App Control
Introduction
With version 5.24.0 the configuration App Control has been introduced. With this feature, you can apply Windows Defender Application Control (WDAC) policies to Windows devices. These policies define which applications are trusted, allowing only those trusted applications to run on the device.
Microsoft provides all necessary information for WDAC policies in their documentation.
WDAC policy generation
Microsoft explains the design and creation of WDAC policies in their design guide.
It is recommended to thoroughly test any WDAC policies before deploying them to production devices via Relution.
It must be ensured that the Relution Windows Companion application is not blocked or restricted by the defined rules.
Create the needed WDAC policy file
For the generation the WDAC Wizard and the example base policies can be used.
The Windows Defender Application Control (WDAC) Policy Wizard generates two configuration files when used for policy generation: an XML file and a CIP file. However, these two files cannot be directly used in Relution because the MDM interface of Microsoft requires a binary file. The process of creating this binary file from the XML file is explained in the following sections.
Xml file
The WDAC policy xml file contains two pieces of information that are critical to successfully applying the configuration to the Windows devices via Relution.
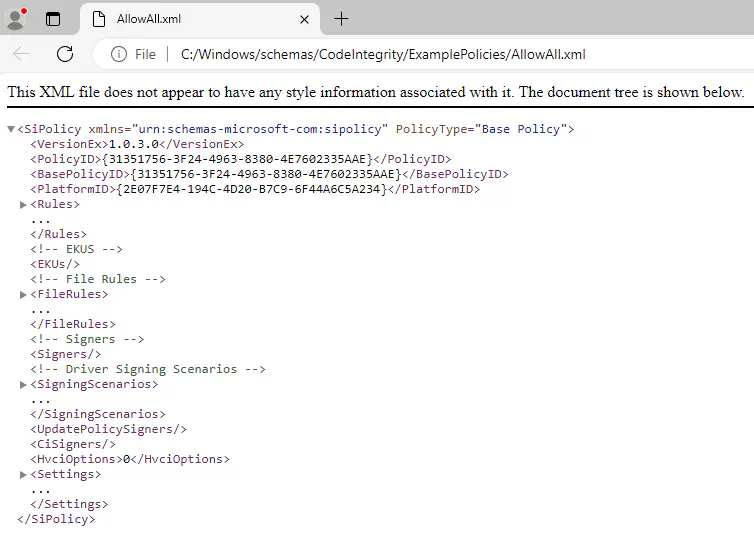
The <PolicyID> is a GUID that uniquely identifies this WDAC policy. It is therefore used for applying, updating and deleting the configuration.
The <VersionEx> is used as versioning for the WDAC policy. Therefore, for updates to a WDAC policy, the version must not be less than the previously applied version. Otherwise the update of the configuration via Relution will fail.
Convert the xml file
The xml file must be converted into a binary file. This can be done using the ConvertFrom-CIPolicy PowerShell command.
Example:
ConvertFrom-CIPolicy -XmlFilePath .\AllowAll.xml -BinaryFilePath .\AllowAll.bin
The resulting binary file can be uploaded to Relution in the application control configuration.
App Control configuration
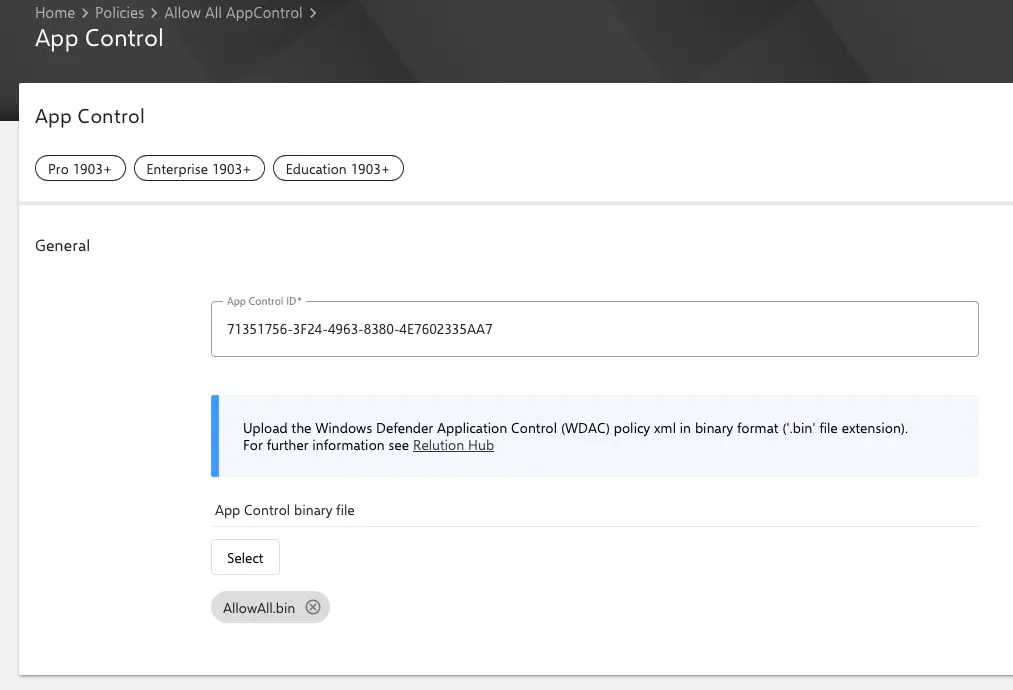
The application control configuration consists of two fields:
- A button to upload the WDAC policy file in binary format, see WDAC policy generation
- A field for entering the
App Control ID. For the configuration to be successfully applied to the device, theApp Control IDmust contain the same value as the<PolicyID>from the WDAC policy. But without the curly brackets.- Example:
- PolicyID in WDAC policy:
<PolicyID>{31351756-3F24-4963-8380-4E7602335AAE}</PolicyID>
- PolicyID in WDAC policy:
- App Control ID in configuration:
31351756-3F24-4963-8380-4E7602335AAE - It is not possible to change the entered
App Control IDafter saving for the first time. However, it is possible to create several (complementary) application control configurations and apply them to one device.
- Example:
Update
In order for a new version of the Application Control configuration to be successfully applied to the device, the <PolicyID> in the WDAC policy must have the same value as the App Control ID of the configuration and the <VersionEx> must have a value higher than in the previous version.
Delete
In order for deleting a WDAC policy to be applied to the device, a device restart is required.
Microsoft recommends a workaround so that the app restrictions are removed without restarting, see Microsoft documentation.
Delete an unsigned application control configuration
In Relution, removal without restarting can be implemented as follows:
- Create an Allow-All WDAC policy
- The
<PolicyID>must match the App Control ID - The
<VersionEx>must be higher than the previous version
- The
- Convert the xml file into the required binary format
- Create a new policy version in Relution
- Upload the new binary file of the Allow-All WDAC policy to the app control configuration
- Publish the new policy version
- This will remove the existing restrictions from the device
- Remove the policy from the device
- This deletes the application control configuration from the device. However, this is only active after the restart.
Delete a signed application control configuration
Removing a signed WDAC policy (without requiring a restart) can therefore be implemented in Relution as follows:
- Create a signed WDAC policy that allows unsigned WDAC policies
- The
<PolicyID>must match theApp Control ID - The
<VersionEx>must be higher than the previous version
- The
- Convert the xml file into the required binary format
- Create a new policy version in Relution
- Upload the new binary file of the Allow-All WDAC policy to the app control configuration
- Publish the new policy version
- This allows unsigned WDAC policies to be applied on the device
- Delete an unsigned application control configuration