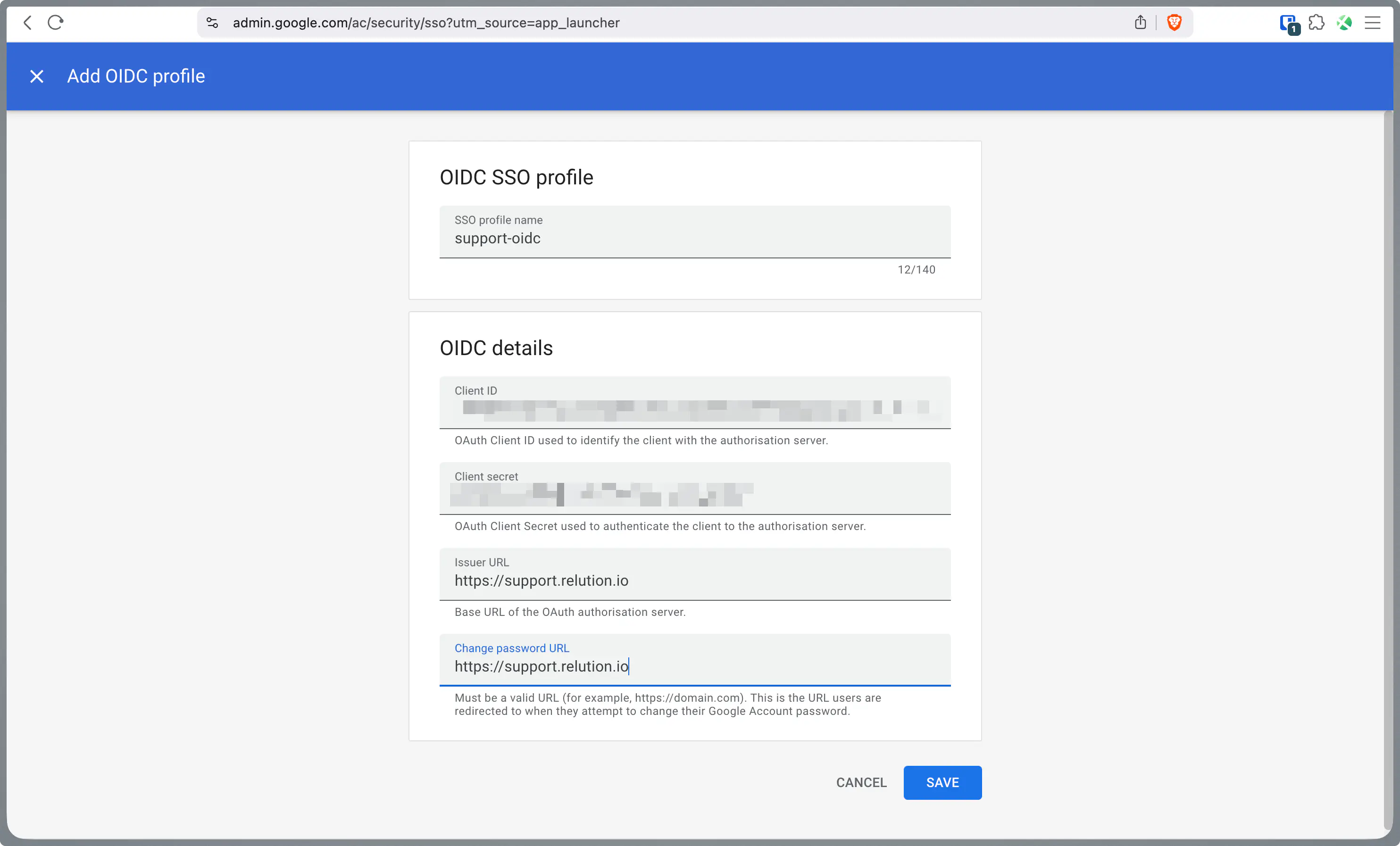
- For the Issuer URL and Change password URL, use your Relution server URL (e.g.,
OIDC Configuration in Relution
Now, the collected data is entered into Relution to establish the connection with Google.
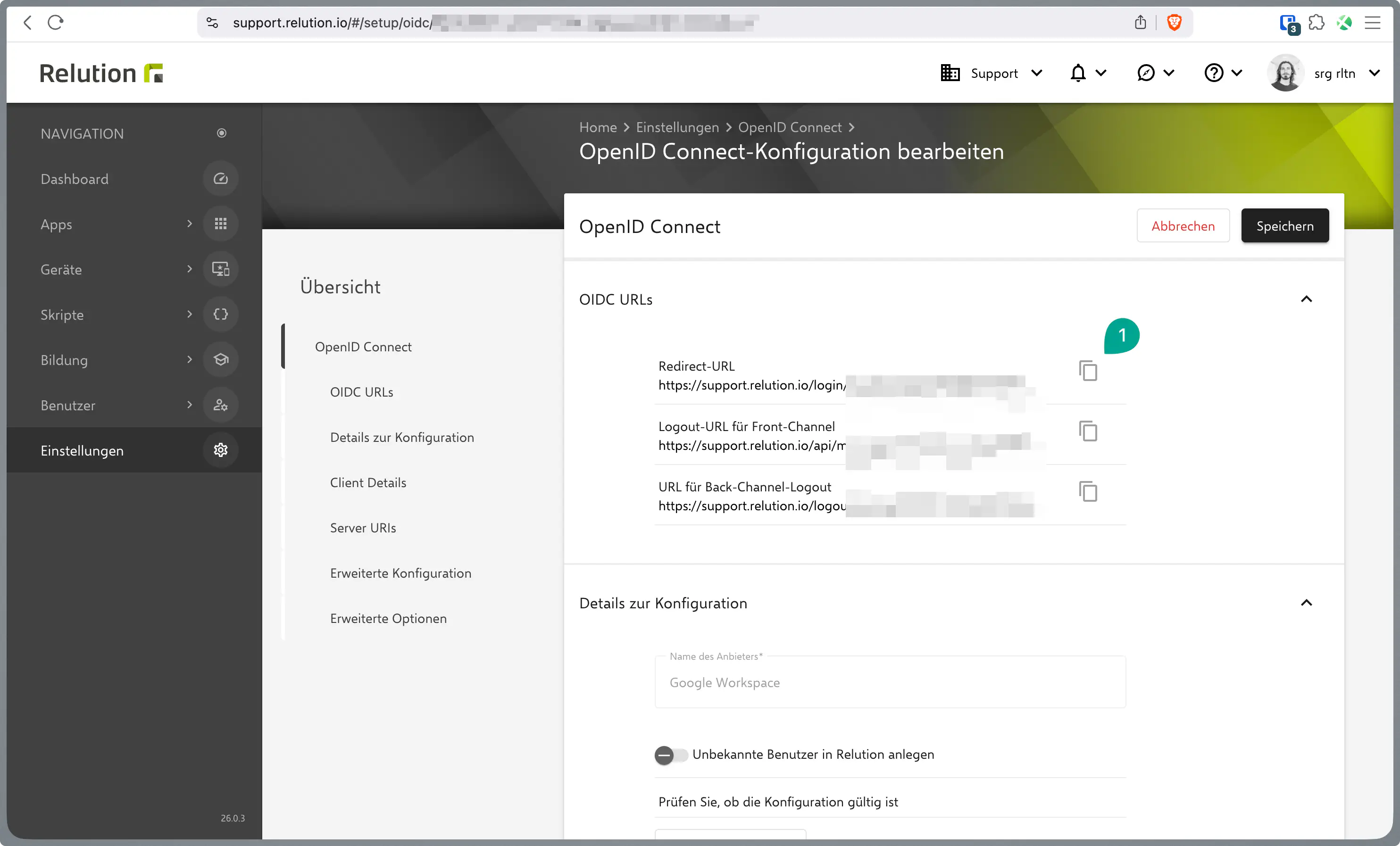
Open the OIDC settings in Relution under Settings → OpenID Connect.
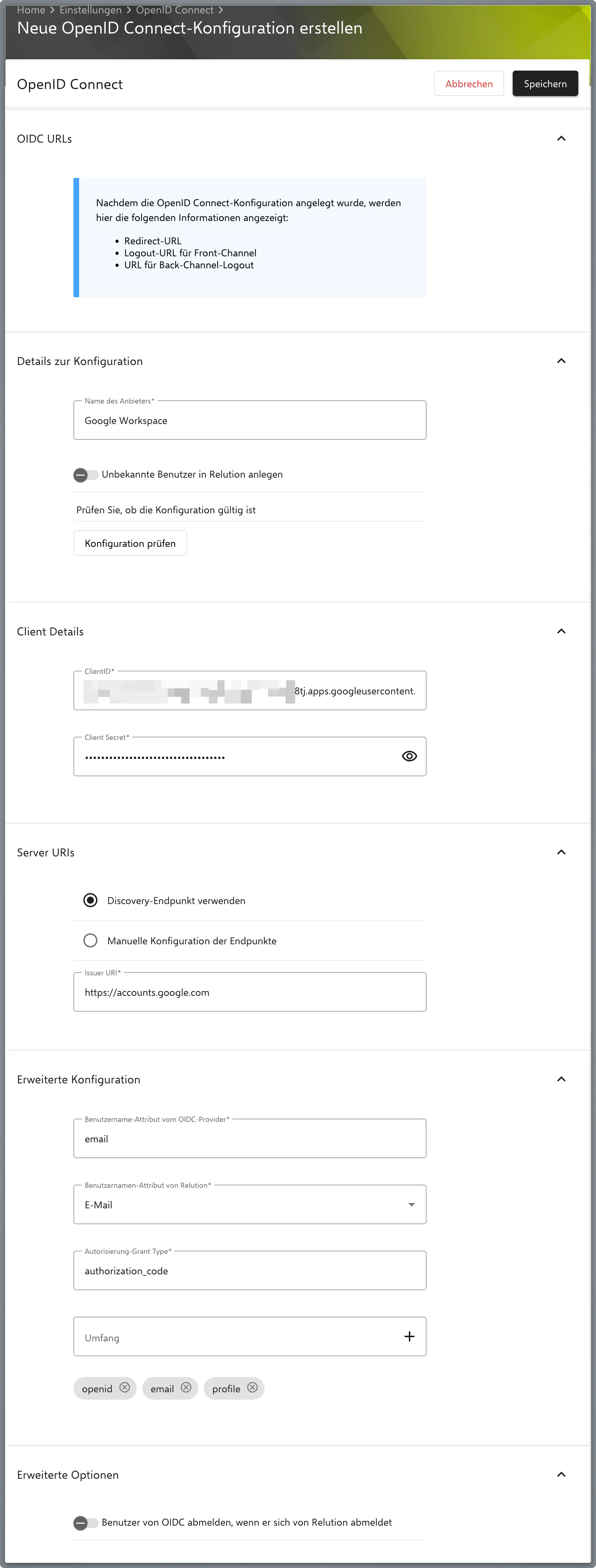
Re-enter the Client ID and Client Secret here.
Under Server URIs > Discovery Endpoint, you must use
https://accounts.google.com.Save the configuration and then open it again to see the generated fields.
Copy the Redirect URL provided by Relution.
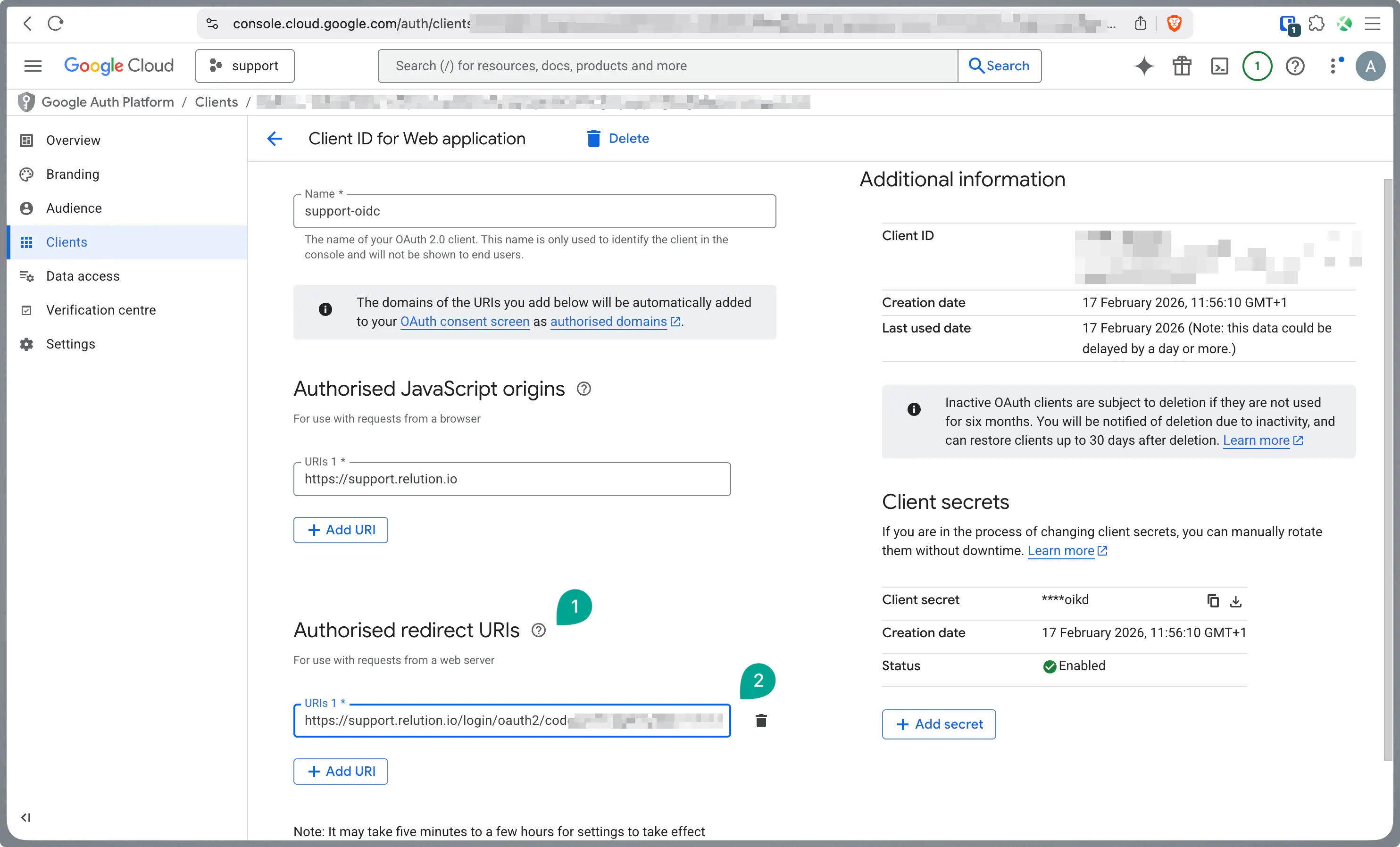
Return to console.cloud.google.com.
Update the Authorized redirect URIs with the Redirect URL you just copied from Relution.

Notes
Backchannel Logout
Relution supports Backchannel Logout starting with server version 5.32.0.
Example Scenario: A user is simultaneously logged into multiple applications via SSO. When logging out of the SSO service, Backchannel Logout ensures that sessions in all other applications are also terminated, even if they are running in the background.