OIDC
Introduction
OpenID Connect (OIDC) is an identity protocol built on top of OAuth 2.0 that provides secure authentication and authorization. It allows users to securely log in to various services while service providers can simultaneously access verified identity information. The following article describes how to set up OpenID Connect (OIDC) in Relution using Microsoft Azure.
Settings in Relution
OIDC can be configured in the Relution portal under Settings > OpenID Connect.
The following screenshots include a working configuration using Microsoft Azure.
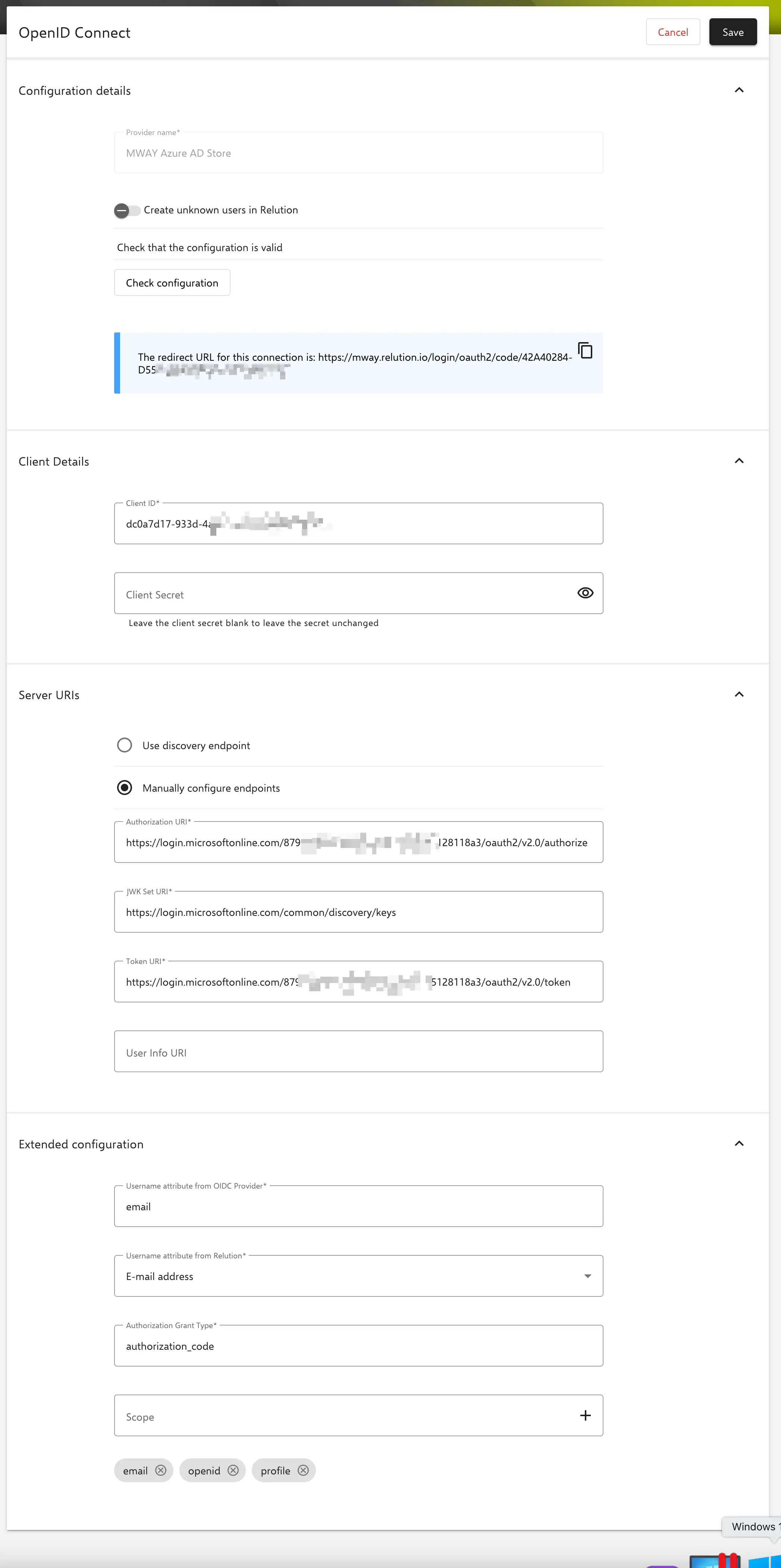
Configuration details
Name of the provider: Will be displayed on the login button in the relution portalCreate unknown users in Relution: Unknown users are created by login in Relution.
If a login is done with an unknown user on the store orga with OIDC configured, it will be created in the store organization. In the case of multiple clients with OIDC configuration, the login must be made via the organization URL so that the unknown user is created in the corresponding organization. This URL is displayed in the portal in the OIDC connections.
Client Details
Client ID" Corresponds to the application ID in Azure.Client Secret: Corresponds to the client secret key to the application ID in Azure.
Server URIs
Use Discovery Endpoint: If supported by the provider, an automatic configuration of the required URIs is performed.Manual configuration of endpoints: Necessary as soon as automatic discovery does not work.
If using Microsoft Azure, endpoints must be entered manually.
Authorization URI:https://login.microsoftonline.com/$-your-client-ID/oauth2/v2.0/authorize
JWK Set URI:https://login.microsoftonline.com/$-your-client-ID/discovery/v2.0/keys
Token URI:https://login.microsoftonline.com/$-your-client-ID/oauth2/v2.0/token
User Info URI:https://graph.microsoft.com/oidc/userinfo
Advanced configuration
The username attribute from the OIDC provider contains the unique username of the authenticated user.
The username attribute in Relution contains the unique username of the authenticated user.
Authorization Grant Type` The Authorization Grant Type is an OAuth mechanism that specifies how an application obtains access permissions from a user.
Scope Scopes define what identity information or resources the application can request from the OIDC provider
Settings in Azure
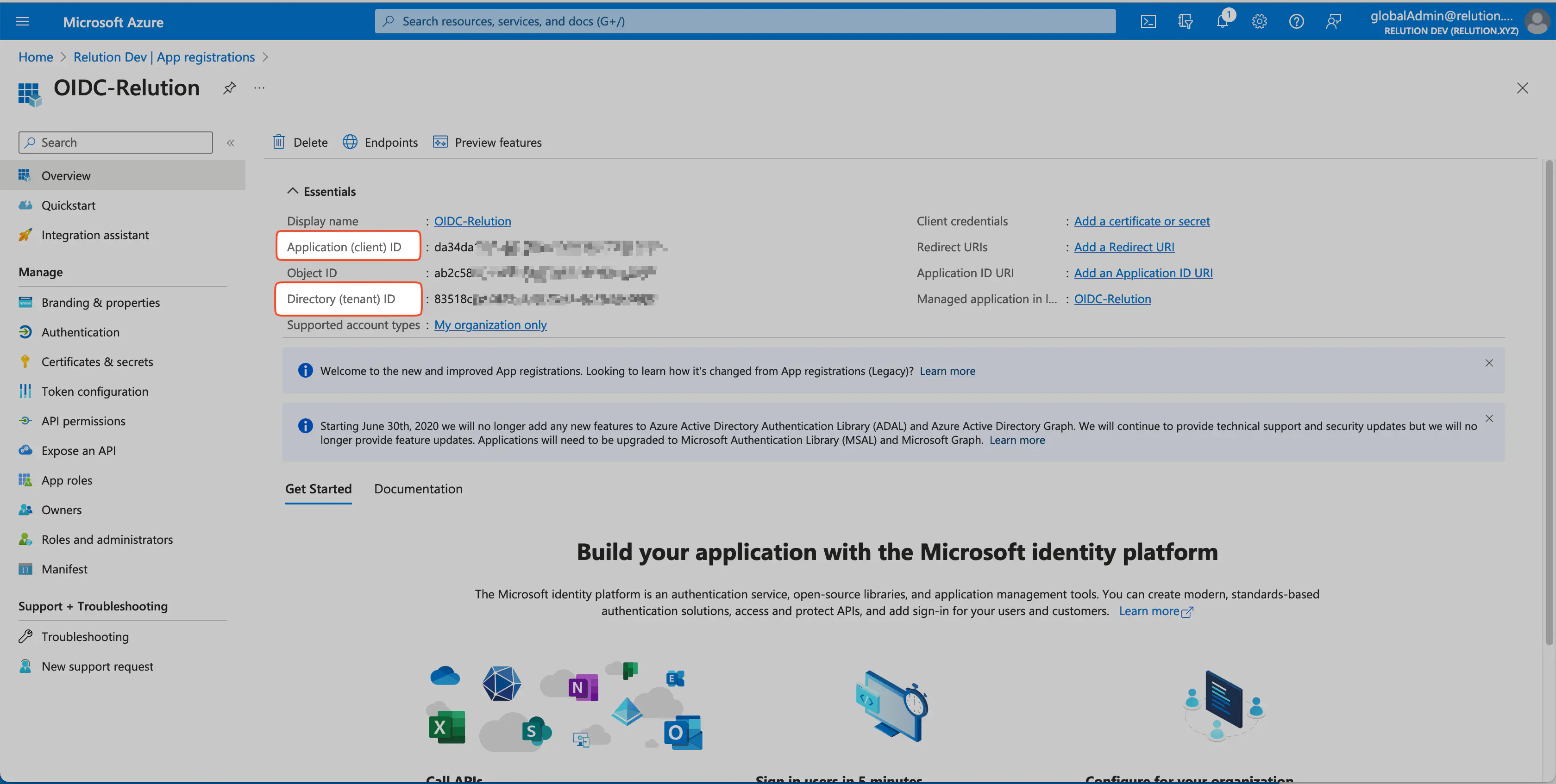
Creating a new app registry
- Logging in in Azure Portal, continuing on
Azure Active Directory.
- Creating new
App registry > Create new registryfor OIDC.
- Naming application, selecting account type
Only accounts in this organization directoryand regesting it.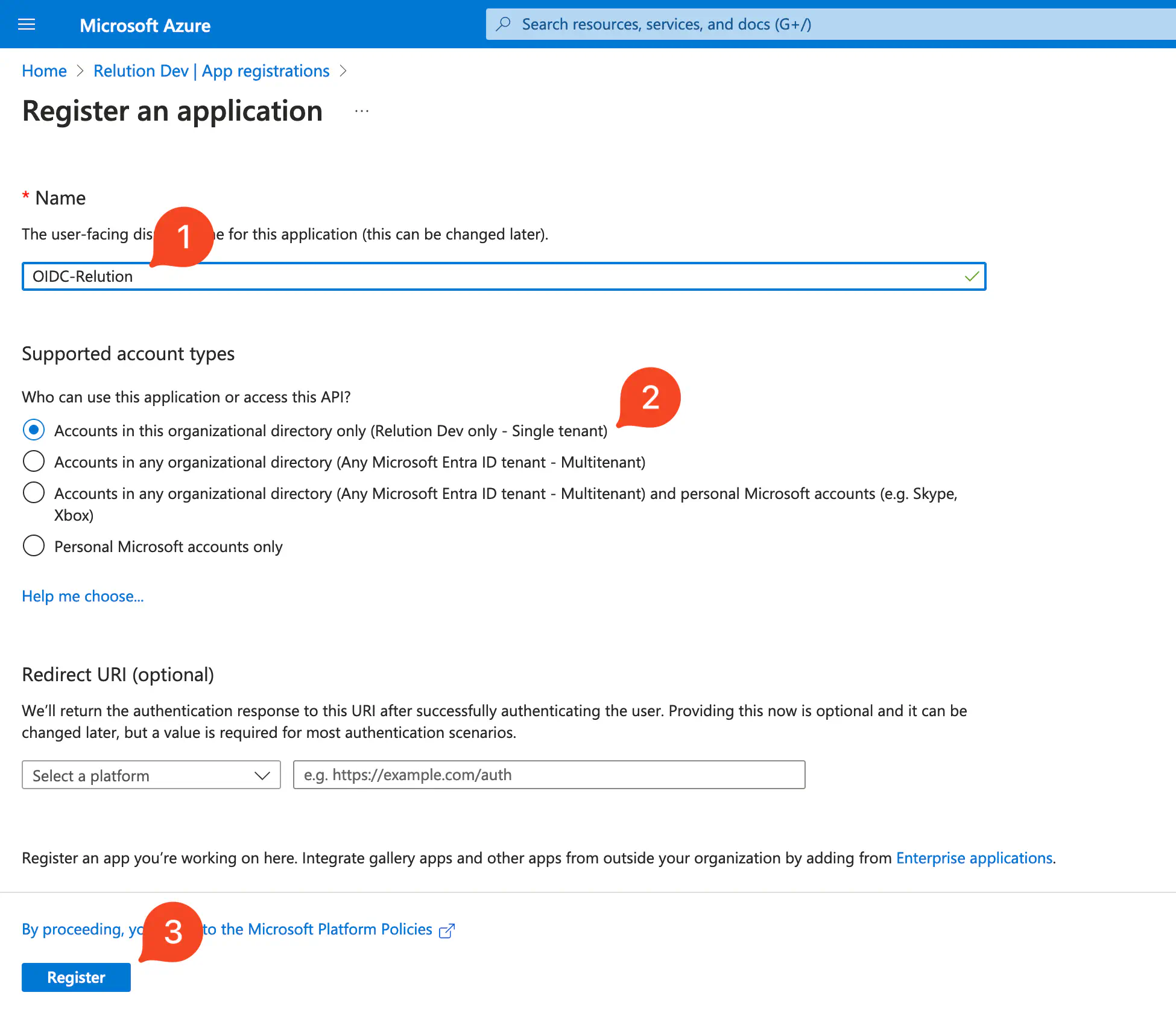
Adding secret client key (Client Secret) under Certificates & Secrets
- The required client secret is created under
Add a certificate or secret.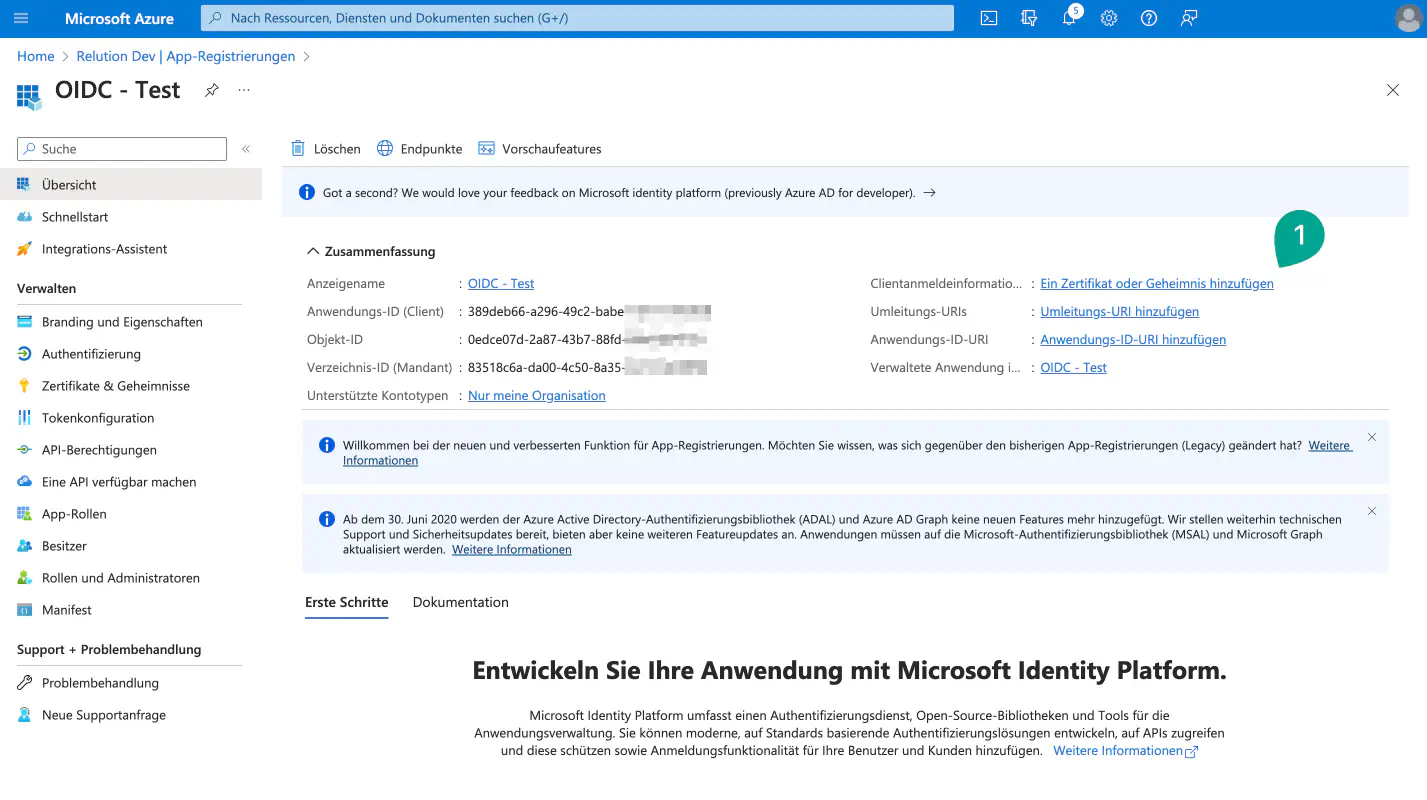
- Via
New secret client keytheDescriptionand validity periodValid untilcan be set.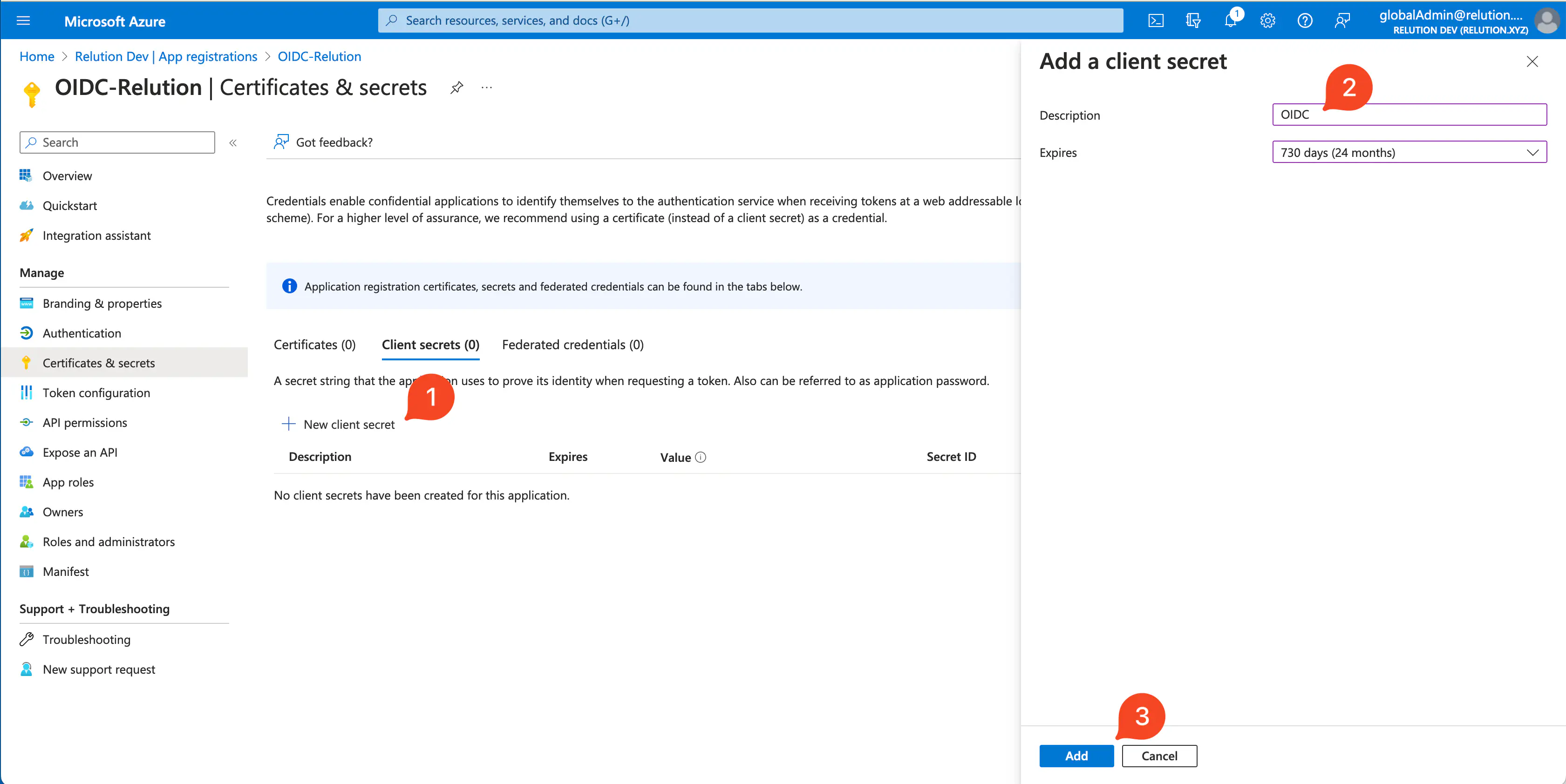
- The client key can be copied directly.
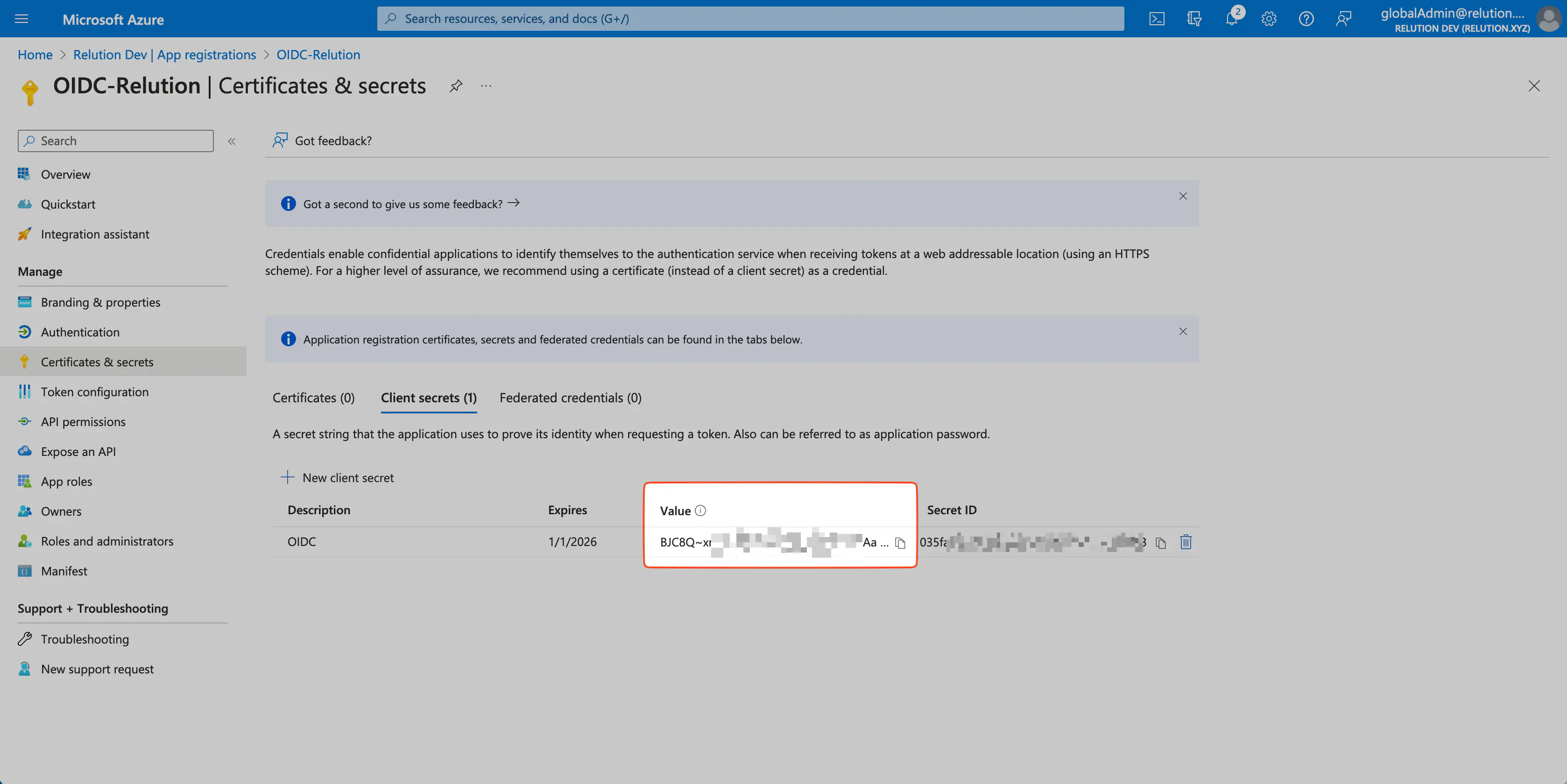
The client key is displayed only once!
When the validity period expires, there will be no connection and Relution will not be able to communicate with Azure. In this case, a new
secret client keymust be created for the application in Azure and re-transmitted to Relution.
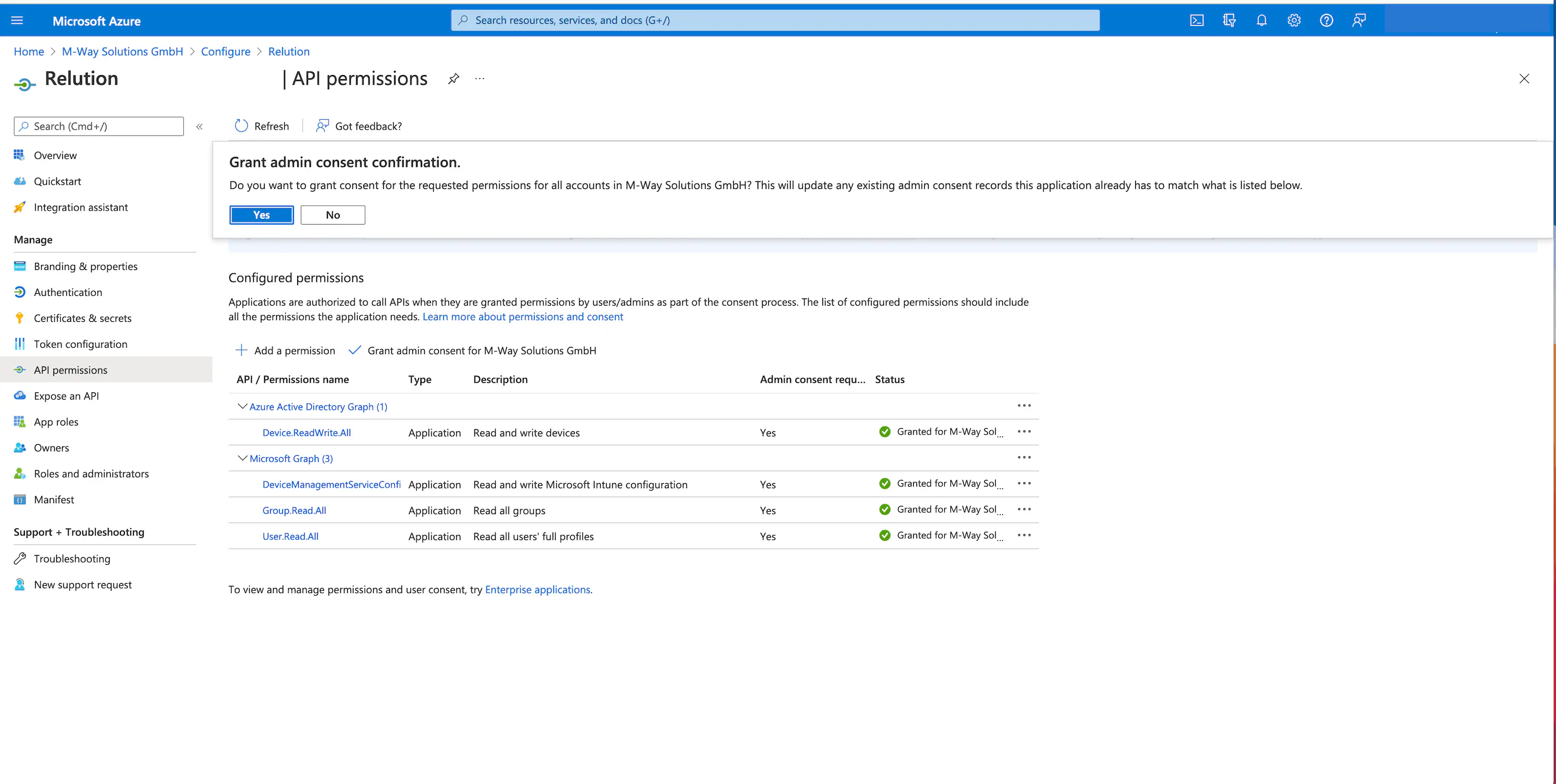
Configure API permissions.
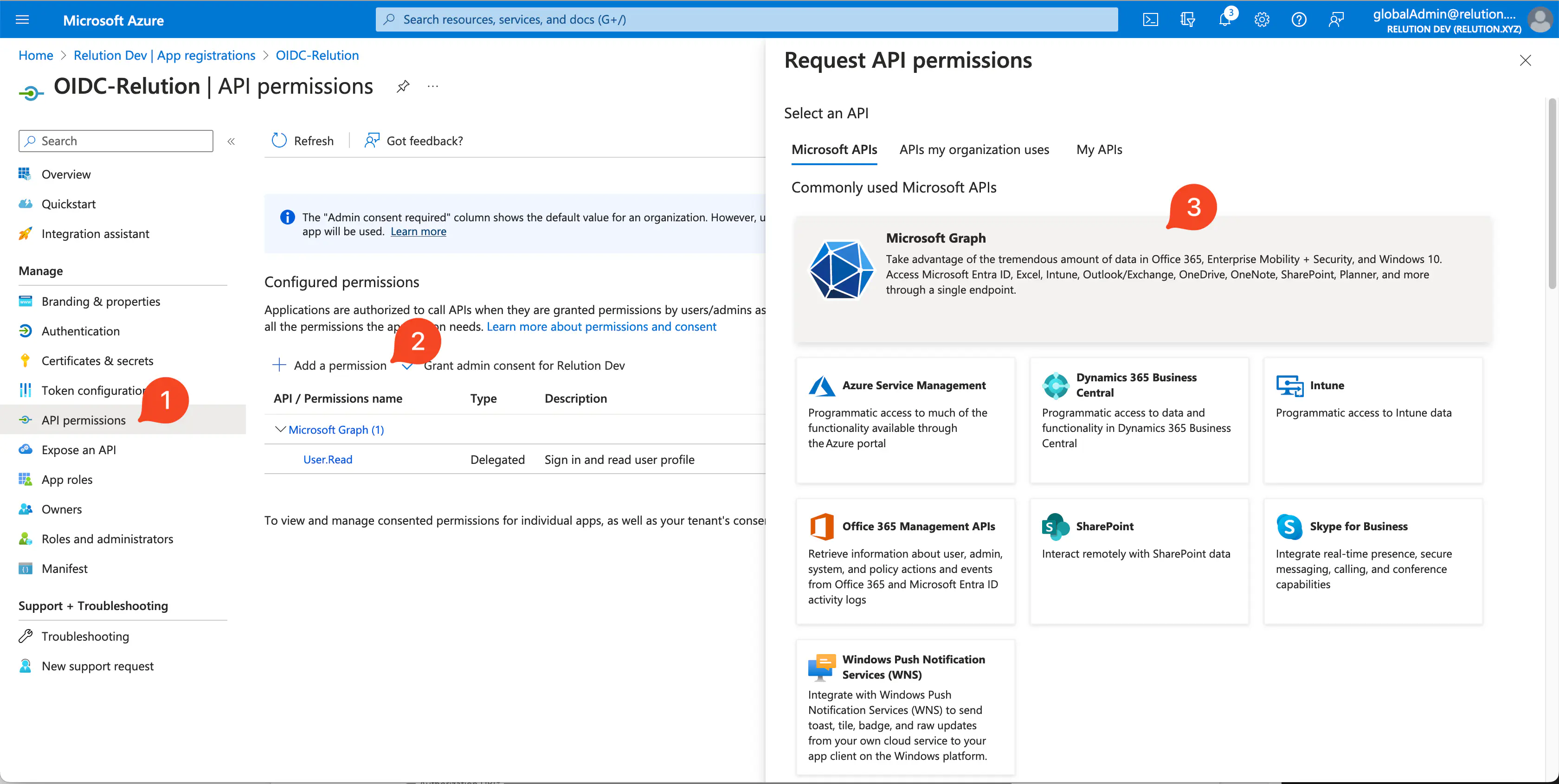
- Under
API Permissions > Configured Permissions,Add Permissionshould be clicked. - The
Microsoft Graphshould be selected underMicrosoft APIsin theRequest API Permissionsdialogue box.
- In the next step, the tile `Application permissions can be selected.
User.Read.Allfor can be selected forUser
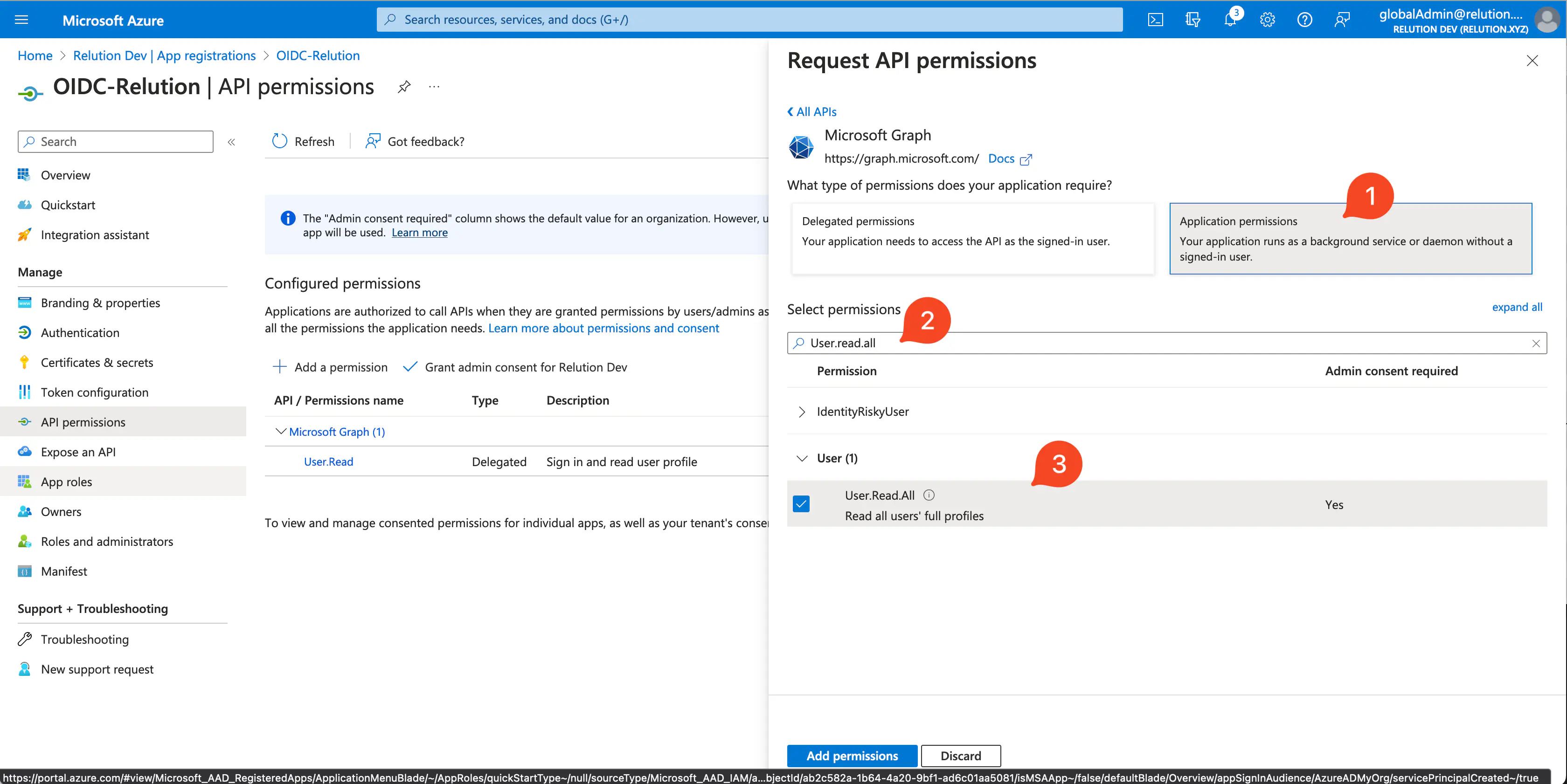
For the newly added API permissions, an exclamation mark is initially displayed as the status. Administrators must agree to this once in order for Microsoft Graph to ultimately receive the permissions. Afterwards, the status is displayed with a green check mark for
Grantedand the permissions are granted.
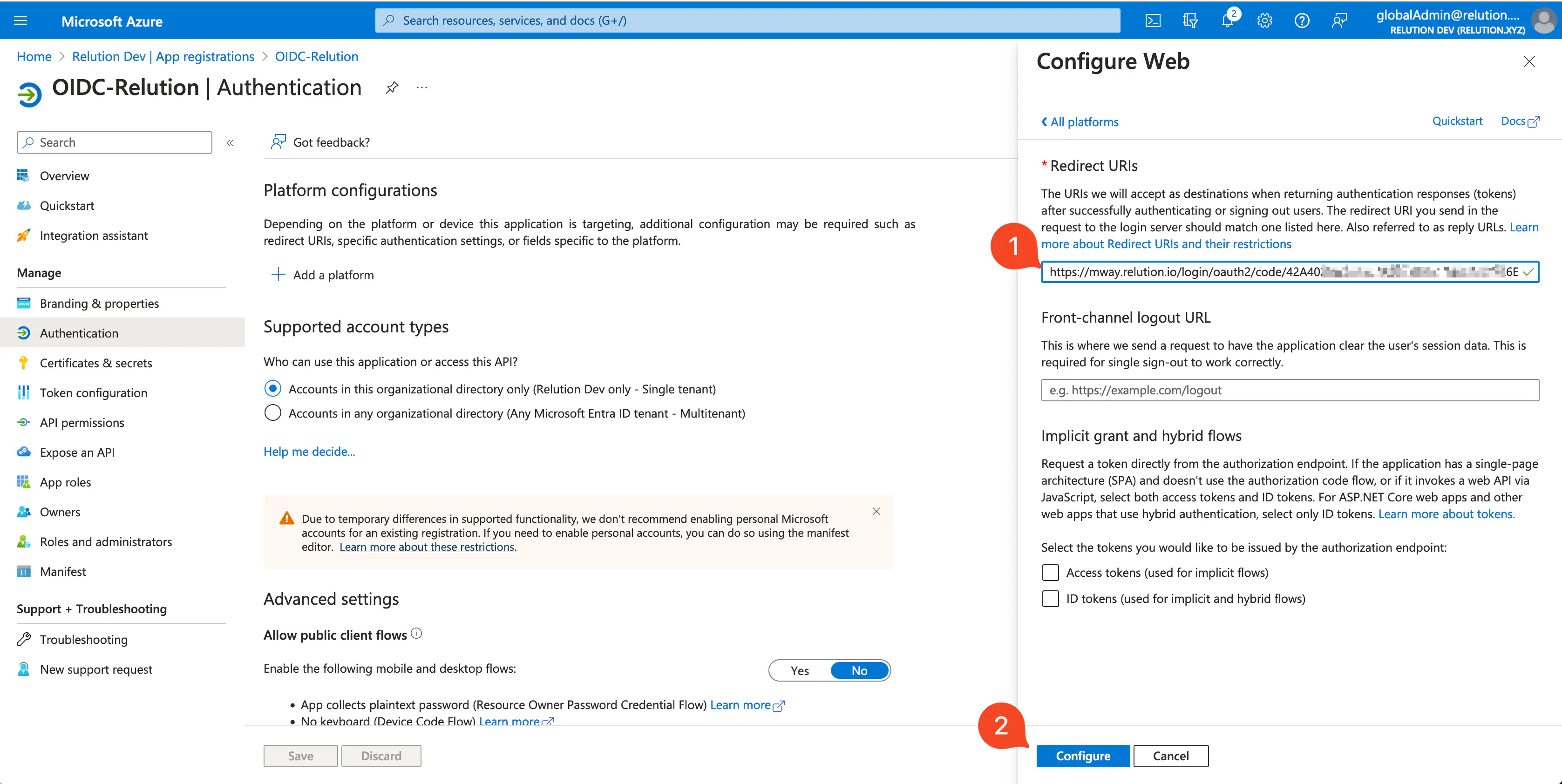
Add redirection URI
The redirection URI will be displayed in the Relution portal once the connection is configured and saved.