Autopilot
- Introduction
- Requirements for using Windows Autopilot
- How it works when starting up Windows 10/11 devices
- Benefits of Windows Autopilot
- Linking Azure AD and Relution
- Adding Windows 10/11 devices
- Preparation of the Out Of The Box Experience (OOBE) at Microsoft
- Synchronize stored Windows 10/11 devices in Relution
- Automatic enrollment of Windows 10/11 devices in Relution
On this page
- Introduction
- Requirements for using Windows Autopilot
- How it works when starting up Windows 10/11 devices
- Benefits of Windows Autopilot
- Linking Azure AD and Relution
- Adding Windows 10/11 devices
- Preparation of the Out Of The Box Experience (OOBE) at Microsoft
- Synchronize stored Windows 10/11 devices in Relution
- Automatic enrollment of Windows 10/11 devices in Relution
Introduction
Windows Autopilot is a cloud-based offering from Microsoft that automates the setup of new Windows 10/11 devices to prepare them for production use. The Windows 10/11 devices do not need to be reinstalled, Windows Autopilot uses the existing image on the devices. Relution supports automatic enrollment via Windows Autopilot and so Windows 10/11 devices can be quickly and easily inventoried in Relution via this path.
Requirements for using Windows Autopilot
Currently only possible using your own Relution server
Windows Autopilot can be used with Windows 10/11-Professional, -Enterprise or -Education from version 1709. An Azure instance with an Azure Active Directory (AAD) and Azure AD Premium P2 subscription is required. For setup in Azure, user must have the Global Administrator role. An internet connection must be available when the Windows 10/11 devices go live.
How it works when starting up Windows 10/11 devices
When starting the Out Of The Box Experience (OOBE) of the Windows 10/11 devices, if there is an existing network connection, the system automatically detects that it should be configured via Windows Autopilot. The devices submit their ID to Microsoft and check if it has been registered in Autopilot for an Azure AD environment. Then, the user must log in to the Microsoft login page with their credentials. The sign-in will enroll them in Relution and create a user account for the Azure AD user on the devices.
Benefits of Windows Autopilot
The goal of Windows Autopilot is to avoid the cumbersome task of individually loading new Windows 10/11 devices with an internally created image. Instead, the devices should transform themselves into pre-configured devices as independently as possible. This minimizes the effort required for image creation and reduces the time required for physical registration and provisioning of the devices. Azure only needs to be set up once for this, and auto-enrollment works until the defined validity date of the secret client key expires (see below).
s
Linking Azure AD and Relution
In the Relution portal, under Settings > Organization > Azure Active Directory, you will find instructions to help you set up and link Azure AD and Relution.
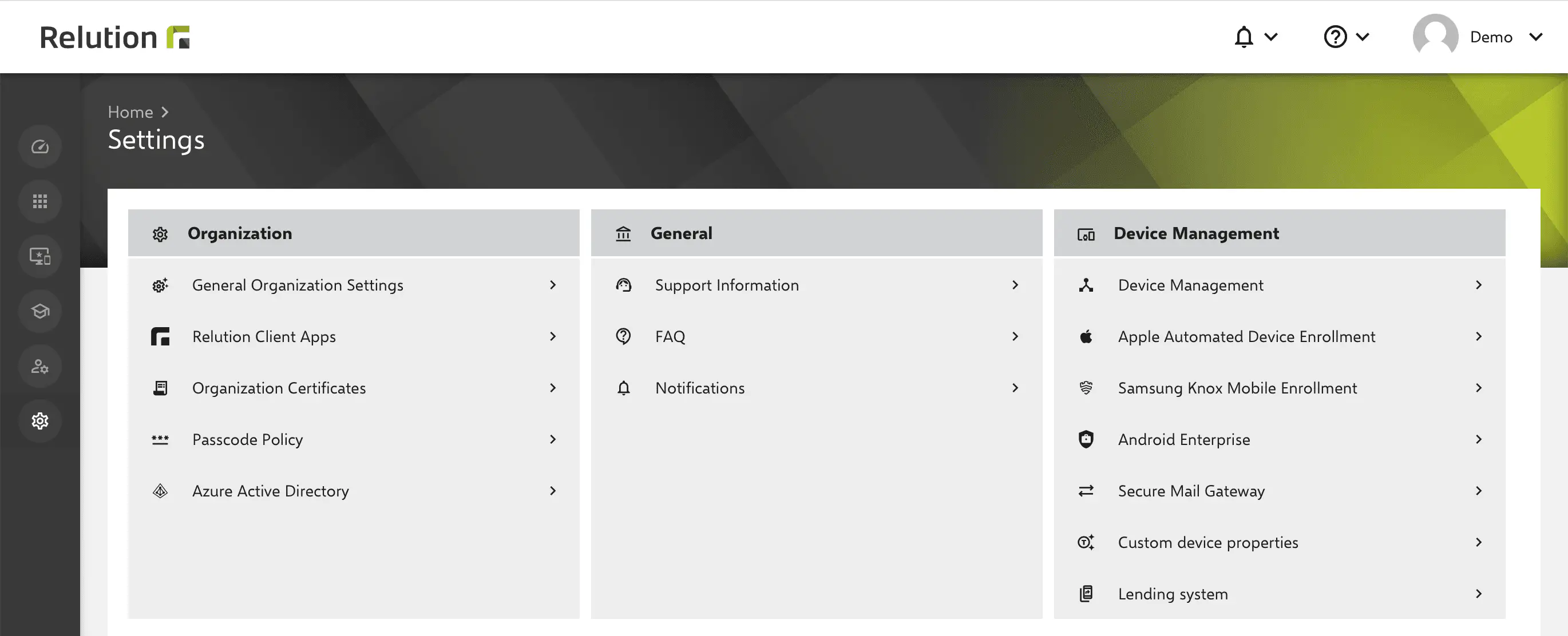
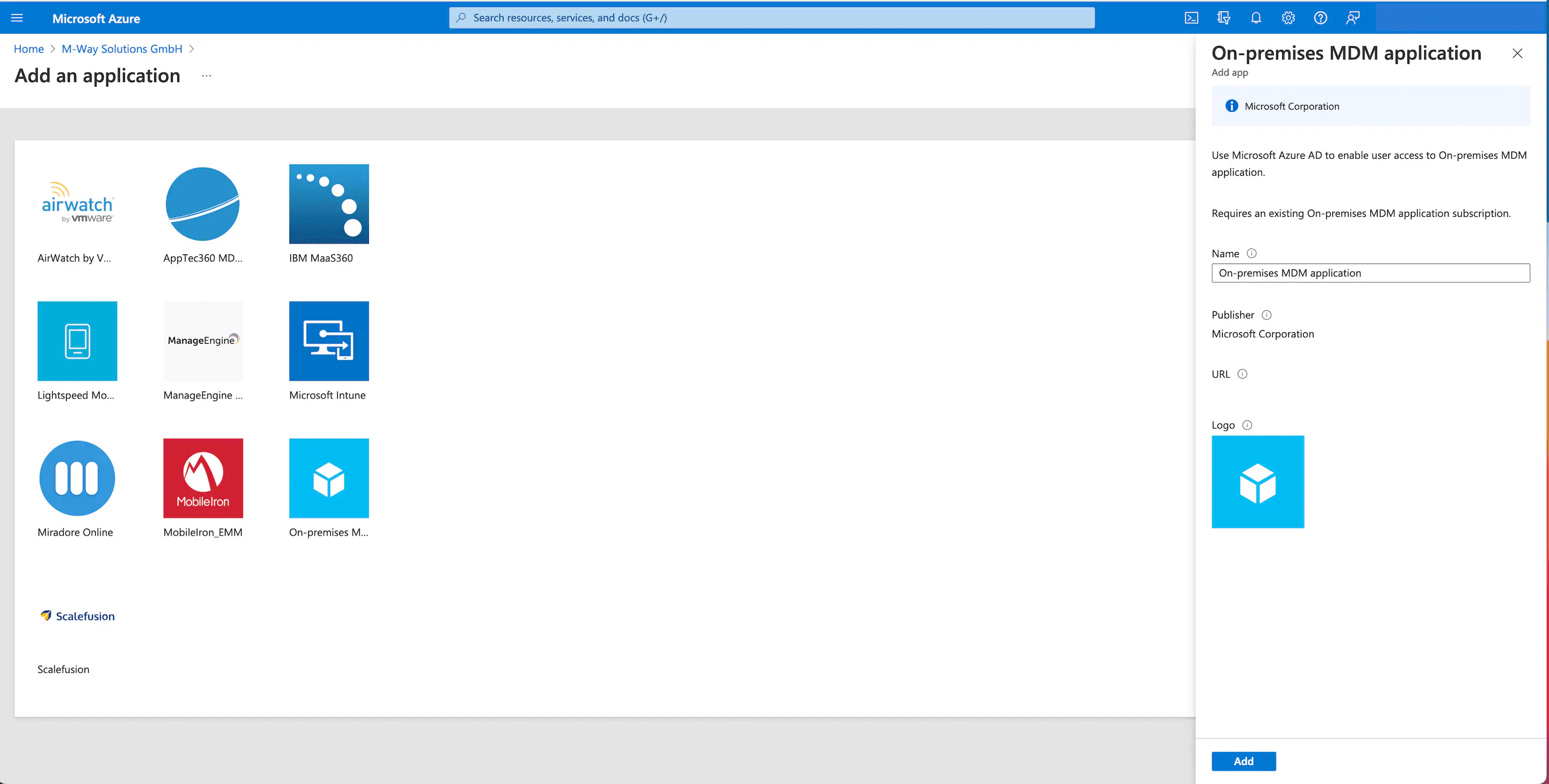
Adding the MDM application
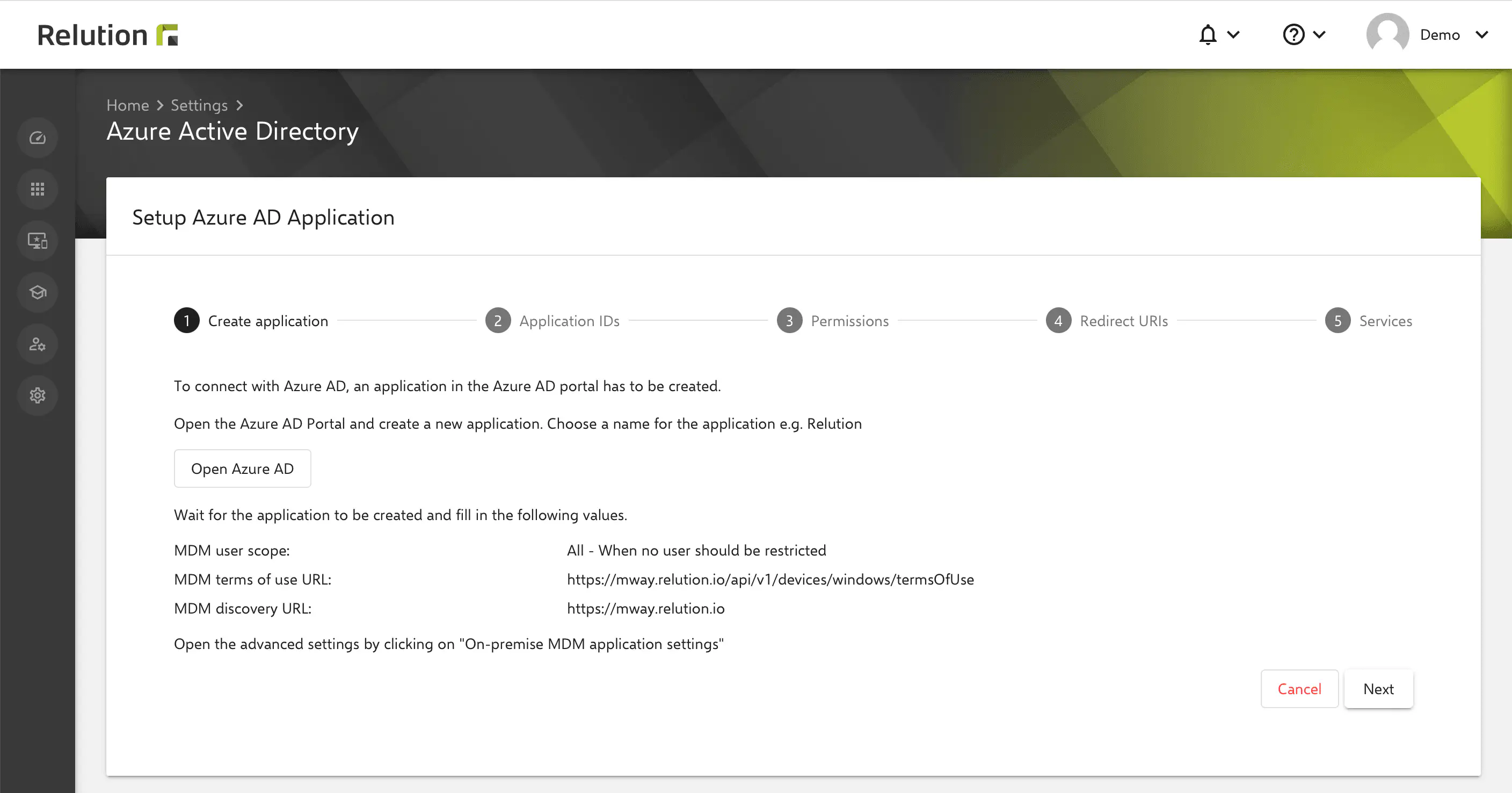
First, create a new MDM application in Azure and complete it with the details from the Relution guide.
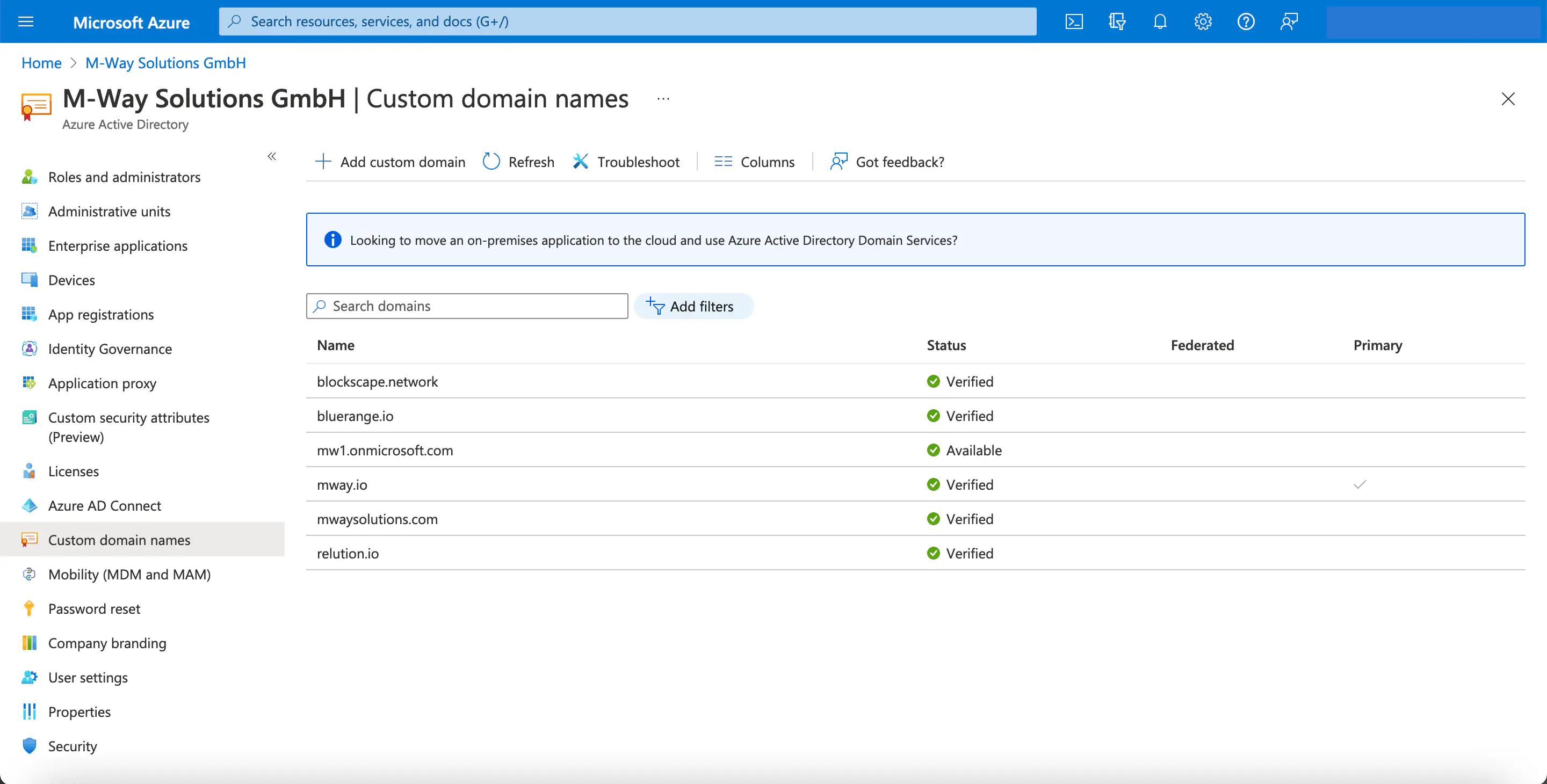
Add the domain of the corresponding Relution server in Azure AD under names of custom domains. This may take some time to complete. For more information, see the Microsoft documentation.
Under Mobility (MDM and MAM), the desired MDM application is then added and activated:
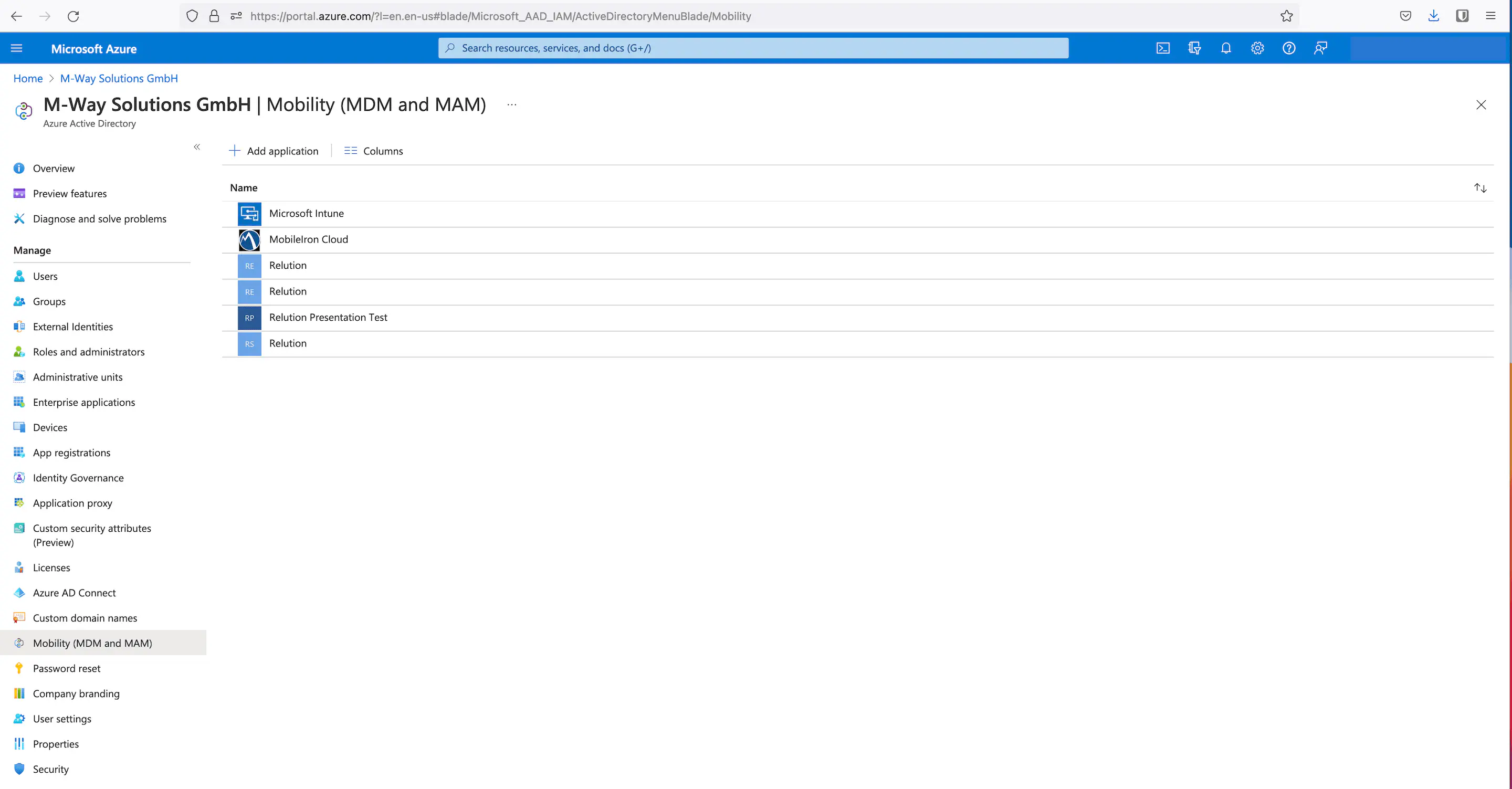
- Select the tile
On-Premises MDM Applicationat the bottom right. - Assign a name.
- Click on
Add.
Now the new MDM application is configured with the information of the Relution guide from step:
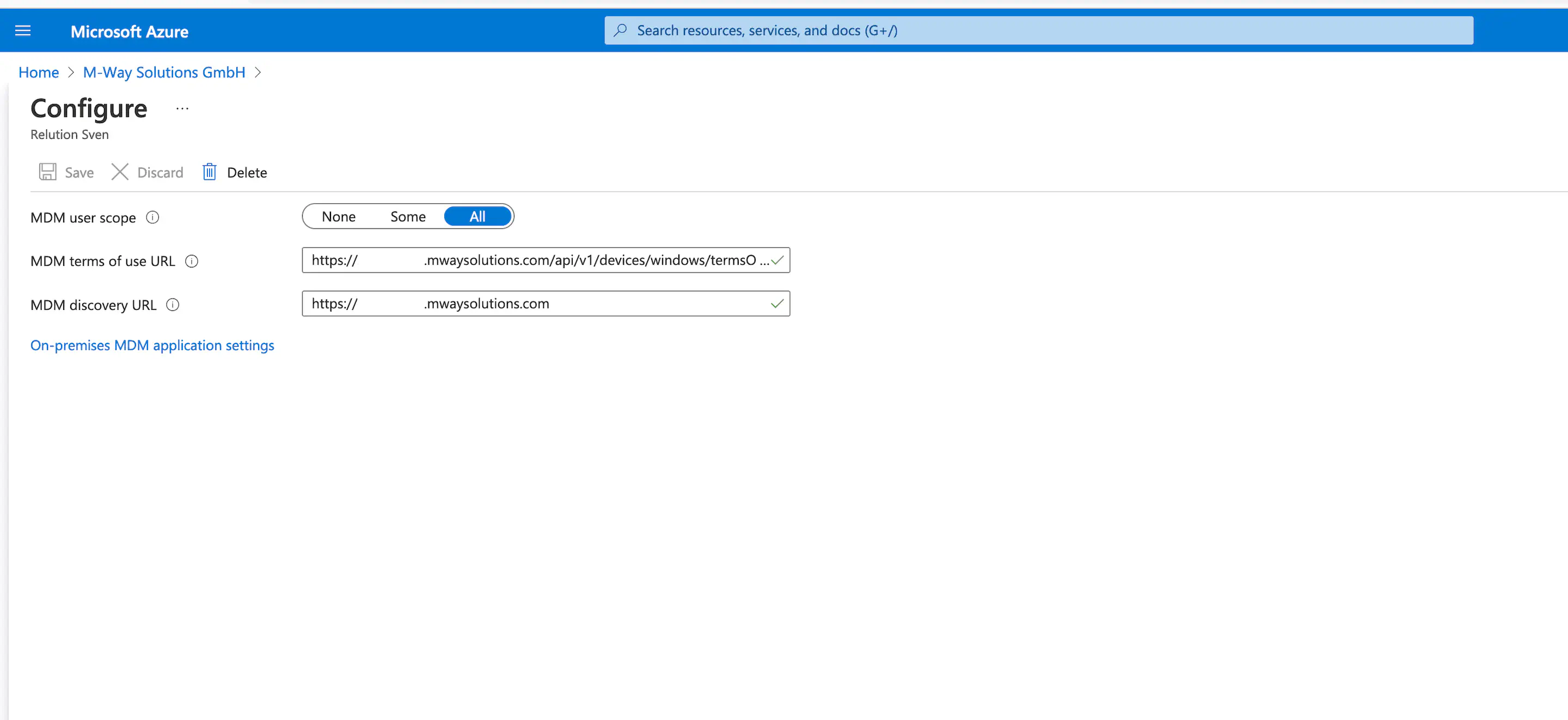
- Select
AllforMDM User Area(all user can performAutopilotenrollment). - Enter the URL to the
MDM Terms of Usefrom Relution:
https://serverurl/api/v1/devices/windows/termsOfUse
Microsoft will request this URL before each enrollment, no web page will be accessed
- Enter the
MDM discoveryURL:
https://serverurl/api/v1/devices/windows/discover
- Click on
Save.
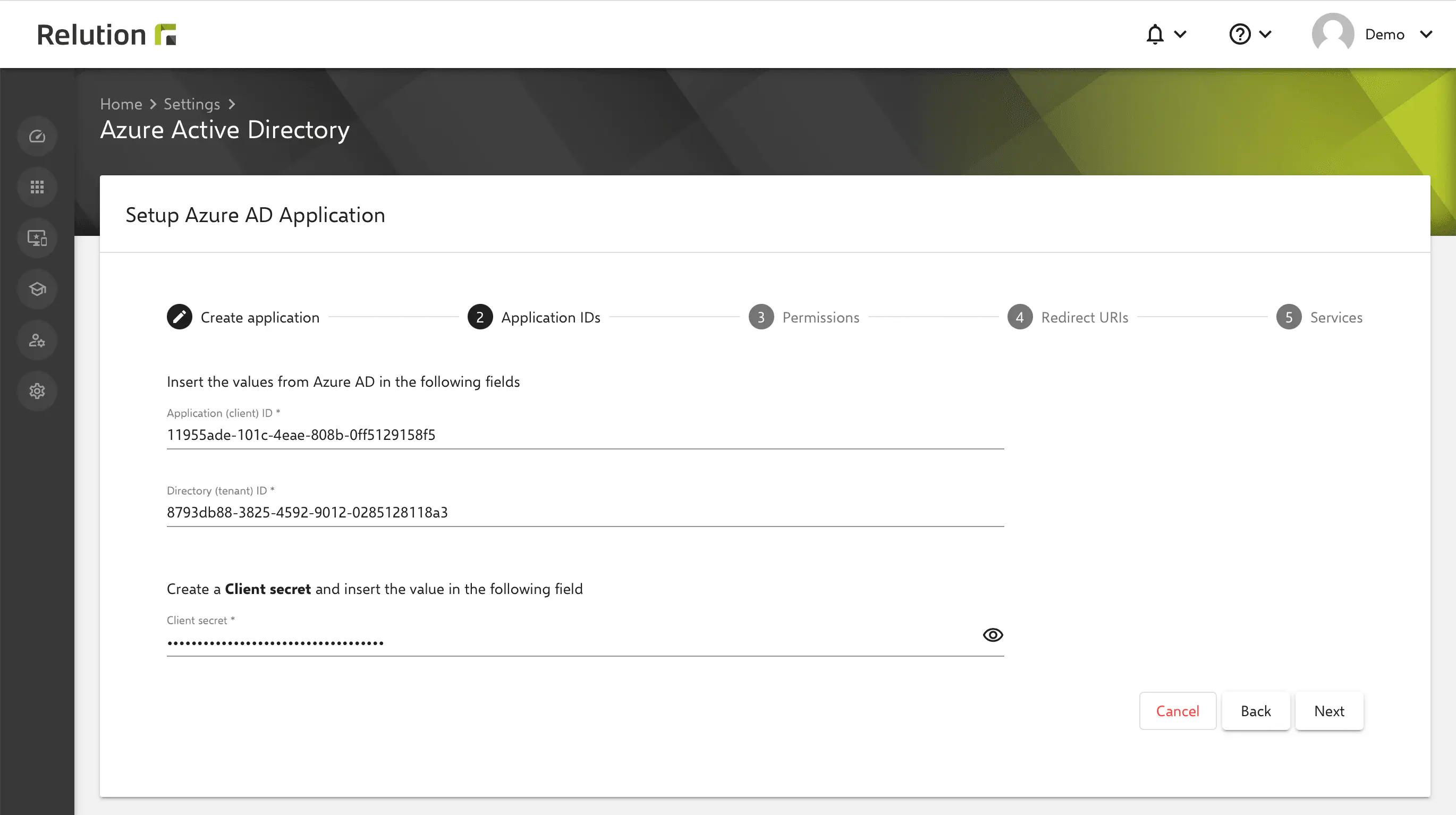
Making the MDM application settings
After the new MDM application is created, the on-premises MDM application settings can be made in Azure. Here, it is mandatory that the following details are transferred from Azure to the Relution guide in step 2:
Application ID (Client).Directory ID (client).- Value of the `secret client key.
Now, in the on-premises MDM application settings in Azure, click Application ID URI to edit.
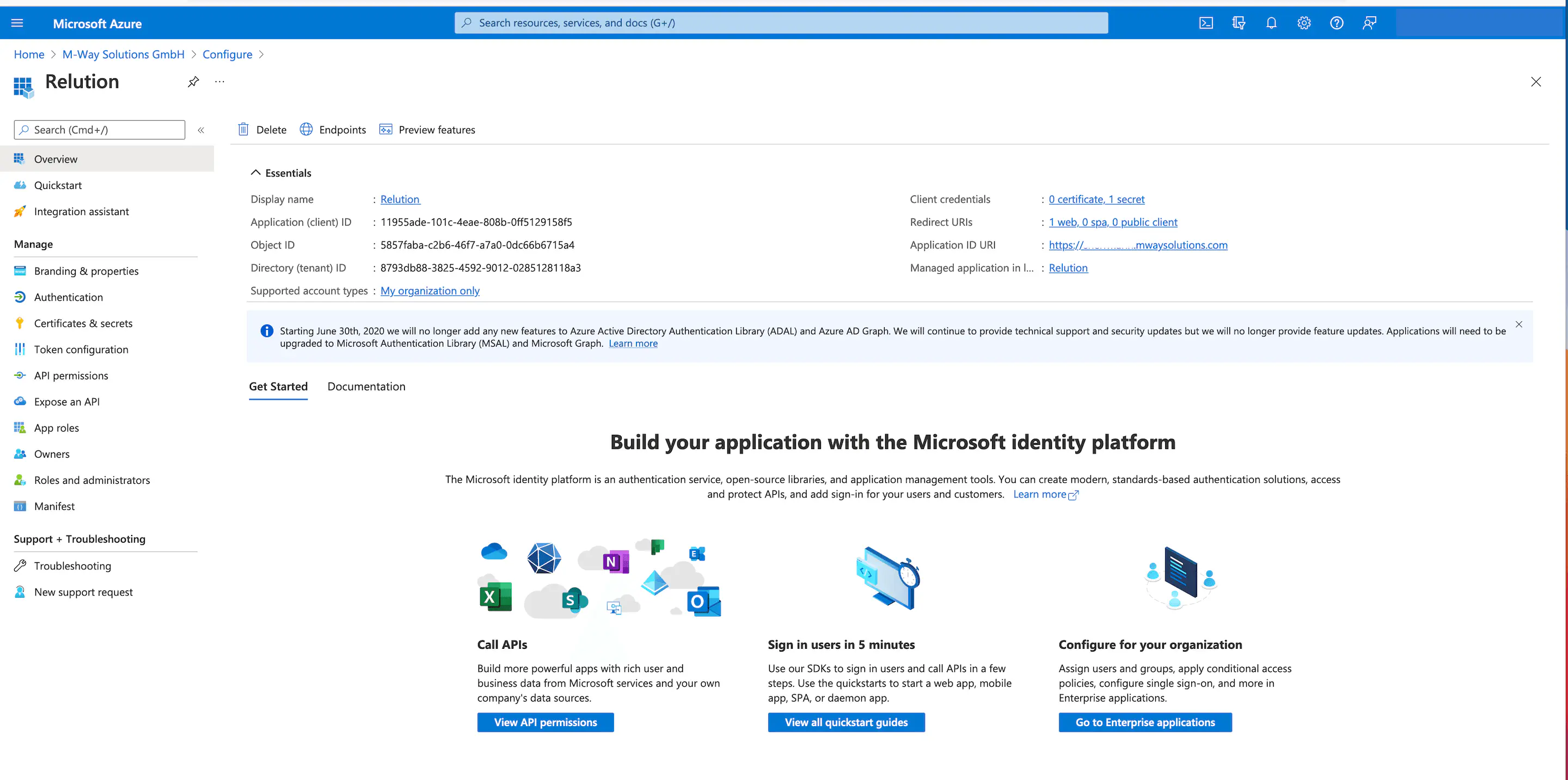
Then, enter the corresponding server URL in the following view for Application ID URI.
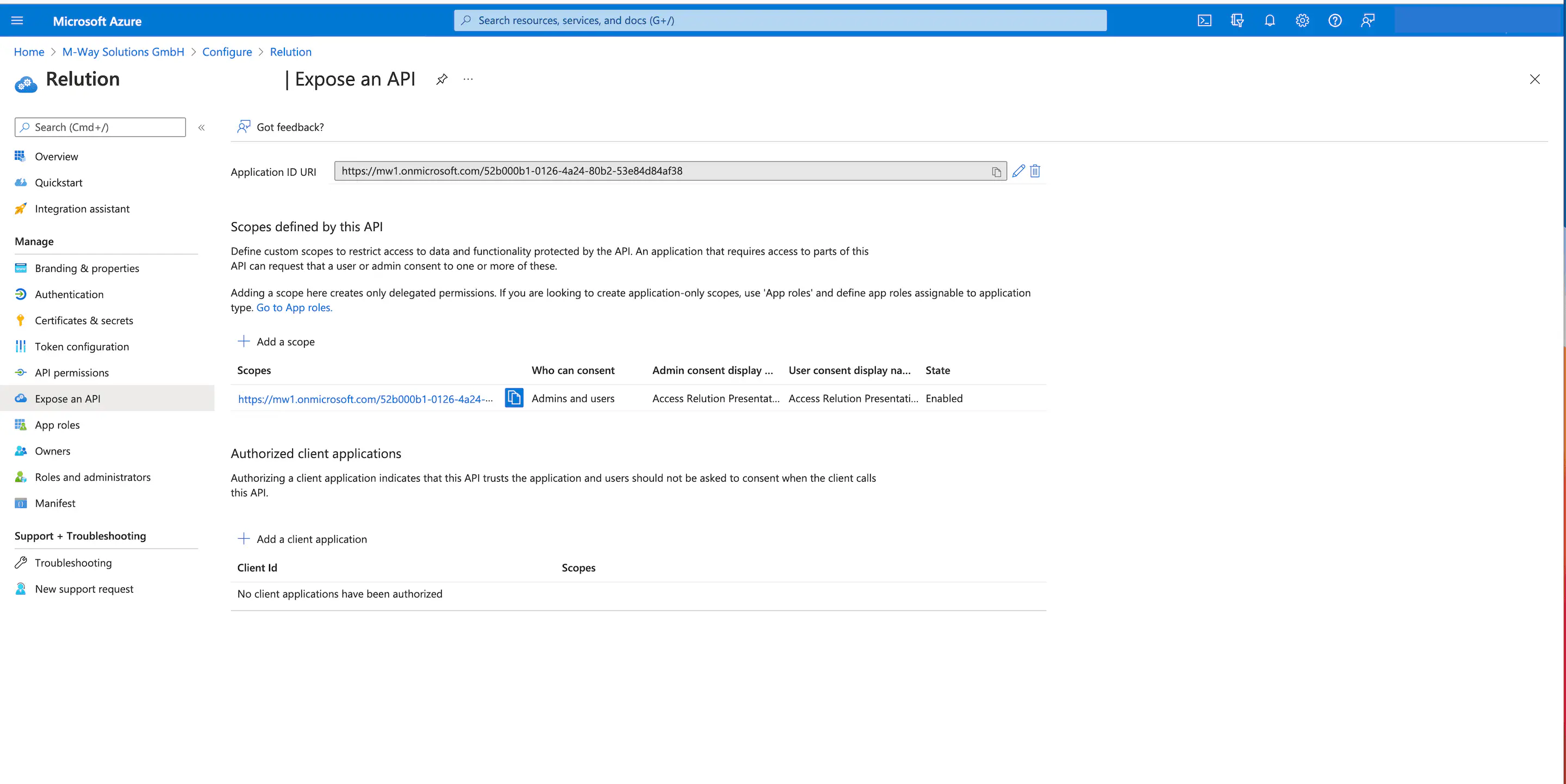
Next, add a Secret Client Key (Client Secret) under Certificates & Secrets:
- Click on
New secret client keyin tabSecret client keys. - In the dialogue box,
Add secret client keyenter a description and the validity. - Click
Add.
When the validity period expires, there is no longer a connection and Relution cannot communicate with Azure. In this case, a new
secret client keymust be created for the application in Azure and re-transmitted to Relution.
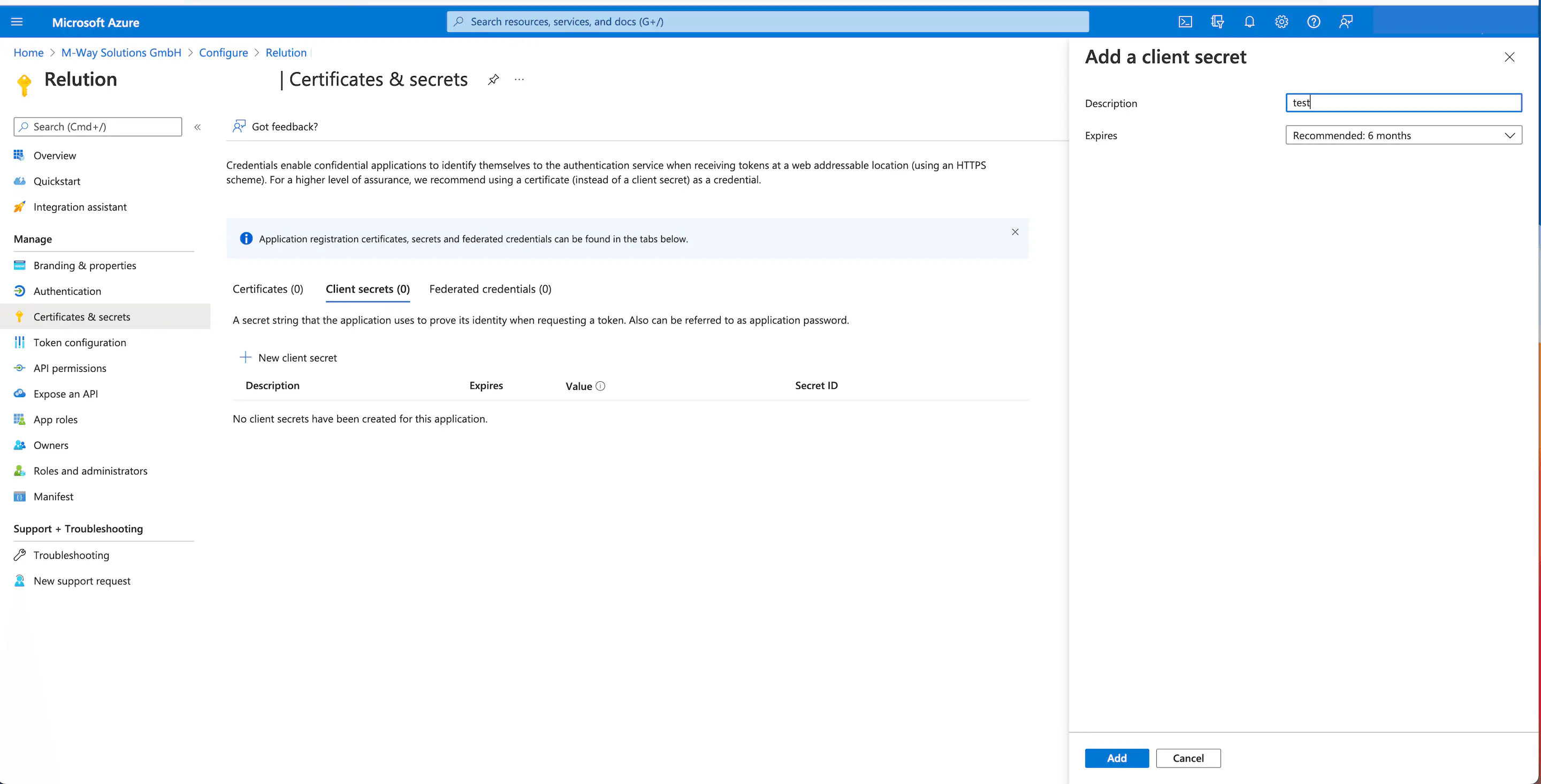
After that, the listing under tab secret client keys will show the new entry.
The associated
Valueis only displayed once now and it is mandatory to copy and transfer it to Relution.
Configuring API permissions
In step 3 of the Relution instructions, the API permissions are now configured:
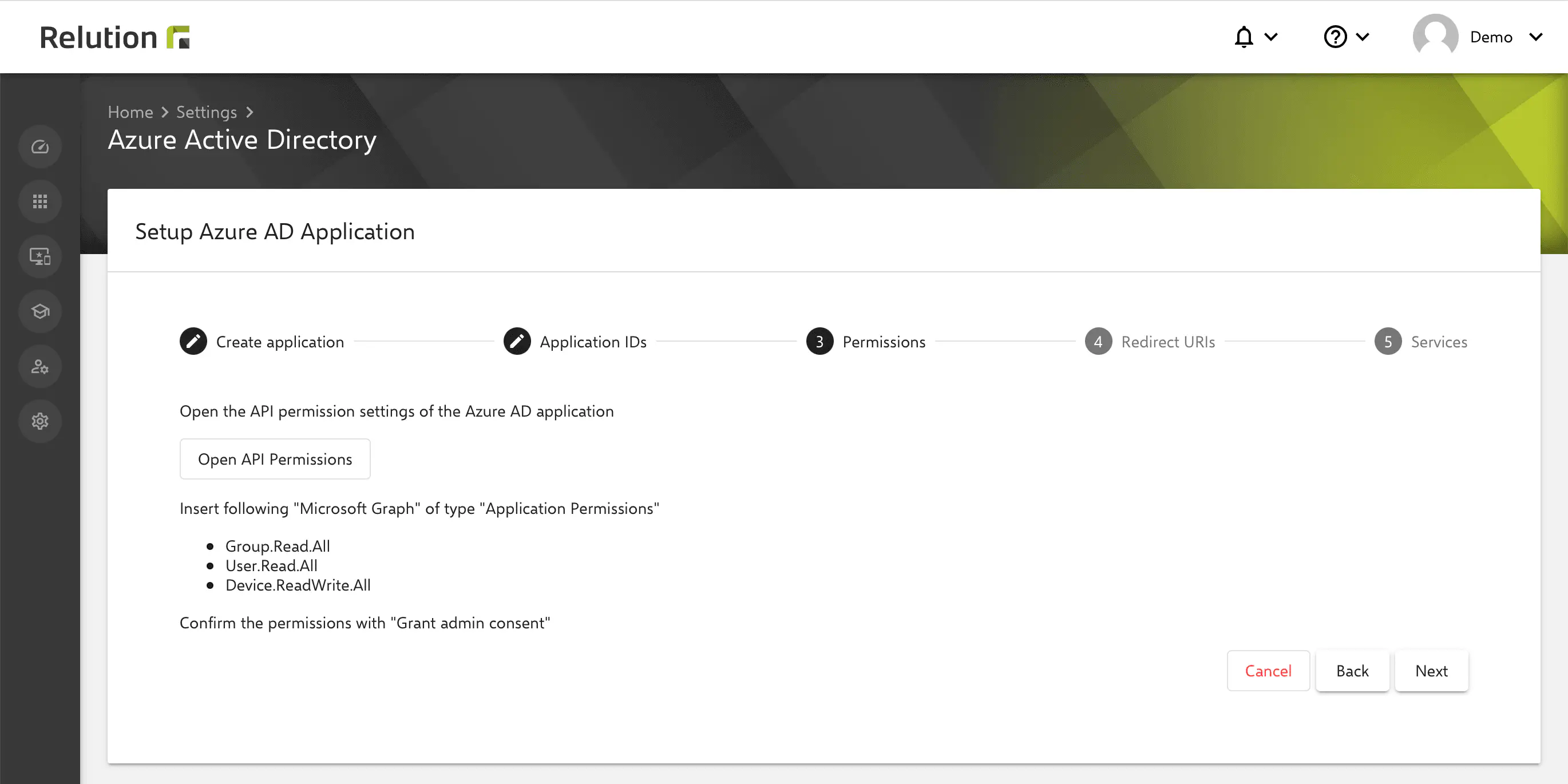
New permissions may need to be added here later, if new features are added by Microsoft for Windows Autopilot in the future.
The following settings need to be made in Azure:
- Under
API Permissions > Configured Permissions, clickAdd Permission. - Select
Microsoft GraphunderMicrosoft APIsin theRequest API Permissionsdialogue box.
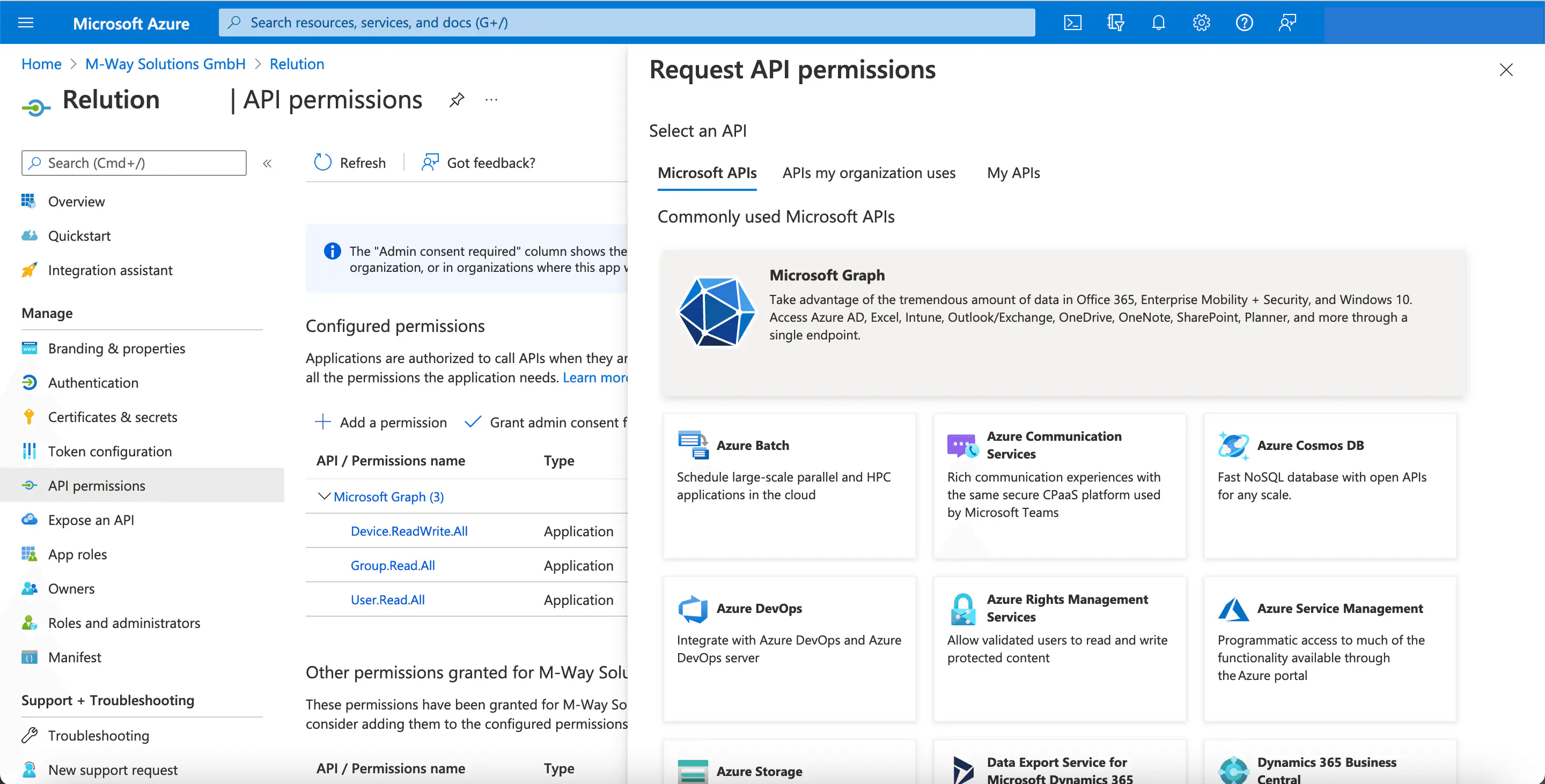
- In the next step, select the tile
Application permissions.
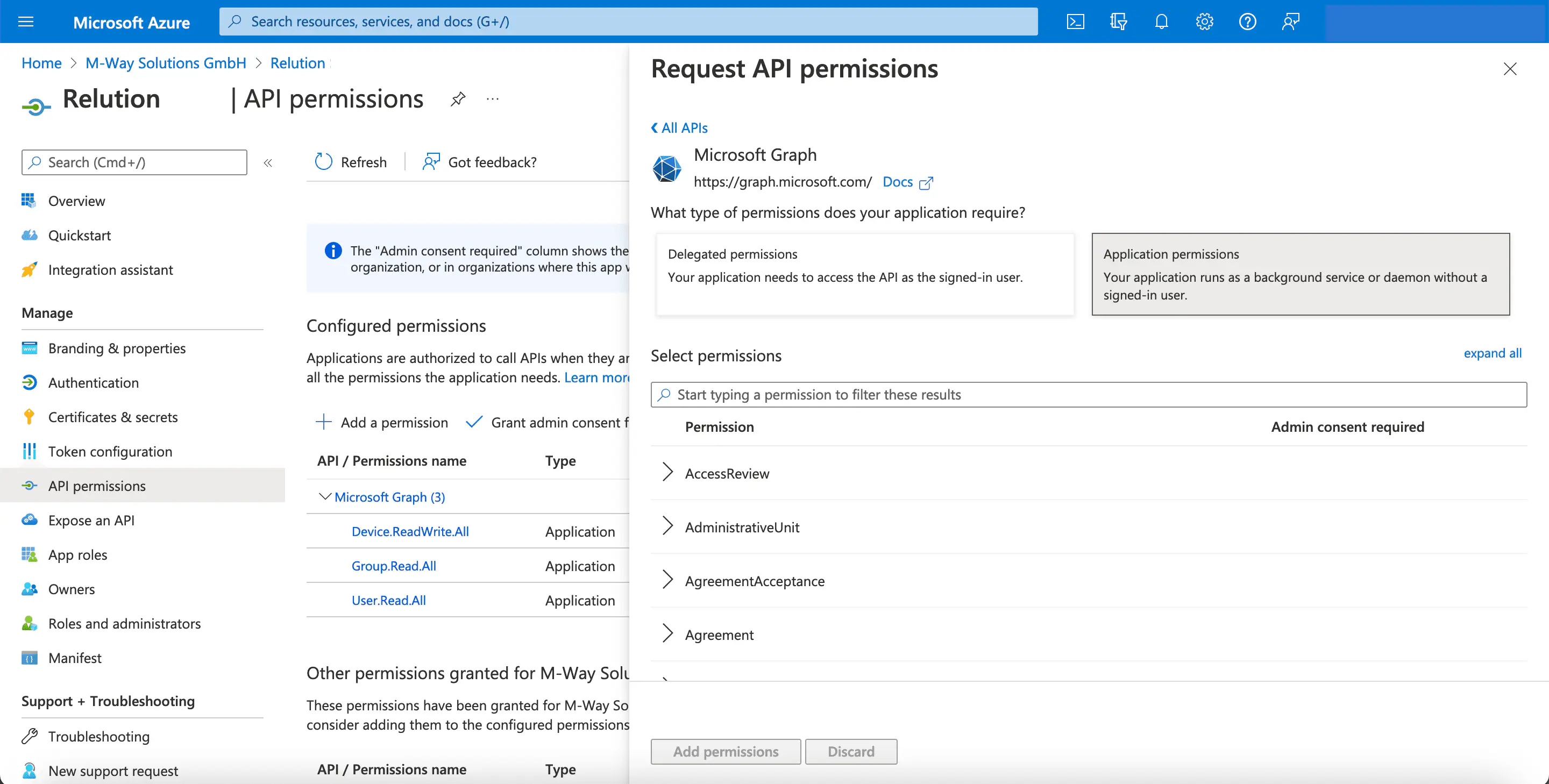
- Select
User.Read.AllforUser.
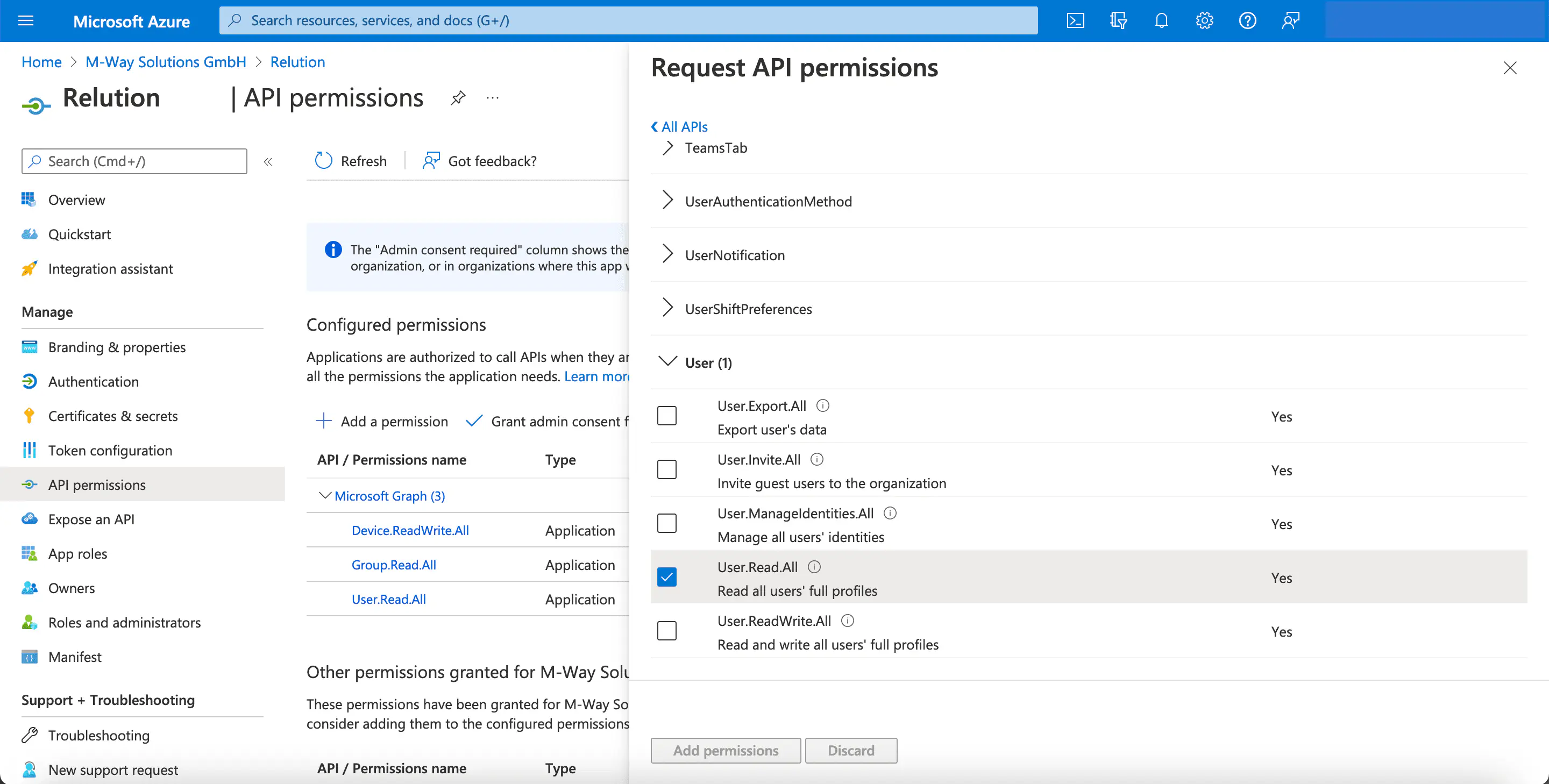
- Select
Group.Read.Allfor `Group.
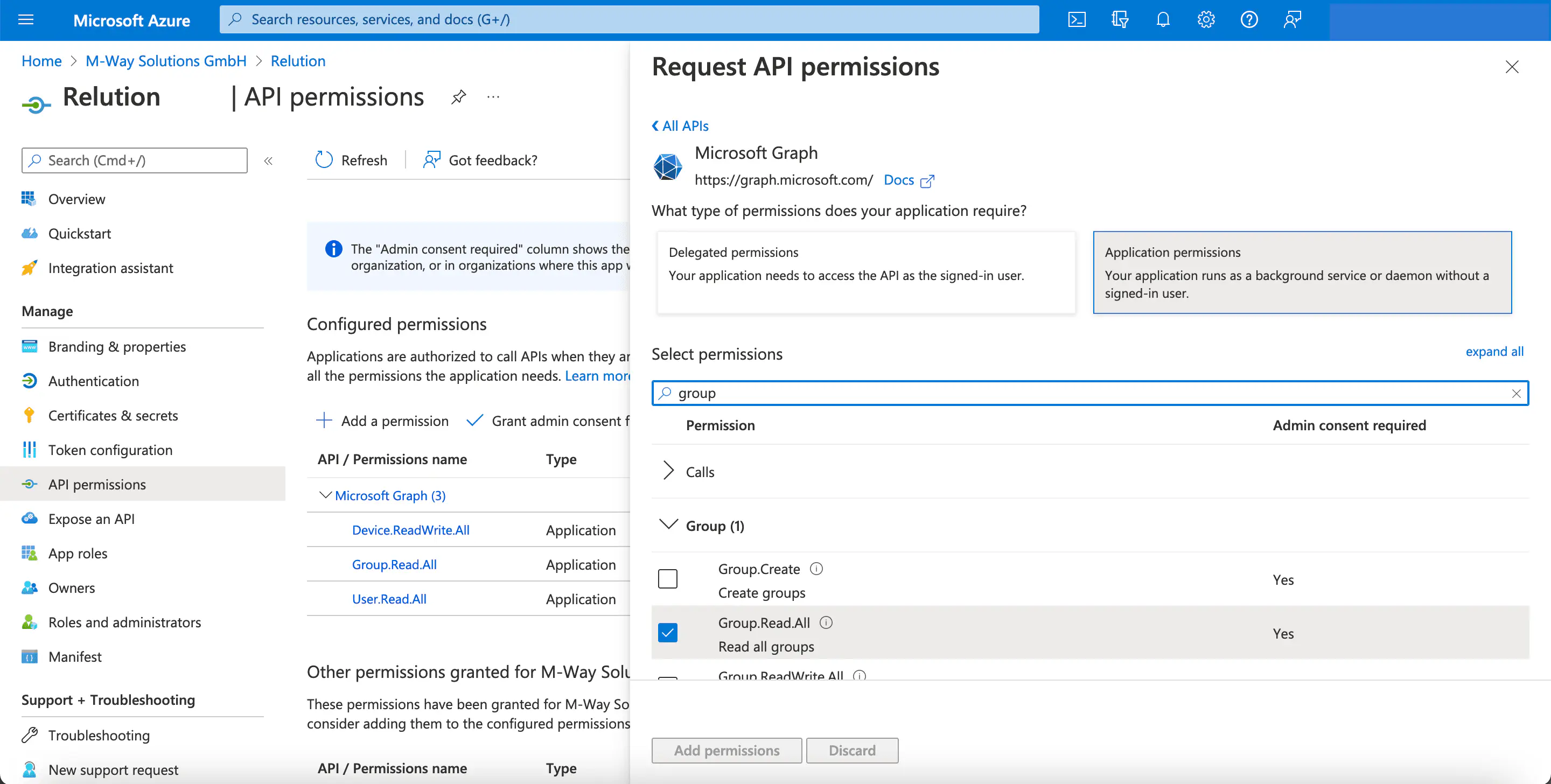
- Select
Device.ReadWrite.AllforDeviceand confirm the selection withAdd Permissions!
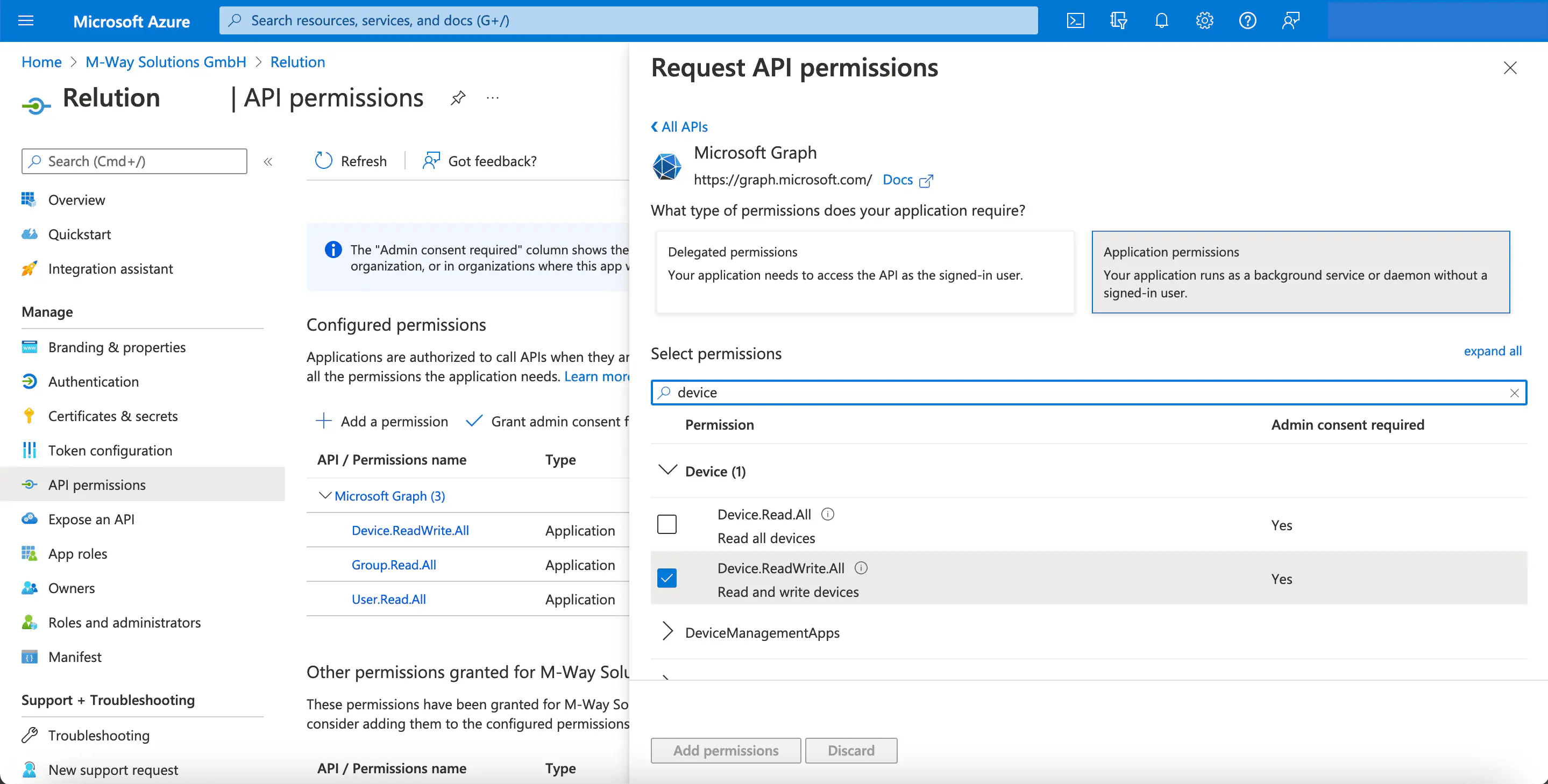
For the newly added API permissions, an exclamation mark is initially displayed as status. Administrators have to agree here once, so that Microsoft Graph finally receives the permissions. Afterwards, the status is displayed with a green check mark for Granted and the permissions are granted.
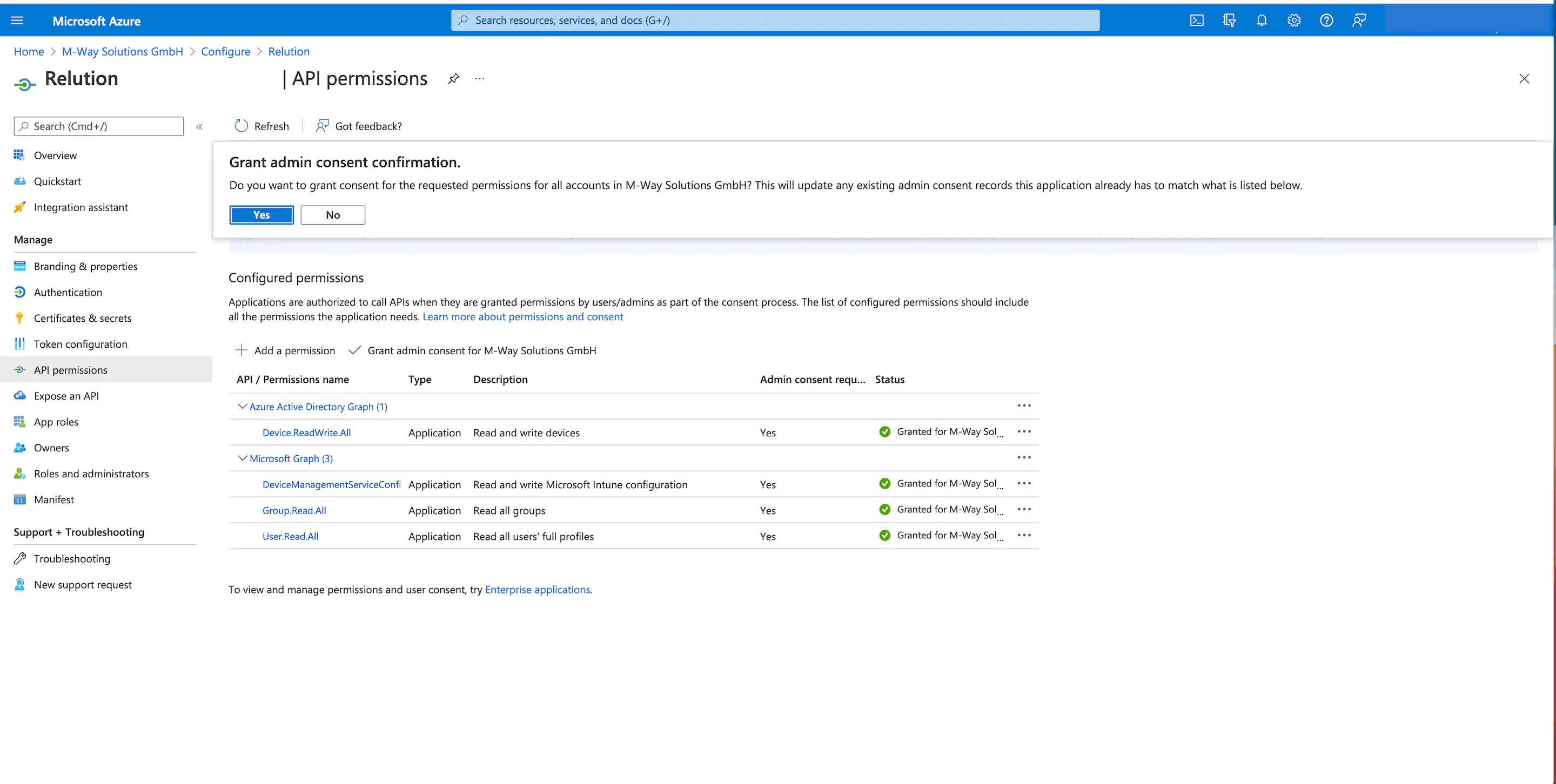
Defining the redirection URI
Step 4 of the Relution guide configures the redirection URI in Azure:
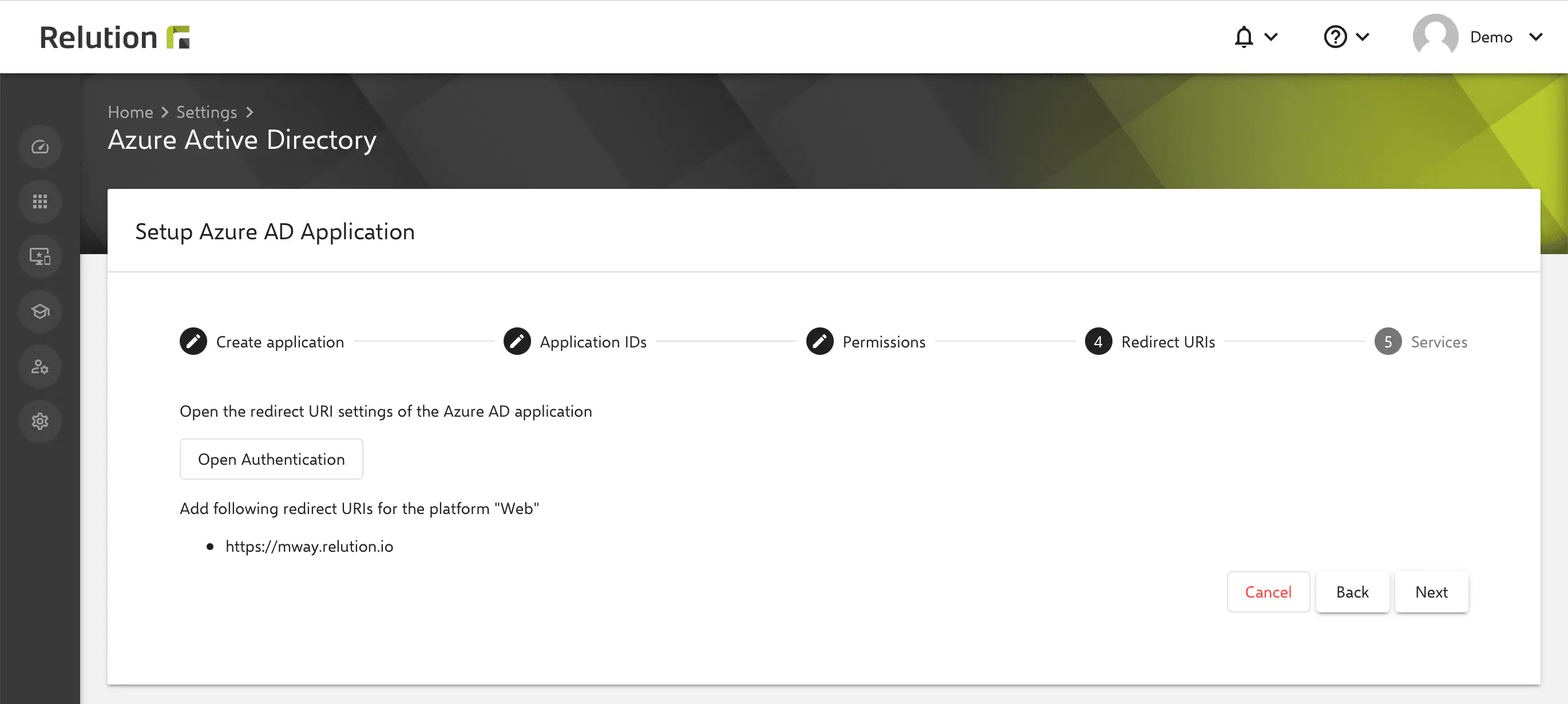
- Under
Authentication, clickAdd Platform. - In the
Configure Platformdialogue box, the tileWebshould be selected.
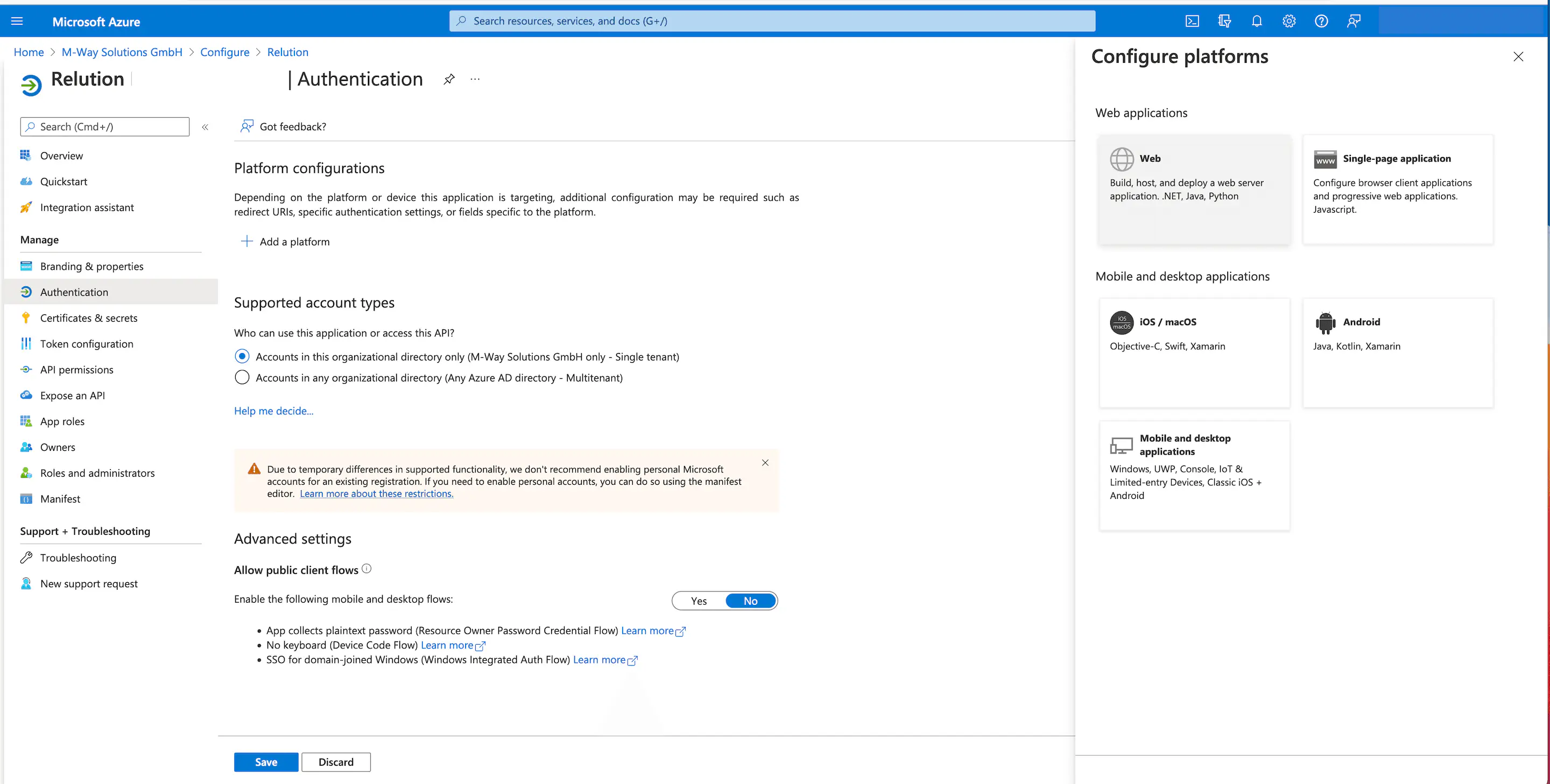
- In the next step, under
Web, one should enter the server URL atAdd redirection URI. - Uncheck the
ID tokenscheckbox. - Click on
Save.
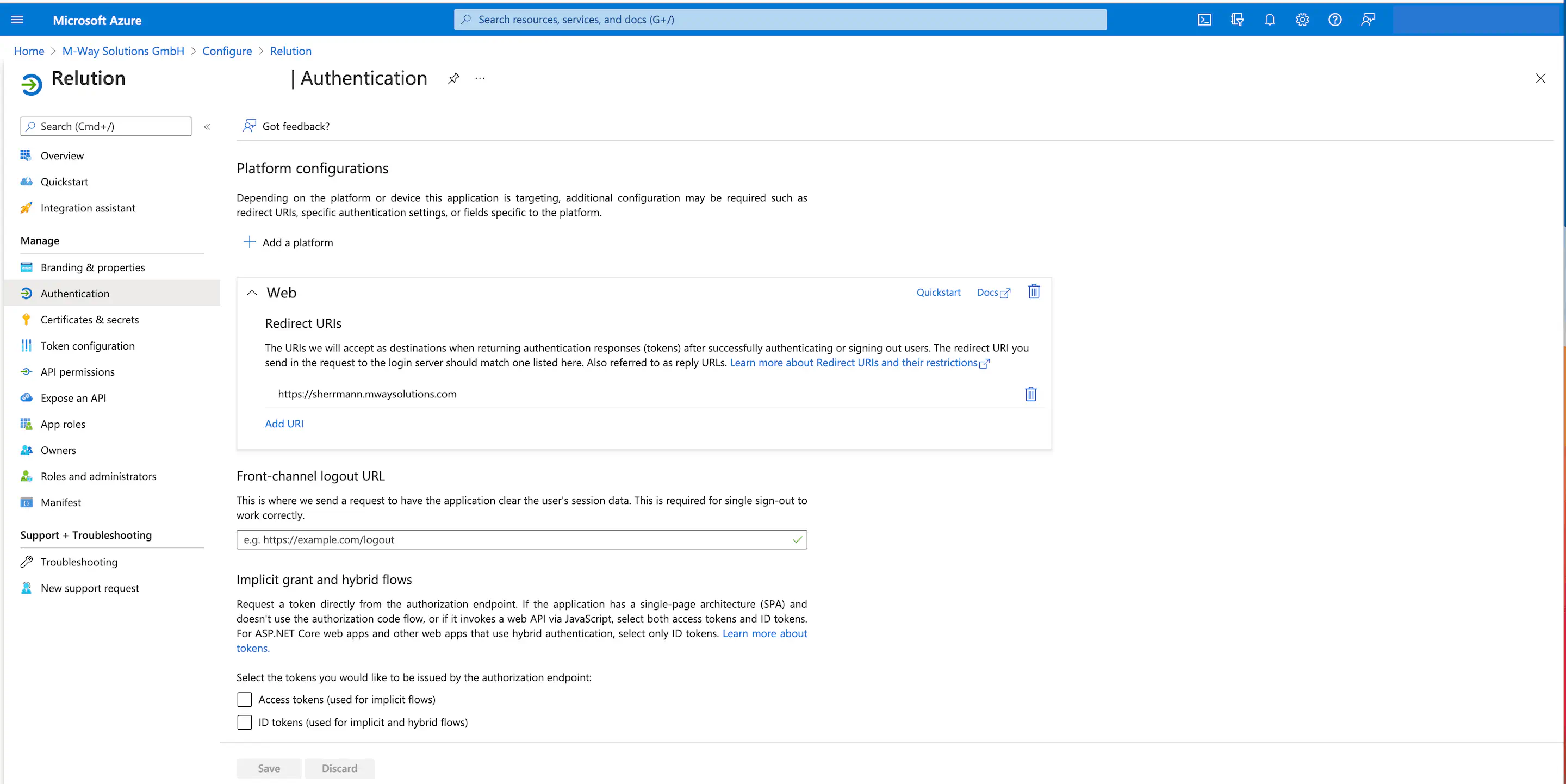
Review the Azure default settings and complete the setup
Under Devices > Device Settings, the following items must be configured:
- All users are allowed to mount devices in
Azure AD. - All users are allowed to register their devices to Azure AD.
- Maximum number of devices per user should be respected.
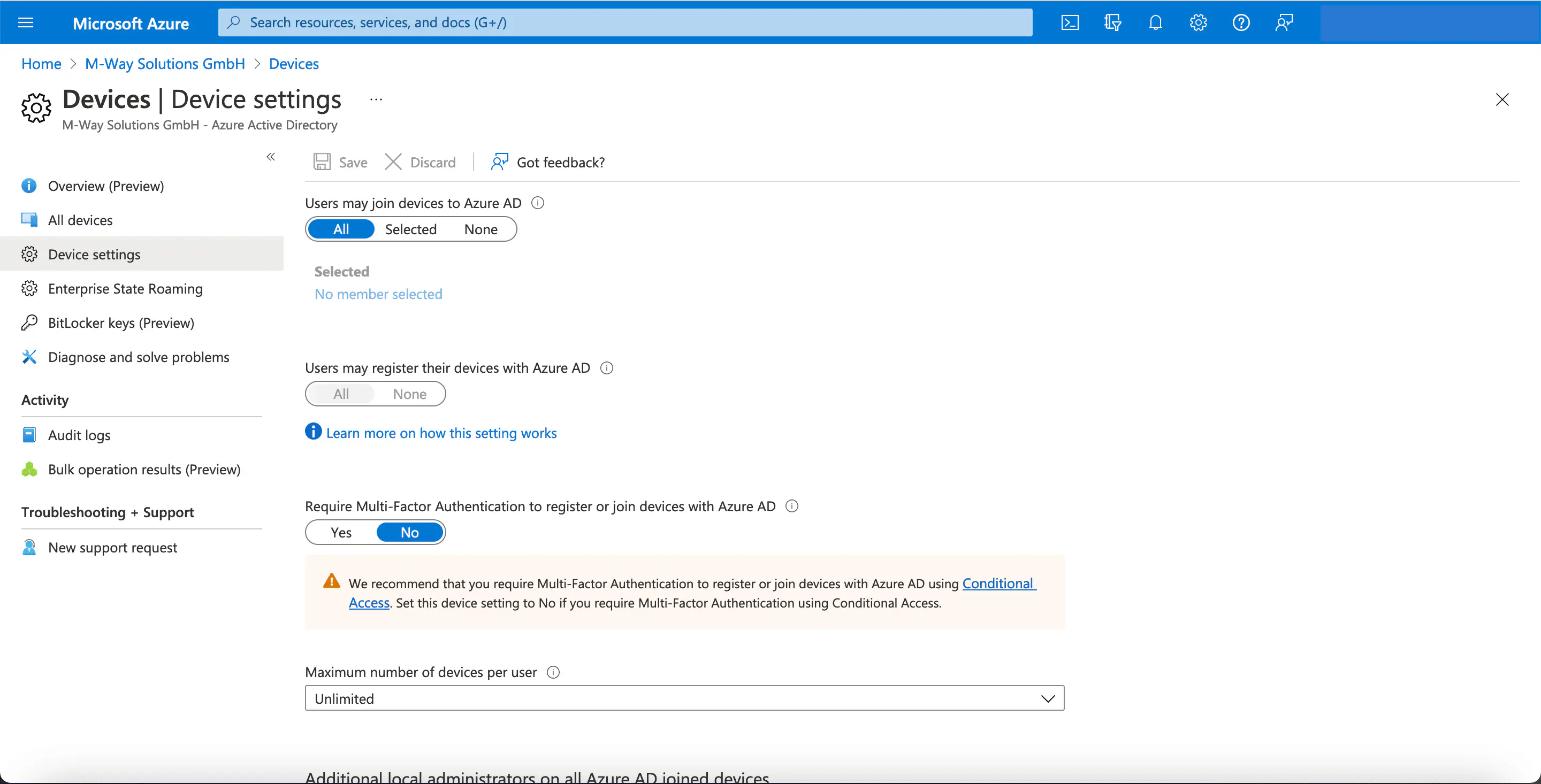
This completes the setup in Azure.
Selecting the Relution service options and completing the setup
In the Relution instructions, in step 5, you can still optionally choose whether Azure AD users and Azure AD groups should be synchronized with Relution:
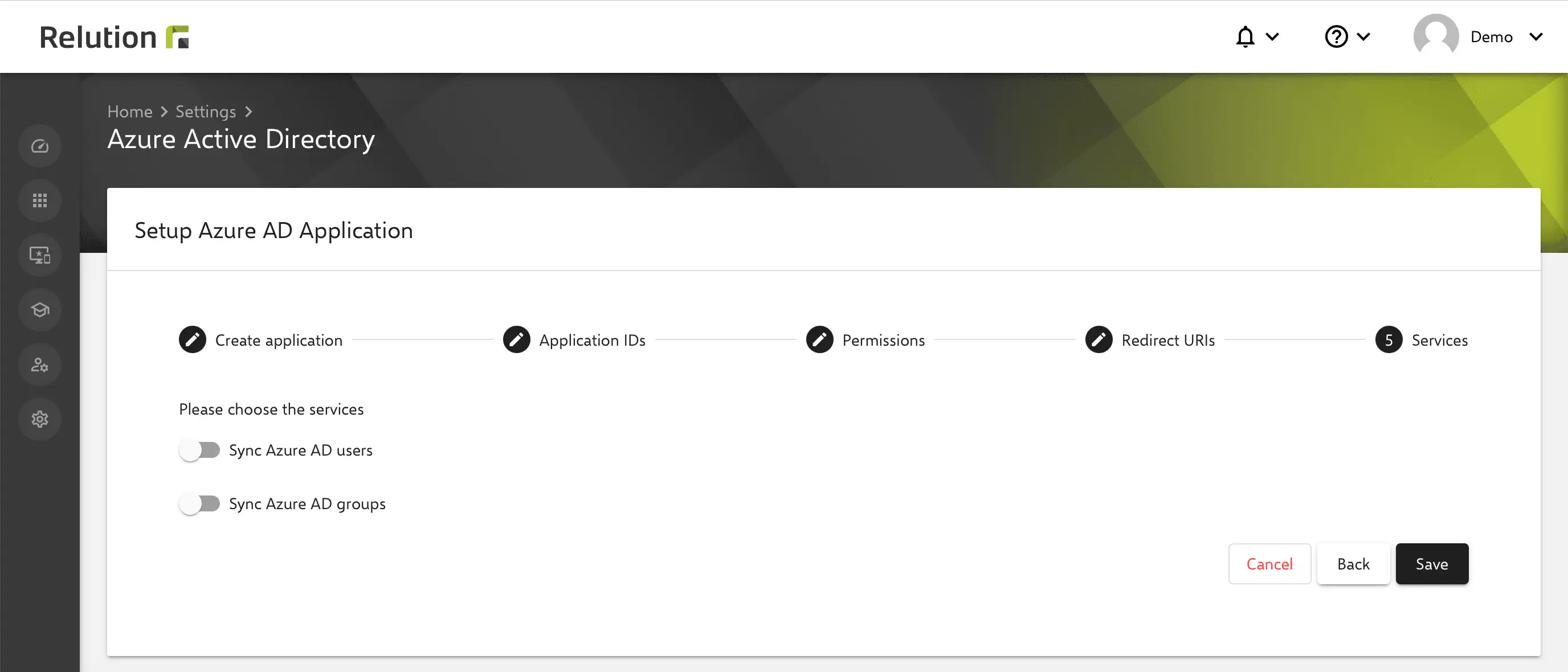
Clicking Save completes the setup and linking of Azure AD in Relution.
Adding Windows 10/11 devices
These steps replace the steps previously required in the Microsoft Store for Business.
New devices can be procured and registered via a partner. In this way, the devices are automatically stored in the Intune portal and in Azure AD and do not have to be entered manually.
Already enrolled devices can be added manually to the Entra Portal. You will need a CSV-file for this, which can be created with a Powershell-Script. After that, the file needs to be uploaded to the Intune Portal. https://intune.microsoft.com
The file can be created with this Powershell-Script:
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
New-Item -Type Directory -Path "C:\HWID"
Set-Location -Path "C:\HWID"
$env:Path += ";C:\Program Files\WindowsPowerShell\Scripts"
Set-ExecutionPolicy -Scope Process -ExecutionPolicy RemoteSigned
Install-Script -Name Get-WindowsAutopilotInfo
Get-WindowsAutopilotInfo -OutputFile AutopilotHWID.csv
Powershell needs to be executed as administrator.
In the Azure Portal you have to switch to Devices > Search for Enrollment and select it > Scroll down on the right window > select Devices. Hit the Import button and upload the file.
Preparation of the Out Of The Box Experience (OOBE) at Microsoft
A profile must now be created.
To do this, switch back to the function finder. Click on Devices on the left > Enter ‘Registration’ in the search > Scroll all the way down on the right > Click on ‘Deployment profiles’.
- Click
Create profile. - Select
Windows PC. - Enter a name.
- Click
Next. - Click
Next. - Select
Add groupsorAdd all devices. - Click
Next. - Click
Create.
The devices are now connected to the profile.
Synchronize stored Windows 10/11 devices in Relution
Under Devices > Auto Enrollment, the Windows 10/11 devices are added to Relution via the Synchronize button. The devices must not be enrolled at this time.
Only when Windows 10/11 device appear in the overview, an automatic enrollment via Windows Autopilot can be performed.
Automatic enrollment of Windows 10/11 devices in Relution
After resetting the devices or during initial startup, the network connection is established in the OOBE. Once this is done, the devices communicate with Azure and download the Autopilot profile.
The log in screen for the Microsoft account then appears. After users enter their credentials, communication with Relution takes place. The Terms of Use endpoint is called first, and then enrollment in Relution takes place.
If the users are enrolled in Relution and there are auto-enrollments for the devices, the enrollments are performed. Then the Windows 10/11 devices appear in the device inventory of the corresponding Relution organization and can be further configured via Windows policy configurations and actions.
Please do not delete the account on the device with which the device was registered.