Create MSIX files
Introduction
The MSIX format is a Windows app package format used to create and distribute applications in Windows 10/11. These MSIX files are usually not available via a simple download, as they need to be certified and “repackaged” before being installed on Windows devices.
MSIX Packaging Tool
The creation of MSIX files requires the MSIX Packaging Tool, which can be downloaded from the Microsoft Store → and installed on a Windows device.
Certificate creation
The next step is to create a certificate. This can be done comfortably via the Powershell. To do this, change the name of the certificate and/or the password if necessary.
# Generate a new self signed certificate with the subject 'CN=Relution', the key algorithm RSA,
# the key length 2048, the key usage DigitalSignature and the type CodeSigningCert and save it in the personal
# in the personal certificate store of the current user
$Newcert = New-SelfSignedCertificate -Subject 'CN=Relution' -KeyAlgorithm RSA -KeyLength 2048 -KeyUsage DigitalSignature -Type CodeSigningCert -CertStoreLocation Cert:\CurrentUser\My
# Get the thumbprint of the newly generated certificate
$trumbprint = $Newcert.Thumbprint
# Get the certificate object from memory by its thumbprint
$cert = (Get-ChildItem -Path cert:\CurrentUser\My\$trumbprint)
# check if the certificate was retrieved successfully
if($cert -ne $null){
# convert the plaintext password string to a secure string
$Secure_String_Pwd = ConvertTo-SecureString "Passw0rd" -AsPlainText -Force
# Export the certificate to a PKCS#12 file on the user's desktop
Export-PfxCertificate -Cert $cert -FilePath $env:USERPROFILE\desktop\MSIXZertifikat.pfx -Password $Secure_String_Pwd
# Remove the certificate from memory
Remove-Item cert:\CurrentUser\My\$trumbprint
}
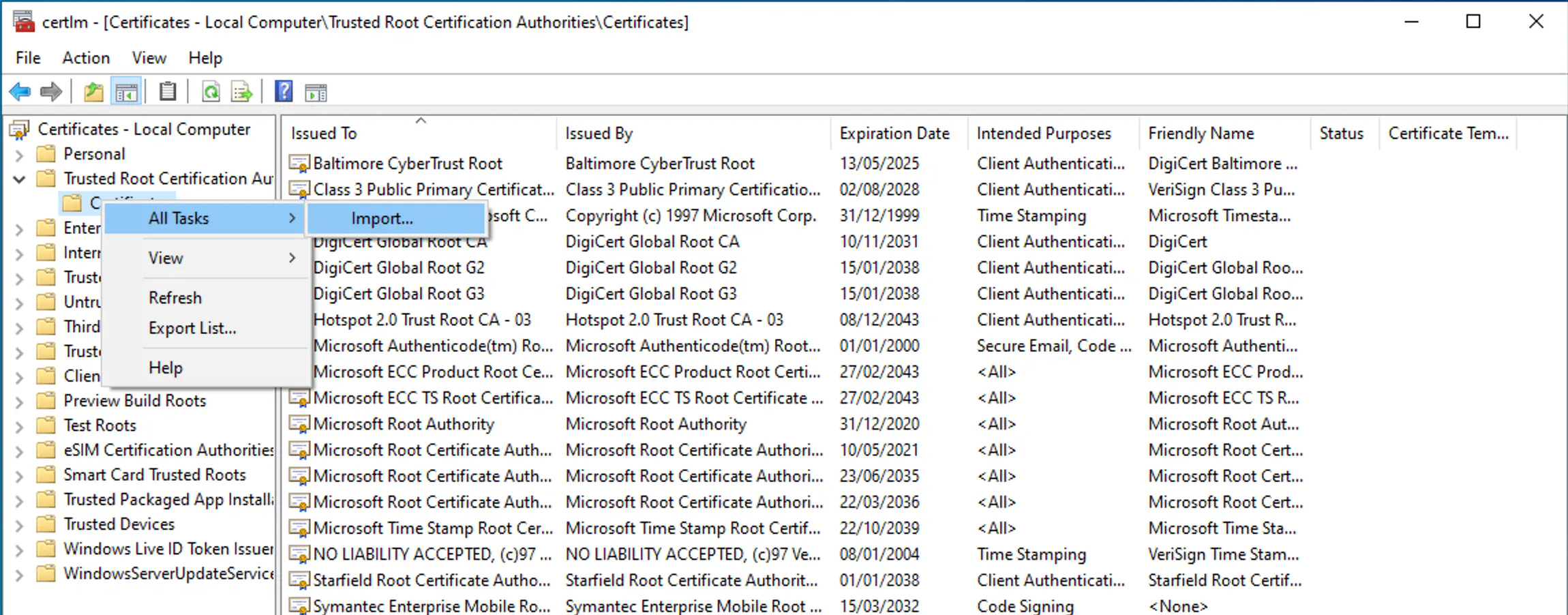
The created certificate must be stored in the Trusted Root Certification Authorities category on all Windows 10/11 devices where MSIX files are to be installed. This can be done either with Relution via the policy configuration Certificates or manually, directly on the devices. The password string in the example is passw0rd. To add the certificate manually, start the certificate management Manage Computer Certificates as an administrator.
Creation of MSIX files
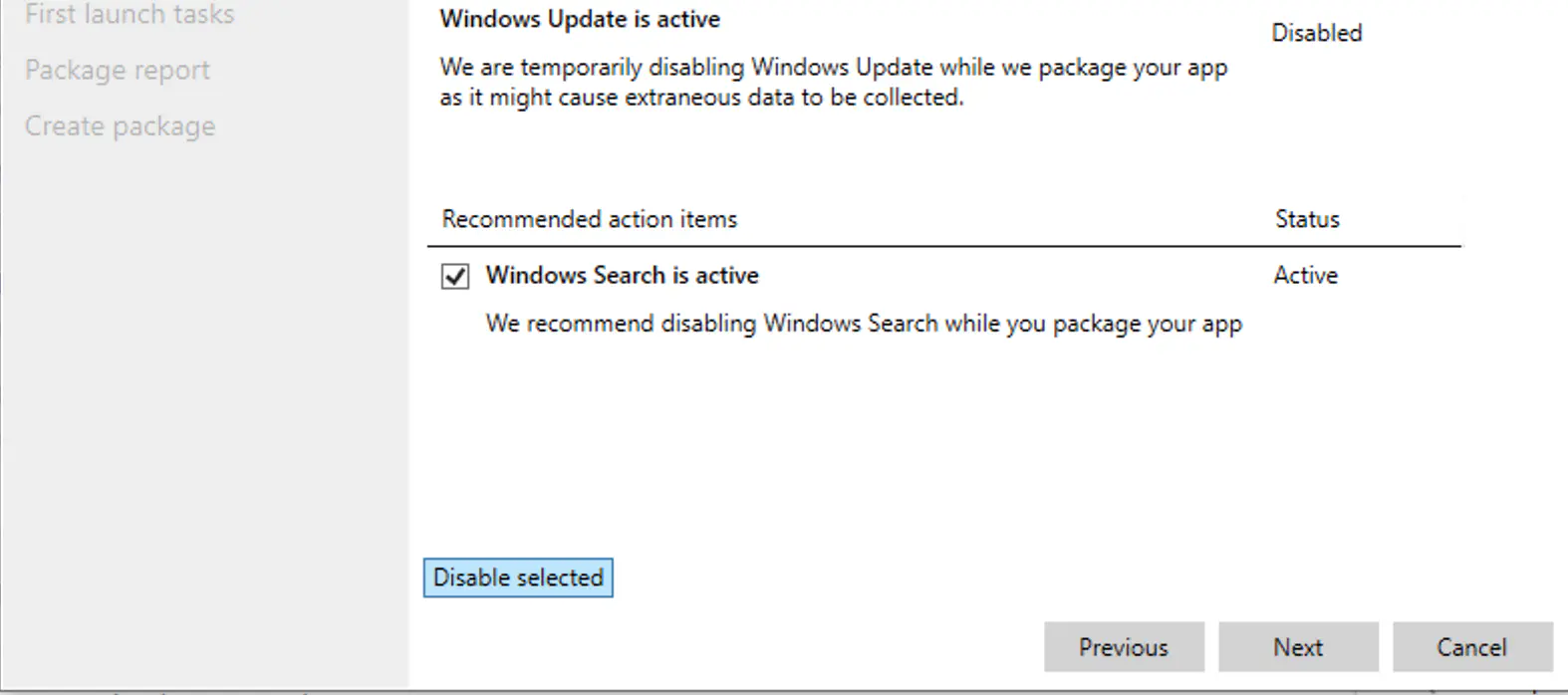
Start the MSIX Packaging Tool and select the option to create a new app package. Uncheck Windows Search is active in the following dialogue.
In the example, we create a MSIX file for Notepad++. First, a setup file has to be downloaded. Then a file and the certificate in the MSIX Packaging Tool have to be selected. The Signature Preference must be set to Sign with a certificate (.pfx).
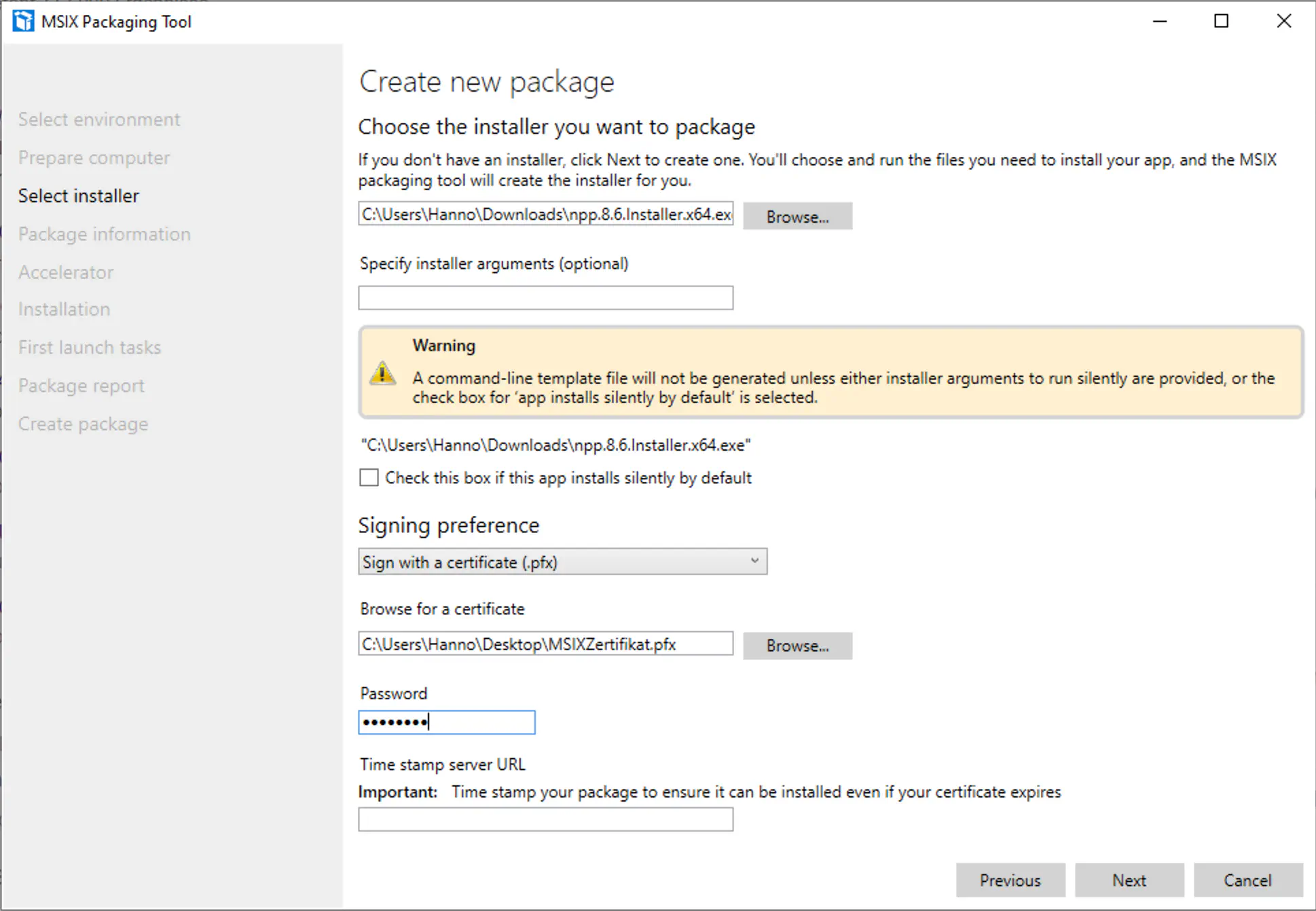
The appropriate fields have to be filled in.
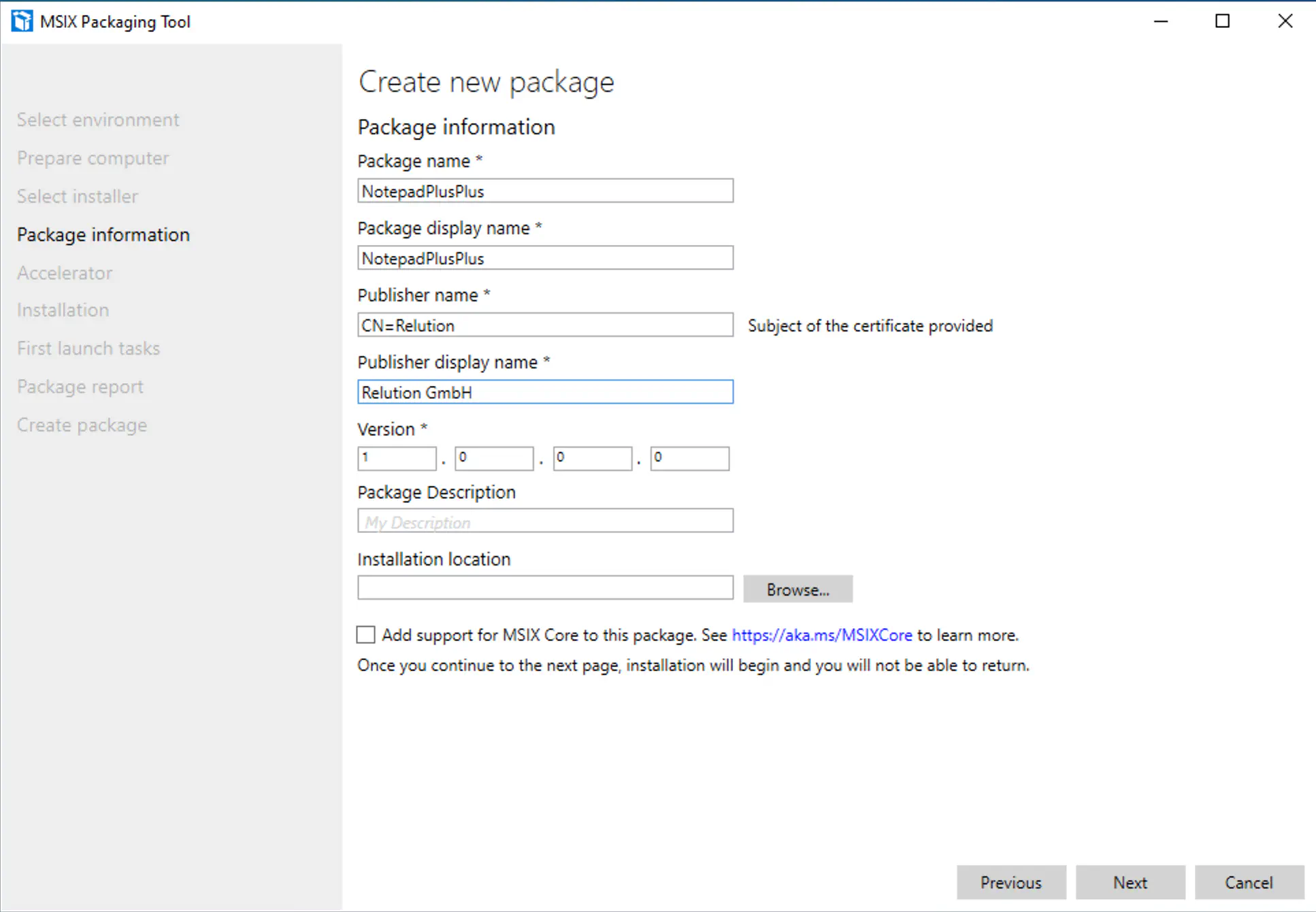
Now, the installer of Notepad++ starts. It should be run normally and the configurations have to be set according to the needs.
In the MSIX Packaging Tool click on Next and Yes, continue when the installation of Notepad++ is finished.
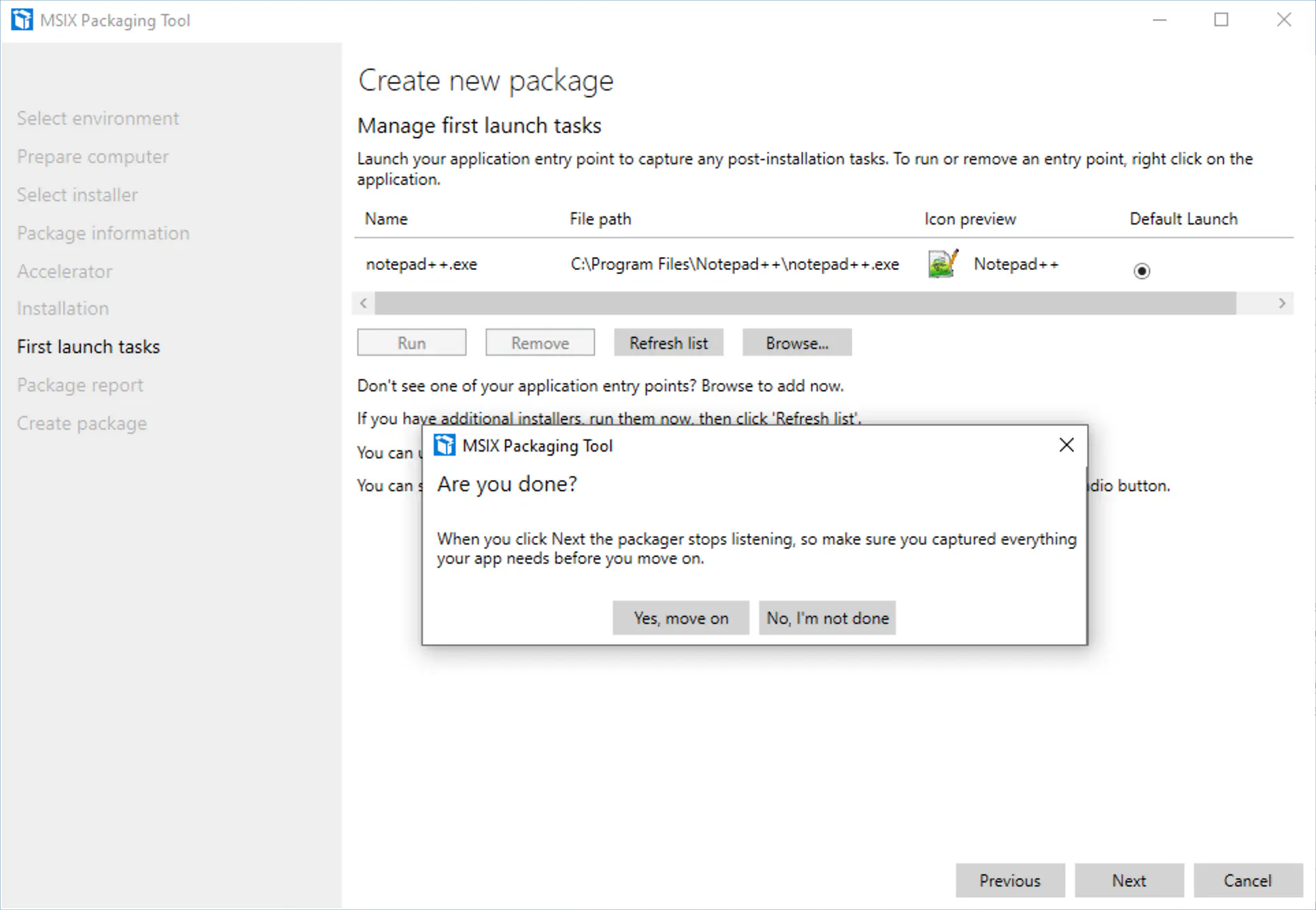
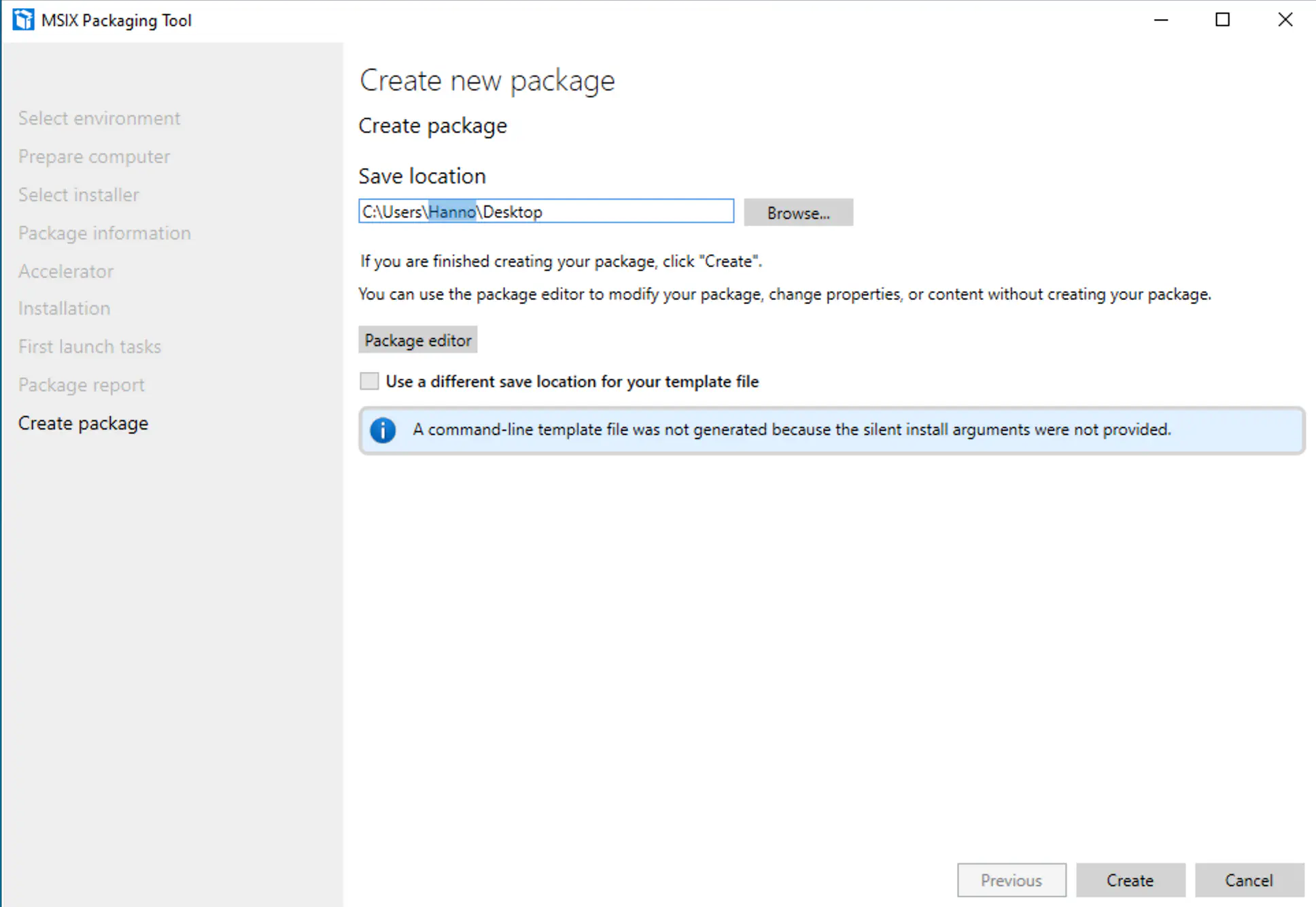
The tool will indicate that no services have been installed and detected. In the last dialog box you can specify the location of the package. Finish the creation by clicking Create.
Deploy certificate on other Windows PCs
In order to be able to install the MSIX package on other Windows PCs, the certificate must be provided on these. To do this, the certificate must be converted from a PKCS12 to a PKCS1 certificate using openSSL. To do this, openSSL must be installed on the system. This works with this command:
openssl pkcs12 -in MSIXZertifikat.pfx -clcerts -nokeys -out MSIXZertifikat.der
The PKCS1 certificate that has just been converted can then be uploaded to Relution under Settings > Certificates.
Finally, the certificate must be delivered to the devices in a policy for Windows devices. To do this, the “Certificates” configuration must be used and the certificate selected.
It is mandatory to select ‘Trusted root certificate authority’ as the certificate store.